Email breaches pose significant risks to personal security when unauthorized users access email accounts or sensitive data. Often, leaked credentials can end up being sold on the dark web, leading to consequences like identity theft and financial loss. Public database breaches are common as hackers exploit vulnerabilities in organizations’ software systems. To protect your data, it’s essential to use services like DeXpose for free email breach scans, which check if your information has been compromised. Additionally, employing strong passwords and being aware of phishing tactics are crucial measures you should take. Regular updates and dark web monitoring can further enhance your security against potential threats.
Understanding Email Breaches
Email breaches happen when hackers or unauthorized users access email accounts or databases containing personal information. This can lead to the theft of usernames and passwords, which are often leaked or sold on the dark web. For example, if a company’s database is hacked and your email credentials are exposed, attackers can use this information to impersonate you, access sensitive accounts, or commit fraud.
Public database breaches are a common source of these leaks. They occur when hackers exploit weak security measures or software vulnerabilities to gain access to databases. If your data is stored in a compromised database, you may not even be aware of the breach until it’s too late.
Another risk comes from infostealers, a type of malware that collects sensitive information from your device. This malware can capture keystrokes, logins, and even financial information. Once this data is collected, it is sent to attackers who can then exploit it for identity theft or financial gain.
The consequences of having your email breached can be severe. Aside from financial losses, it can lead to identity theft and unauthorized access to your accounts. Once hackers have your email credentials, they might use them to reset passwords on other services, putting even more of your personal information at risk. Regularly monitoring your email for breaches and taking proactive steps to protect your information are essential in today’s digital landscape.
Public Database Breaches and Their Risks
Public database breaches happen when hackers gain unauthorized access to databases that hold user information. These breaches can expose sensitive data like names, email addresses, and passwords. Common causes include hacking incidents, software vulnerabilities, and weak security practices by organizations. When a database is compromised, users whose information is stored there face significant risks. For instance, a breach at a popular online retailer could expose thousands of customers’ details, leading to potential identity theft or financial fraud. Furthermore, once data is leaked, it can be sold on the dark web, where cybercriminals can easily purchase it for malicious purposes. This risk highlights the importance of organizations implementing robust security measures and for users to remain vigilant about their personal information.
Infostealer Data from Compromised Devices
Infostealers are a type of malware specifically designed to gather sensitive information from infected devices. Once this malware infiltrates a device, it silently monitors user activities, capturing keystrokes and extracting data from various applications like web browsers and password managers. For example, if an infostealer infects a computer, it can record login credentials for online banking or shopping sites without the user ever knowing.
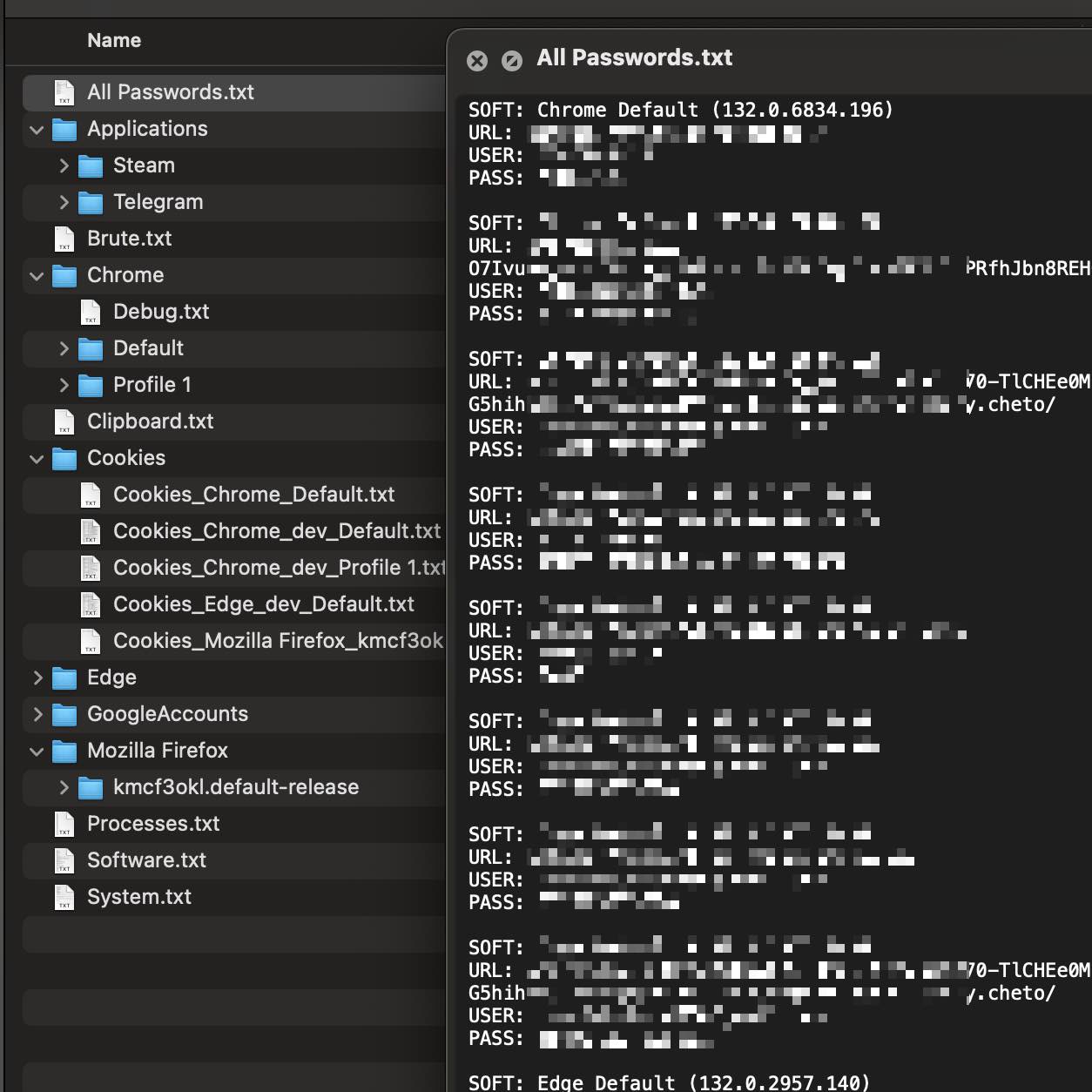
After collecting this data, the malware transmits it to cybercriminals, who can then use it for identity theft, financial fraud, or selling it on the dark web. The impact of infostealers is significant, as they can lead to severe financial loss and personal security risks.
Risks Associated with Email Breaches
Email breaches can expose your personal information, leading to significant risks. When your email credentials are compromised, attackers can gain unauthorized access to various accounts that use the same login details. This can result in financial loss, identity theft, and unauthorized transactions. For example, if your email is hacked, an attacker might reset your bank account password, locking you out and draining your funds.
Moreover, once your information is leaked, it can be sold on the dark web, where criminals purchase stolen data for malicious purposes. Users who have had their emails breached often become targets for phishing attacks, where they might receive fake emails designed to steal even more sensitive information.
The evolving nature of cyber threats means that continuous monitoring is essential. New breaches are reported frequently, making it necessary to stay vigilant. Even if you think you are safe, an old breach could resurface and put your data at risk.
Protective Measures Against Breaches
To safeguard your personal information from email breaches, start by using tools like DeXpose, which scans your email against known data breaches. This service can alert you if your credentials have been compromised, allowing you to take action swiftly. It’s also essential to create strong, unique passwords for each account. Avoid using easily guessable information such as birthdays or common words. Regularly changing your passwords can further enhance security.
Additionally, enable two-factor authentication (2FA) wherever possible. This adds an extra layer of protection by requiring a second form of verification, such as a text message or authentication app, alongside your password.
Be cautious with your personal information online. Limit the data you share on social media and be mindful of the permissions you grant to apps and websites. For instance, think twice before linking your email to less secure platforms.
Lastly, stay informed about the latest security threats. Subscribe to security newsletters or follow cybersecurity blogs. This knowledge can help you recognize potential threats early and adjust your online behavior accordingly.
| Measure | Description | Purpose |
|---|---|---|
| DeXpose Email Scan | A service to check if your email has been compromised in data breaches | Enhance awareness of potential security risks |
| Strong Unique Passwords | Implementing distinct passwords for each account | Reduce risk of credential reuse in case of breaches |
| Regular Password Changes | Changing passwords frequently to maintain security | Mitigate potential exposure from past breaches |
| Continuous Monitoring | Using services to monitor for breach alerts | Provide real-time updates on data exposure risks |
DeXpose Breach Email Scan Service
DeXpose breach email scan service is an essential tool for anyone concerned about their online security.
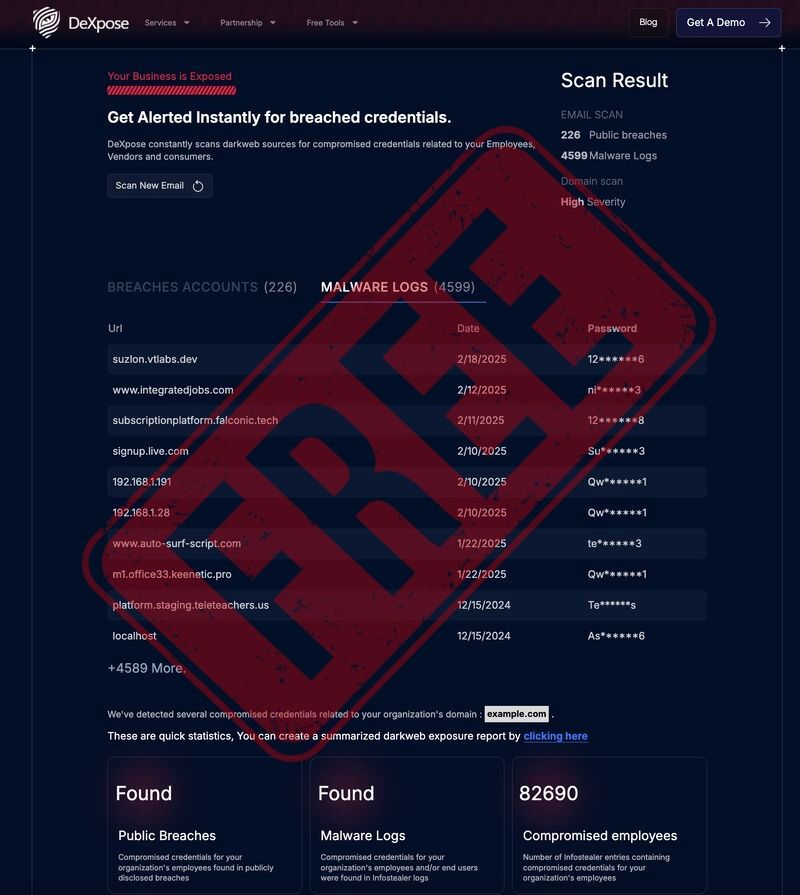
By visiting DeXpose Email Breach Scan, users can initiate a free scan of their email accounts to check for any signs of compromise. This service analyzes email addresses against a vast database of breached accounts, malware logs, and public data breaches. Once the scan is complete, users receive a detailed exposure report, which highlights any vulnerabilities and suggests actions to mitigate risks.
What sets DeXpose apart is its continuous monitoring capability. The service keeps an eye on the dark web, where stolen credentials are often traded. If any of your credentials are found in these illicit marketplaces, DeXpose alerts you in real-time, allowing you to take swift action.
This proactive approach is crucial in today’s digital landscape, where cyber threats are constantly evolving.
For example, if your email appears in a recent data breach, you can immediately change your passwords and secure your accounts, minimizing the potential for identity theft or financial loss. Utilizing DeXpose can significantly enhance your online safety and provide peace of mind.
Monitoring the Dark Web
The dark web is a hidden part of the internet where activities are often shrouded in secrecy. It is not indexed by standard search engines, making it a haven for illegal dealings, including the trade of stolen data. When your personal information is leaked from a data breach, it can end up on these dark web marketplaces, where cybercriminals buy and sell it.
For example, email addresses and passwords from a breach can be sold in bulk, allowing attackers to access multiple accounts with ease. Monitoring the dark web for your personal information is vital for early detection of potential threats.
Services like DeXpose can help identify if your email or credentials are being traded illegally, giving you the chance to take immediate action. By regularly checking the dark web, you can better safeguard your personal data and reduce the chances of falling victim to identity theft or financial fraud.
Best Practices for Online Security
To enhance your online security, start by regularly updating your software, including operating systems and applications. These updates often contain patches for security vulnerabilities that cybercriminals exploit. Next, educate yourself about phishing attacks, which can trick you into giving away personal information. For instance, be cautious of emails that ask for sensitive details or contain suspicious links. Use strong, unique passwords for each of your accounts; consider using a password manager to keep track of them. Additionally, enabling two-factor authentication (2FA) adds an extra layer of security, requiring a second form of verification beyond just your password. Lastly, consider subscribing to a dark web monitoring service. This can alert you if your personal information appears in compromised databases, allowing you to take action quickly.
- Use strong, unique passwords for all accounts
- Enable two-factor authentication whenever possible
- Regularly update your software and operating systems
- Be cautious of phishing emails and suspicious links
- Monitor your accounts for unauthorized transactions
- Use a reputable antivirus software
- Regularly review privacy settings on social media
Frequently Asked Questions
1. What is an email breach scan?
An email breach scan is a tool that checks if your email address has been part of any data leaks or hacking incidents, helping you know if your information might be at risk.
2. How does an email breach scan work?
It works by comparing your email address against lists of compromised accounts from known data breaches. If your email appears in those lists, it signals potential risks.
3. What should I do if my email is found in a breach?
If your email is found in a breach, you should change your password immediately, enable two-factor authentication, and monitor your accounts for any suspicious activity.
4. Can I prevent my email from being breached?
While you can’t fully prevent breaches, you can protect yourself by using strong, unique passwords, enabling two-factor authentication, and being cautious of suspicious emails.
5. How often should I perform an email breach scan?
It’s a good idea to perform an email breach scan regularly, such as every few months, or any time you hear about a major data breach affecting your email provider.
TL;DR
Email breaches can expose personal information, leading to identity theft and financial loss. Public database breaches and malware like infostealers heighten these risks. To protect yourself, use services like DeXpose for email breach scans, implement strong passwords, and monitor the dark web for compromised data. Regularly update your security practices and educate yourself on online threats.



