Mustang Panda is a sophisticated Chinese state-aligned cyberespionage group active since at least 2012. The group primarily targets government agencies, NGOs, think tanks, religious organizations, and private companies with geopolitical relevance to China’s strategic interests. Mustang Panda is known for its strong focus on Southeast Asia, the European Union, and organizations involved in human rights or regional policy.
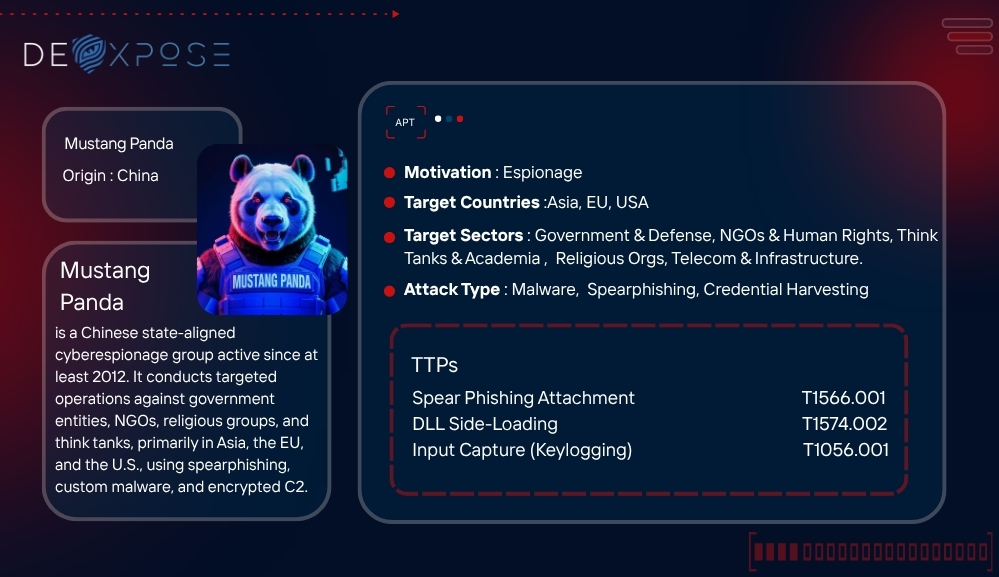
Mustang Panda campaigns are characterized by strategic spearphishing using themed lures, DLL sideloading, custom malware, encrypted C2 communications, all targeting entities of strategic relevance to the People’s Republic of China (PRC).
The group’s sophistication lies not in zero-day exploits but in its ability to craft highly tailored lures, evade detection, and operate with geopolitical intent.
Over the years, Mustang Panda has been tracked under various names by cybersecurity vendors, reflecting different observations of its operations across campaigns and infrastructure.
Known aliases include:
Hive0154, BASIN, BRONZE PRESIDENT, Earth Preta, HoneyMyte, LuminousMoth, Polaris, Red Lich, Stately Taurus, TA416, TANTALUM, TEMP.HEX, Twill Typhoon, Red Delta, Camaro Dragon.
Adversary Focus Areas
Who They Target?
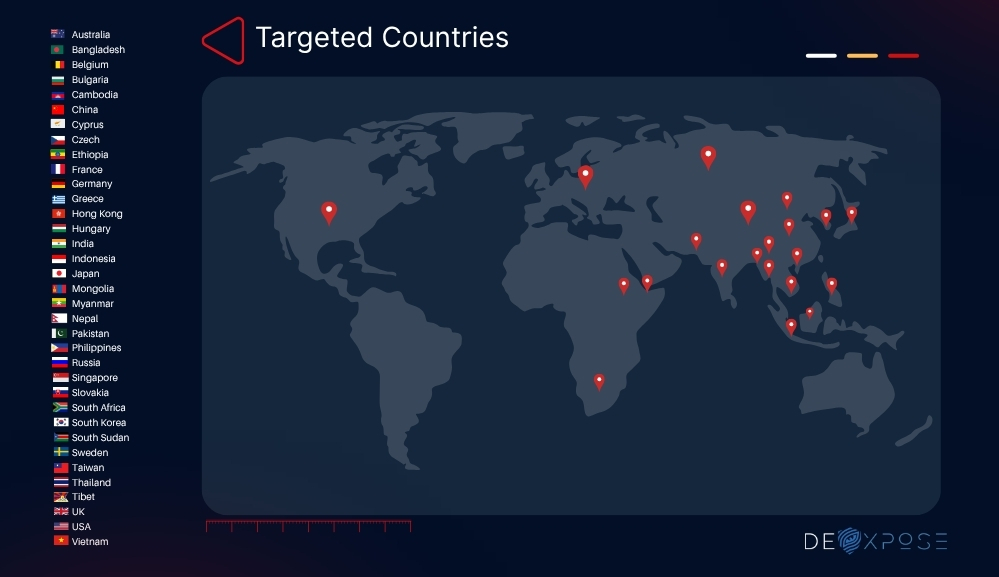
Mustang Panda’s targeting is tightly aligned with the strategic, diplomatic, and ideological objectives of the Chinese state. Over the years, the group has launched campaigns across Asia, Europe, Africa, and North America. Their operations consistently focus on nations, sectors, and communities that intersect with Beijing’s geopolitical interests.
Targets have included Australia, Bangladesh, Belgium, Bulgaria, Cambodia, China, Cyprus, Czech, Ethiopia, France, Germany, Greece, Hong Kong, Hungary, India, Indonesia, Japan, Mongolia, Myanmar, Nepal, Pakistan, Philippines, Russia, Singapore, Slovakia, South Africa, South Korea, South Sudan, Sweden, Taiwan, Thailand, Tibet, UK, USA, and Vietnam.
Targeted Sectors
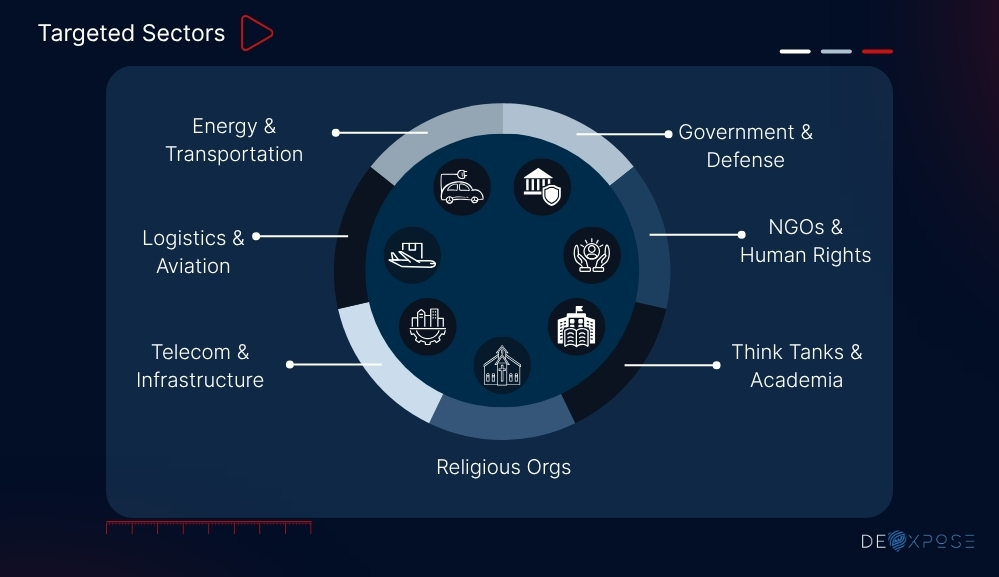
Mustang Panda has consistently pursued entities aligned with China’s strategic, political, and ideological interests. The group’s targets span government, civil society, defense, and critical infrastructure sectors, often chosen for their geopolitical sensitivity or policy relevance.
Primary Target Categories:
Government Agencies: Ministries of Foreign Affairs, Defense, and Interior; diplomatic missions; intelligence services.
Military & Defense
Non-Governmental Organizations (NGOs): Human rights, pro-democracy, and advocacy groups focused on China-related issues.
Religious Institutions
Think Tanks
Telecom and Infrastructure
Educational Institutions
Logistics & Aviation
Energy & Transportation
Tactics & Tradecraft
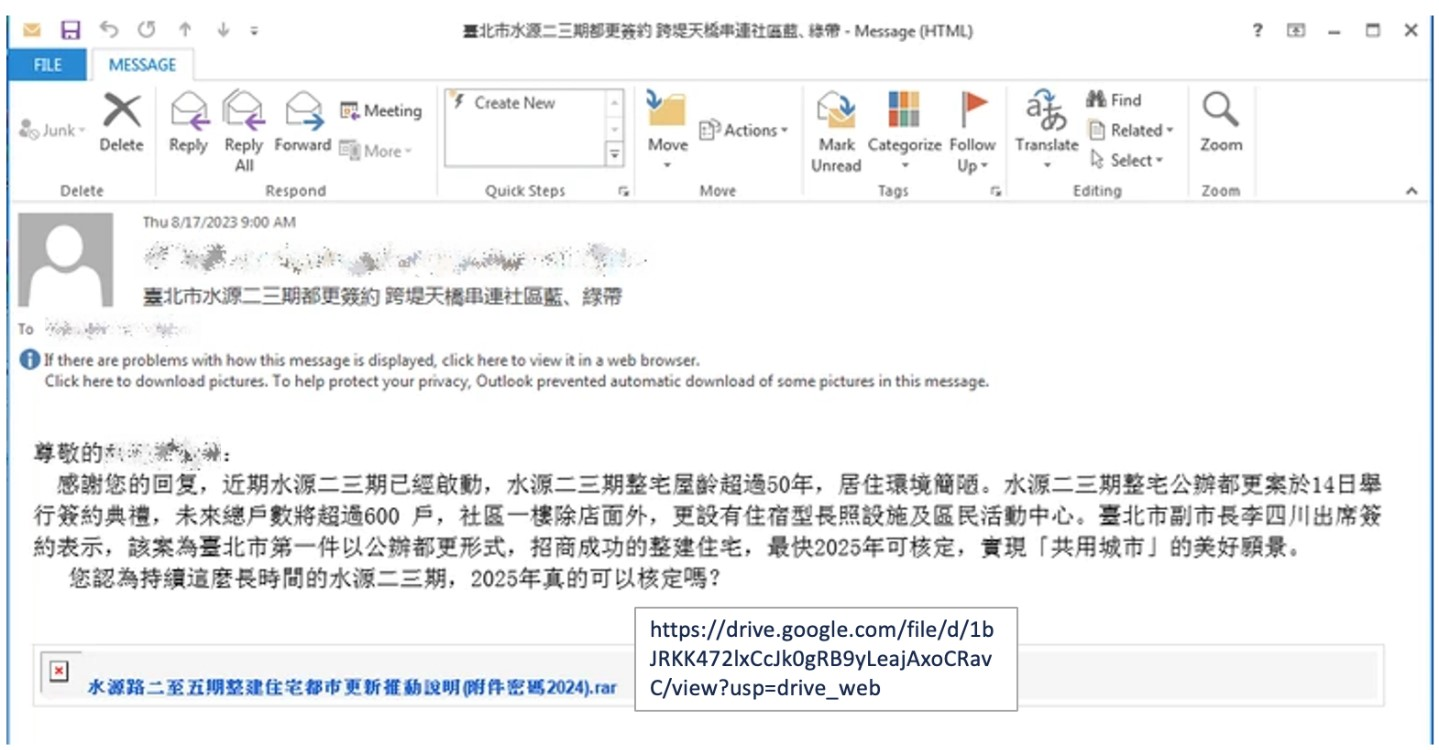
Mustang Panda typically initiates access through spear-phishing attachments containing ZIP, RAR, or LNK files, often themed around politically charged topics like Tibetan events or diplomatic agreements [T1566.001].
In air-gapped or less secure environments, the group has also relied on removable media propagation using the HIUPAN worm to deliver payloads via USB drives [T1091].
Execution is primarily handled via DLL side-loading [T1574.002], leveraging legitimate signed binaries to sideload malicious loaders like Claimloader and ToneShell. Once deployed, Mustang Panda uses DLL injection to load payloads directly into memory [T1055.001].
For persistence, the group favors simple but effective techniques like scheduled task creation [TA0002] and service registration [T1569.002], often implemented in tools like CorKLOG and SplatCloak. These allow long-term footholds even after reboots or security scans.
Mustang Panda’s privilege escalation techniques include token manipulation to create processes under the context of more privileged users [T1134.002]. This is especially prominent in advanced payloads like ToneShell.
Once inside a system, the group conducts discovery by enumerating user accounts [T1087] and system information to support further lateral movement. Tools such as StarProxy facilitate internal C2 routing, allowing compromised hosts to act as relays [T1090.001].
To evade detection, Mustang Panda applies a layered approach. Payloads use custom encryption schemes like XOR or RC4 for C2 traffic [T1573.001], often tunneled through encrypted channels using FakeTLS headers, and further obscured through protocol impersonation [T1001.003]. This blends malicious traffic with normal encrypted sessions, defeating traditional network monitoring [TA0005].
Advanced evasion also includes disabling kernel-level callbacks in EDR products using the custom driver SplatCloak [T1562.001], file deletion post-execution [T1070.004], and obfuscation of code and API resolution through techniques like control flow flattening and DJB2-based hashing [T1027, T1027.007].
Data collection efforts involve keylogging [T1056.001] and clipboard monitoring [T1115] via PAKLOG and CorKLOG, with logs stored locally, encrypted and later exfiltrated.
Their overall command-and-control infrastructure is highly flexible. Both ToneShell and StarProxy establish communication with attacker-controlled servers [TA0011]. These channels are typically encrypted using custom XOR and FakeTLS, enabling stable and stealthy communication that can switch endpoints or protocols as needed.
Abuse of Visual Studio Code
Stately Taurus (aka Mustang Panda) has been observed leveraging an unconventional attack vector by abusing Visual Studio Code’s tunneling feature to gain remote access to targeted Southeast Asian government environments.
The attacker used code.exe tunnel to establish an OAuth-authenticated remote session via GitHub, granting full terminal and file system access through a browser-based VS Code environment. Persistence was achieved via a scheduled task executing startcode.bat at system startup, effectively reestablishing the reverse shell on reboot.
This campaign is linked to prior activity involving ToneShell and ShadowPad, tied together through shared TTPs and a unique 13-character archive password. Stately Taurus maintained access using scheduled tasks and deployed tools like sshd.exe, SharpNBTScan, Listeners.bat, and rar.exe for lateral movement, data staging, and archival.
The attackers exfiltrated data stealthily using Dropbox via curl, while credential theft involved tools such as Mimikatz, LaZagne, In-Swor, and custom LSASS dumpers. The group also attempted to steal NTDS.dit using Volume Shadow Copy.
ShadowPad was deployed via DLL sideloading through imecmnt.exe and maintained persistence using renamed services.
Bypassing EDR at the Kernel Layer
Mustang Panda’s recent toolkit includes SplatCloak, a custom kernel-mode driver delivered via the SplatDropper utility.
Once deployed, it operates at the kernel level to deliberately disable notification callbacks associated with Windows Defender and Kaspersky security products, effectively neutralizing EDR hooks tied to process, thread, and image creation
SplatDropper itself is a self-cleaning sideloading dropper: it uses a signed executable to sideload a malicious DLL which installs the driver, then deletes itself to minimize forensic traces.
The SplatCloak driver employs advanced obfuscation techniques, such as control flow flattening and mixed boolean arithmetic, to resist reverse engineering.
Rather than relying on static API hashes, it resolves required kernel functions dynamically by parsing system module information and using system call routines like ZwQuerySystemInformation and MmGetSystemRoutineAddress
Once loaded, the driver specifically targets callback lists for core kernel events (PspCreateProcessNotifyRoutine, PspCreateThreadNotifyRoutine, and PspLoadImageNotifyRoutine) registered by Defender and Kaspersky drivers such as wdfilter.sys, wdboot.sys, and wdnisdrv.sys.
These callbacks are either disabled or entirely removed based on driver name comparisons, effectively disabling behavioral detection and blocking of future malware executions or injections.
Mustang Panda Malware & Toolset
Mustang Panda maintains a diverse and evolving arsenal of custom malware, open-source tools, and modified payloads tailored for espionage, persistence, and lateral movement. The group frequently relies on multi-stage infection chains involving loaders, encrypted communications, and modular backdoors to maintain long-term access in target environments. Many of their tools are deployed via DLL sideloading techniques and are designed to evade detection through obfuscation, encryption, and stealthy execution.
Claimloader / Pubload / Pubshell
- Claimloader serves as the first-stage stager, typically deployed within malicious ZIP/RAR archives distributed via spear‑phishing campaigns.
- Upon execution, the signed benign binary sideloads the Claimloader DLL, which decrypts and injects the Pubload downloader into memory. Pubload immediately reaches out to the attacker-controlled C2 infrastructure to retrieve Pubshell.
- Pubshell is a lightweight reverse‑shell backdoor that provides interactive command execution, typically spawning cmd.exe within an anonymous pipe environment. Pubshell mirrors its reverse‑shell functionality, requiring additional commands to return output.
ToneShell
Mustang Panda’s primary second-stage backdoor, widely deployed in Myanmar and beyond. Installed via DLL sideloading, it supports payload execution, C2 communication using FakeTLS encryption, dynamic API resolution, token-stealing, DLL injection, and stealth features like file deletion post-execution.
StarProxy
Lateral movement tool that tunnels and proxies C2 traffic between compromised hosts. Delivered alongside ToneShell, it uses FakeTLS-like encrypted channels and enables internal routing of commands to evade detection.
PAKLOG & CorKLOG
PAKLOG is a keylogger that captures keystrokes and clipboard data, encoding logs with a custom character scheme for obfuscation.
CorKLOG extends this by encrypting logs with a 48-character RC4 key and providing persistence via scheduled tasks or services.
SplatCloak
A kernel-mode EDR evasion driver deployed via SplatDropper.
It disables monitoring callbacks from Windows Defender and Kaspersky, using control flow flattening and obfuscated boolean logic to thwart analysis and detection.
Hiupan Worm (a.k.a. USB Worm)
Self-replicating malware spread via USB drives.
It installs Pubload via DLL sideloading once executed, enabling Mustang Panda to cross air-gapped networks or offline systems via removable media.
MQsTTang
A lightweight custom backdoor using MQTT (a messaging protocol typical for IoT devices) for command-and-control.
Identified in European political campaigns.
FDMTP & PTSOCKET
- Tools used in conjunction with Pubload to exfiltrate targeted documents (DOC, PDF, PPT formats) via network channels; associated with earlier APAC campaigns
PlugX
- A longstanding RAT delivered via DLL sideloading. Extensively used for command execution, plug-in deployment, and persistence. Attributed to infections on over 4,000 systems in a U.S.–France coordinated operation. Linked to broader Chinese state-aligned APT operations.
In addition to its core toolset, Mustang Panda has also been observed leveraging other malware families, including Poison Ivy, DOPLUGS, Horse Shell, WispRider, and Sogu.
Exploited Vulnerabilities
The group often exploits public vulnerabilities to gain initial access, particularly those affecting Microsoft Office and Windows components.
These vulnerabilities are often incorporated into phishing campaigns, embedded within weaponized documents or used in exploit chains that lead to the execution of loaders and backdoors such as Claimloader, Pubload, and ToneShell.
Known CVEs exploited by Mustang Panda include:
CVE‑2017‑0199 – A remote code execution vulnerability in Microsoft Office that allows attackers to execute code via specially crafted RTF or Word documents.
CVE‑2021‑1675 / CVE‑2021‑34527 (“PrintNightmare”) – A pair of vulnerabilities affecting the Windows Print Spooler service, enabling remote code execution and local privilege escalation. Mustang Panda has used these to escalate privileges once inside a system.
CVE‑2021‑40444 – A remote code execution vulnerability in the MSHTML (Trident) engine, triggered via malicious ActiveX controls embedded in Microsoft Office documents. This exploit allows attackers to compromise systems through specially crafted Office files.
Notable Campaigns by Mustang Panda
1. Hive0154 Campaign Targeting the Tibetan Community (2025)
In June 2025, the China-aligned threat group Hive0154 (aka Mustang Panda) launched a targeted phishing campaign on the Tibetan community, timed around significant events such as the Dalai Lama’s 90th birthday and the 9th World Parliamentarians’ Convention on Tibet held in Tokyo from June 2 to 4.
The attackers distributed spear‑phishing emails containing Google Drive links that downloads weaponized ZIP/RAR archives.
The infection chain began with a benign Word file and legitimate-seeming content mixed with a malicious executable, which used DLL sideloading to launch the custom Claimloader stager.
Claimloader then decrypted and dropped the Pubload downloader, which in turn fetched the Pubshell backdoor to establish a reverse shell for remote access.
2. Mustang Panda’s New Arsenal: Keyloggers & EDR Evasion Tools (2025)
Between April and mid‑2025, Mustang Panda launched a sophisticated campaign targeting organizations in Myanmar. This campaign involved the deployment of new variants of the ToneShell backdoor, alongside additional tools designed for persistence, monitoring, and evasion.
ToneShell is a stealthy modular backdoor capable of dynamic payload loading, C2 switching, and defense evasion. It leverages DLL sideloading for execution.
StarProxy acts as a reverse proxy, enabling lateral movement and C2 tunneling within compromised environments. Both are delivered via decoy-laced RAR archives and use encrypted communication over HTTP(S).
PAKLOG is a user‑mode keylogger leveraging Windows APIs to capture both keystrokes and clipboard content, with data obfuscated via a custom encoding scheme and written to record.txt. It’s deployed via a legitimate, signed binary that sideloads a malicious DLL, but lacks built‑in exfiltration functionality.
CorKLOG similarly records keyboard input and clipboard data but encrypts its logs using a 48‑character RC4 key. It ensures persistence either by installing itself as a service (if run with admin privileges) or by scheduling a recurring task named TabletInputServices executing every 10 minutes. It is delivered via a RAR archive containing an executable and the malicious DLL sideloaded by the signed executable, though deployment in some cases contained an error preventing successful sideloading.
SplatCloak, delivered via a dropper (SplatDropper), is a Windows kernel driver developed to disable kernel‑level notification callbacks used by Windows Defender and Kaspersky security products. It employs obfuscation techniques such as control‑flow flattening and mixed boolean arithmetic to hinder analysis and is removed from disk before execution to evade detection.
3. USB Worm-Driven Campaign Targeting APAC Governments (2024)
In mid-2024, Mustang Panda launched an espionage campaign targeting government agencies in Myanmar, the Philippines, Vietnam, Singapore, Cambodia, and Taiwan. The campaign leveraged removable media (USB drives) as the initial infection vector, using the HIUPAN worm to self-propagate across systems and evade traditional email filtering mechanisms.
Specific targets in the campaigns included personnel across various government organizations — military, police departments, foreign affairs and welfare agencies, executive branches, and public education.
The infection chain involved staged payloads, including DOWNBAIT, PULLBAIT, and PUBLOAD, enabling in-memory execution, reconnaissance, and command-and-control communication. Once access was established, Mustang Panda deployed post-exploitation tools such as FDMTP, PTSOCKET, and CBROVER for lateral movement and data exfiltration, as well as PlugX and FILESAC for deeper persistence within target environments.
4. CL‑STA‑0044 – Southeast Asian Government Campaign (2021–2023)
Between 2021 and 2023, the Chinese state-linked APT group Stately Taurus (aka Mustang Panda) conducted a prolonged cyberespionage campaign targeting a Southeast Asian government. The group focused on stealing sensitive government data, using advanced backdoors and stealthy persistence methods.
The attackers initially deployed a custom backdoor known as ToneShell, a malware family unique to Stately Taurus. In later stages, they also used ShadowPad, a backdoor commonly associated with multiple Chinese APTs. To gain internal access and escalate privileges, they used tools like China Chopper, Impacket, and Mimikatz.
5. RedDelta Campaign Targeting Catholic Organizations (May–July 2020)
Between May and July 2020, China-linked APT group RedDelta (aka Mustang Panda) launched a cyberespionage campaign targeting the Vatican, the Catholic Diocese of Hong Kong, and other religious organizations. The attacks coincided with the expected renewal of the China–Vatican provisional agreement and used spear-phishing emails containing lure documents that mimicked official Catholic communications. Victims were tricked into opening malicious Word files or archives that used DLL side-loading techniques to deploy PlugX.
Conclusion
Mustang Panda remains one of the most persistent and strategically aligned cyberespionage groups operating on behalf of Chinese state interests. Through a continuously evolving arsenal of malware, sophisticated spear-phishing tactics, and abuse of legitimate tools and infrastructures, the group demonstrates an exceptional ability to adapt, evade detection, and maintain long-term access in targeted environments.
References
Zscaler ThreatLabz. (2024, May 14). Latest Mustang Panda arsenal: ToneShell and StarProxy (Part 1). Zscaler.
Zscaler ThreatLabz. (2024, May 16). Latest Mustang Panda arsenal: PAKLOG, CorKLOG and SplatCloak (Part 2). Zscaler.
Mühr, G., & Chung, J. (2025, June 23). Hive0154 aka Mustang Panda shifts focus on Tibetan community to deploy Pubload backdoor. IBM Security X-Force.
CYFIRMA. (2024). APT Profile: Mustang Panda.
Palo Alto Networks Unit 42. (2024, March 28). Stately Taurus attacks Southeast Asian government using legitimate software.


