A recently observed phishing campaign impersonating Egypt Post (البريد المصري) has been attributed to the Smishing Triad, a well-documented cybercriminal group for their phishing (smishing) campaigns across multiple countries. The campaign impersonates Egypt Post, aiming to steal credentials and financial information through fraudulent SMS messages and phishing websites.
Overview of the Campaign
In early May 2025, multiple phishing SMS messages claiming to be from Egypt Post. The messages tell the recipient that a delivery attempt failed twice and that they need to update their address information, redirecting them to a fake Egypt Post website. The domains used in the campaign are consistent with infrastructure previously seen in Smishing Triad operations.
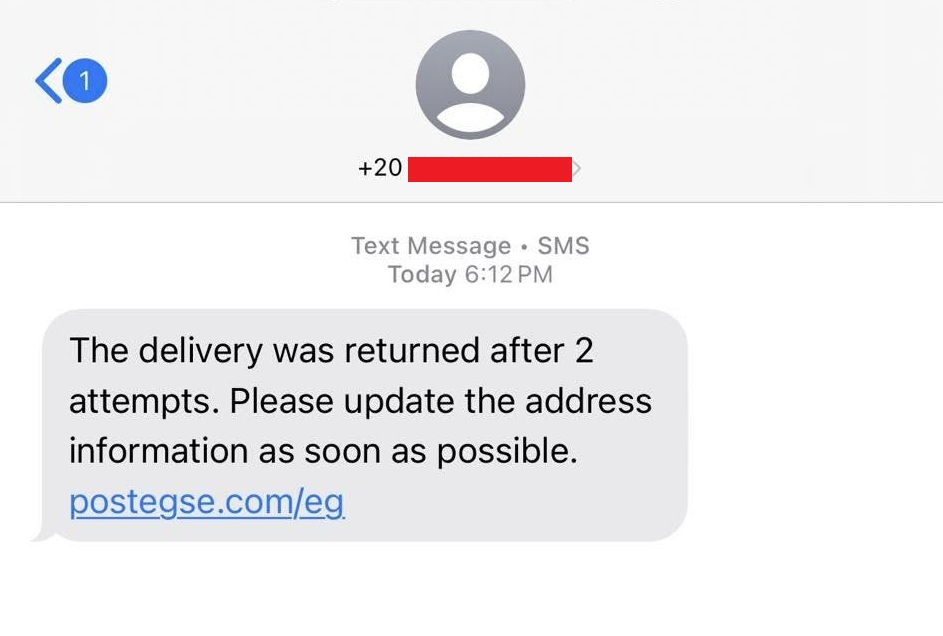
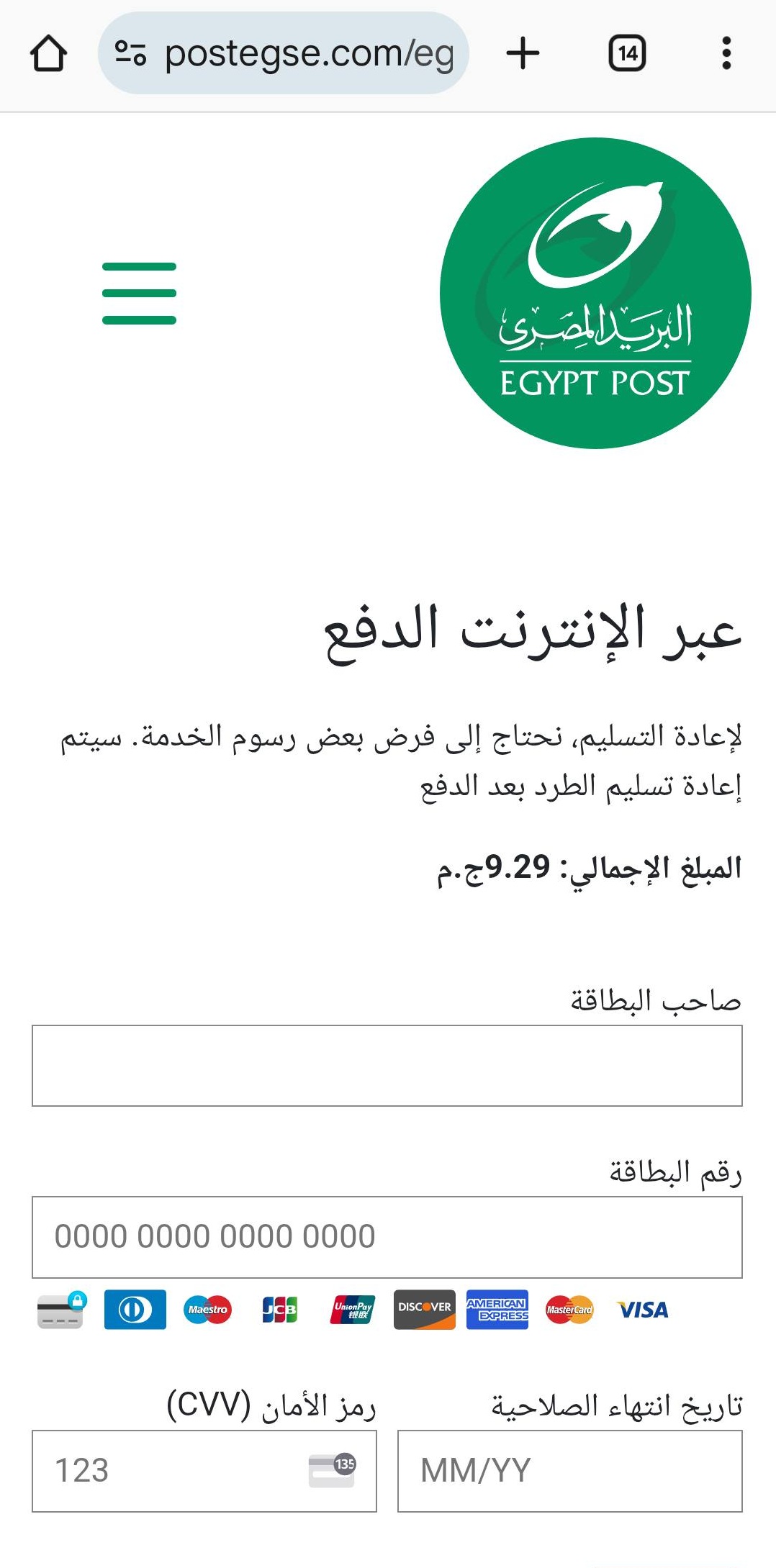
The link leads to a phishing website impersonating Egypt Post, where users are prompted to enter their full card details—including name, number, expiration date, and CVV—under the pretext of paying a small delivery fee (9.29 EGP).
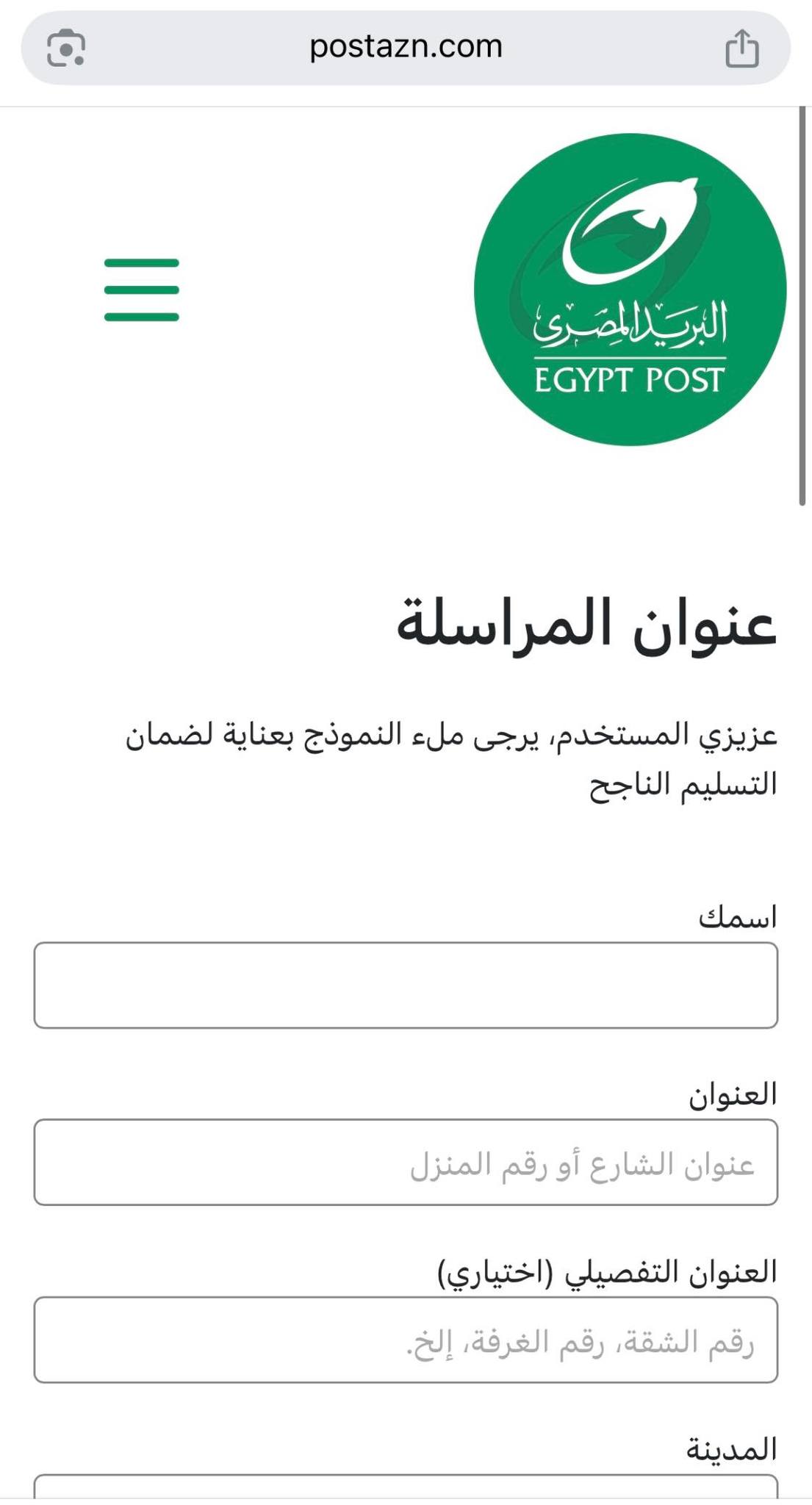
Another link leads to a phishing website impersonating Egypt Post, where users are asked to submit personally identifiable information (PII) such as their name and full address.
Who is the Smishing Triad?
The Smishing Triad is a Chinese-speaking cybercriminal group that specializes in global smishing operations (SMS-based phishing). The group is primarily known for impersonating national postal services and logistics companies, distributing fraudulent messages that claim the recipient must resolve an issue with a package or shipment.
Their primary goal is to harvest personally identifiable information (PII) and payment credentials from victims through mobile-optimized phishing pages. Notably, the group frequently leverages compromised Apple iMessage accounts to distribute these fraudulent messages at scale — a tactic that allows them to bypass traditional SMS gateways and increase delivery success rates.
The Smishing Triad also offers phishing kits, infrastructure, and services for sale via Telegram, enabling a decentralized affiliate model where other cybercriminals can launch localized attacks using the same backend systems.
Targeted Countries
The Smishing Triad has conducted smishing campaigns across the following countries:
- North America: United States, Canada, Mexico, Guatemala, Costa Rica, Dominican Republic, Bahamas, Belize, Cuba, El Salvador, Honduras, Jamaica, Nicaragua, Panama, and St. Lucia
- South America: Argentina, Brazil, Chile, Colombia, Ecuador, Peru, Uruguay, Bolivia, Guyana, Paraguay, and Venezuela
- Europe: Austria, Belarus, Belgium, Bulgaria, Croatia, Czech Republic, Finland, France, Germany, Greece, Ireland, Italy, Lithuania, Moldova, Netherlands, Norway, Poland, Portugal, Romania, Serbia, Slovakia, Spain, Switzerland, United Kingdom, Ukraine, Albania, Cyprus, Denmark, Estonia, Hungary, Kosovo, Latvia, Luxembourg, Macedonia, Malta, Monaco, Slovenia, and Sweden
- Middle East: Egypt, Georgia, Israel, Kazakhstan, Libya, Saudi Arabia, Turkey, United Arab Emirates, Bahrain, Iraq, Jordan, Kuwait, Kyrgyzstan, Oman, Qatar, and Turkmenistan
- Africa: South Africa, Angola, Botswana, Congo, Ghana, Kenya, Mali, Mauritius, Morocco, Namibia, Nigeria, Seychelles, Togo, Tunisia, and Uganda
- Asia-Pacific: Australia, Hong Kong, India, Indonesia, Japan, Malaysia, China, New Zealand, Pakistan, Philippines, Singapore, Sri Lanka, Thailand, Armenia, Brunei, Cambodia, Fiji, South Korea, Laos, Maldives, Mongolia, Taiwan, and Vietnam
Targeted Industries
The Smishing Triad’s operations are focused on the following sectors:
- Postal & Logistics: National postal services, private couriers, and global shipping firms including USPS, Royal Mail, La Poste, DHL, FedEx, UPS, Amazon (U.S.), Bay Area FasTrak (California, U.S.), Canada Post, Correo El Salvador, Correos de Costa Rica, Correos de Guatemala (Guatemala Post), Estafeta (Mexico), Telcel (Mexico), Telefónica México, The Toll Roads (California, U.S.), Tigo Guatemala, 4-72 Shipping (Colombia), Agencia Nacional de Infraestructura (ANI) (Colombia), Correo Uruguayo (Uruguay), Peruvian Ministry of Labor, Servicios Postales del Ecuador, Servientrega Post (Colombia), An Post (Ireland), Aramex (Bulgaria), BelPost (Belarus), Chronopost France, Czech Posta (Czech Republic), DPD Parcel (France), Evri (U.K.), Hellenic Post (ELTA) (Greece), InPost (Poland), Lietuvos Paštas (Lithuania), Mondial Relay (France), myHermes Konto (Germany), Obrasci Posta (Croatia), Post AG (Austria), Poșta Moldovei (Moldova), Poșta Română, Posten Norway, Posti Group (Finland), Poste Italiana (Italy), Public Enterprise “Pošta Srbije” (Serbia), Posturinn (Iceland), Royal Mail (U.K), Slovenská Pošta (Slovakia), Swiss Post (Switzerland), Ukraine Post, Georgian Post (Georgia), Israel Post, Qaz Post (Kazakhstan), SMSA Express (Saudi Arabia), SPL Express (Saudi Arabia), Turkish Post (PTT) (Turkey), Yurtiçi Kargo (Turkey), Algeria Post, Egypt Post, Libyan Post (Libya), South African Post Office, AIS Thailand, Australia Post, HKeToll (China), India Post, J&T Express (Asia), New Zealand Post, Pakistan Post (EP), Philippine Postal Corporation, Singapore Post, SMBC Card (Japan), Sri Lanka Post, Telkomsel (Indonesia), TEPCO (Japan), Thailand Post, and Yamato Transport (Japan)
- Telecommunications: Providers including Maxis Telecom (Malaysia), Telcel (Mexico), Tigo Guatemala, Telkomsel (Indonesia), M360 SMS Send (Philippines), and Altice Dominican Republic (Dominican Republic)
- Transport & Toll Systems: Electronic toll services and transport infrastructure such as Bay Area FasTrak (California, U.S.), Dirección General de Tráfico (DGT) (Spain), East Nippon Expressway Company (E-NEXCO) (Japan), The Toll Roads (California, U.S.), and HKeToll (China)
- Finance, Banking & Retail: CitiGroup, HSBC, Mastercard, Visa, PayPal, Stripe, Australia and New Zealand Banking Group, Commonwealth Bank of Australia, National Australia Bank, Westpac Banking Corporation, ING Bank (Australia), Macquarie Bank, Bank of Nova Scotia, Bendigo and Adelaide Bank, HSBC Bank Australia, Bank of Queensland, Bank Australia, Bank of Sydney, Cuscal LTD, George Bank, Newcastle Permanent Building Society, Police Bank
- Government & Public Services: Dubai Police, Peruvian Ministry of Labor, Tokyo Electric Power (TEPCO) (Japan), and Public Enterprise “Pošta Srbije” (Serbia)
According to an analysis by Silent Push blog authors, approximately 187 unique TLDs have been observed across their campaigns. The most frequently used TLDs include:
- .top
- .xin
- .vip
- .world
- .cc
- .com
- .xyz
- .icu
- .cfd
- .ink
How This Campaign Is Linked to the Smishing Triad
Several indicators tie this Egypt Post impersonation campaign to the Smishing Triad:
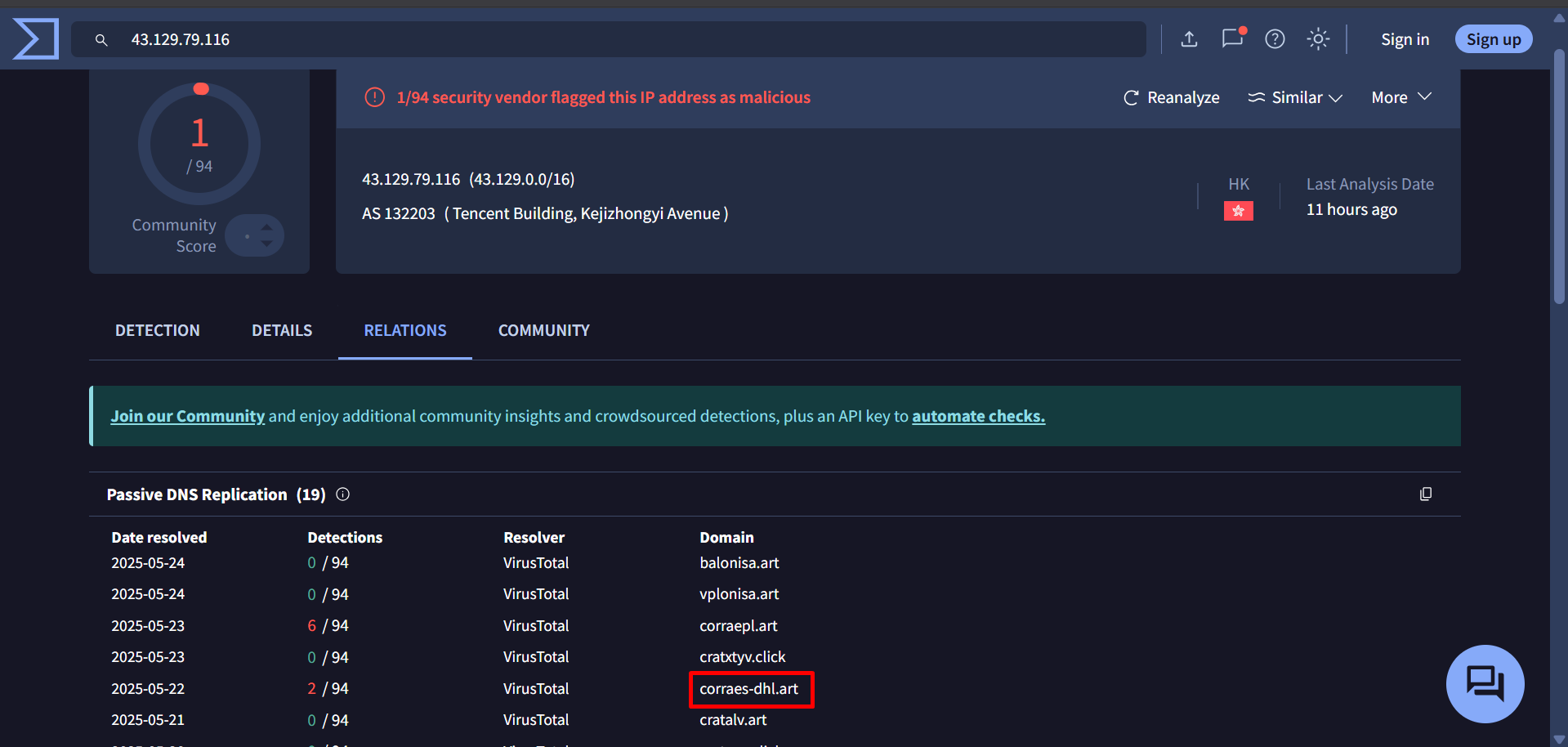
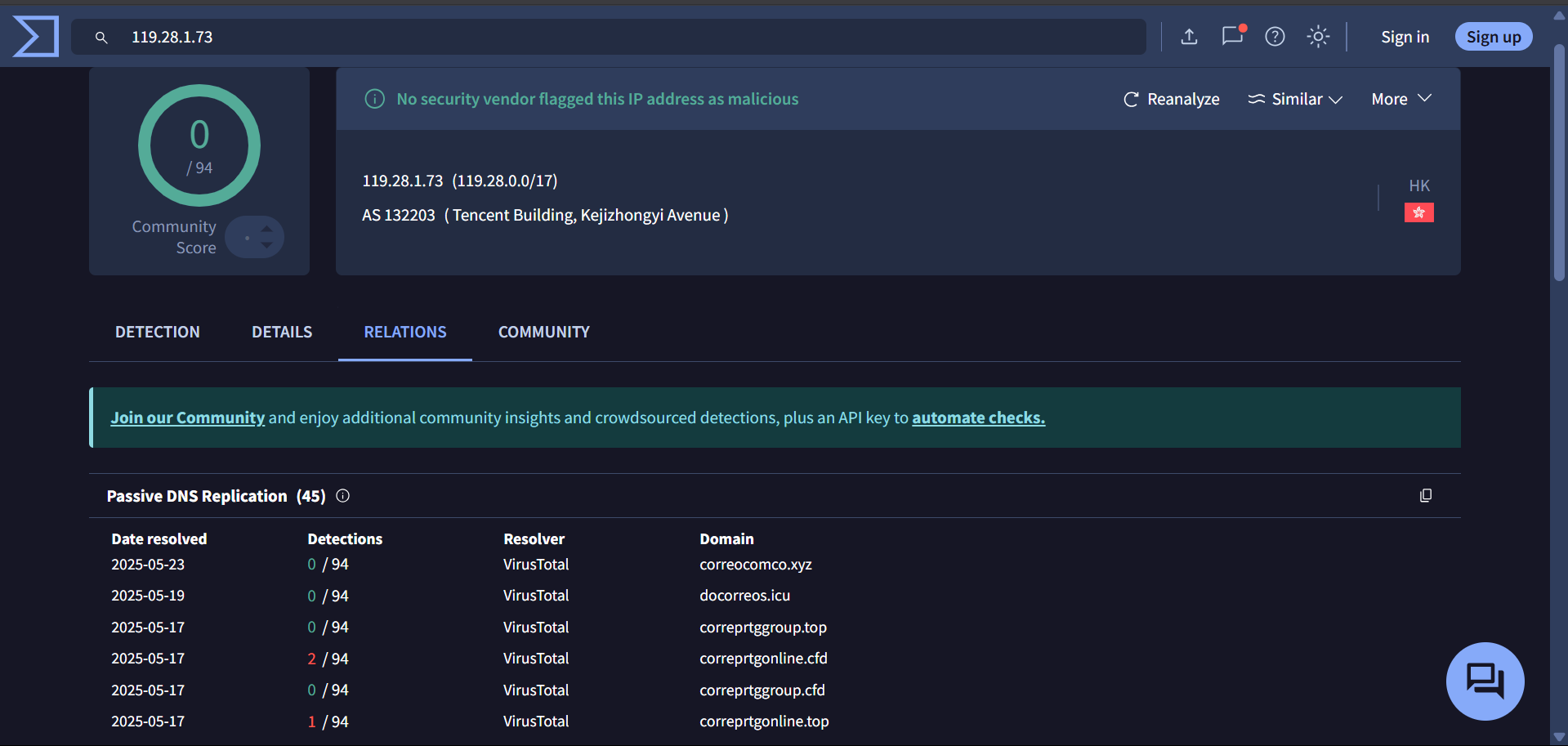
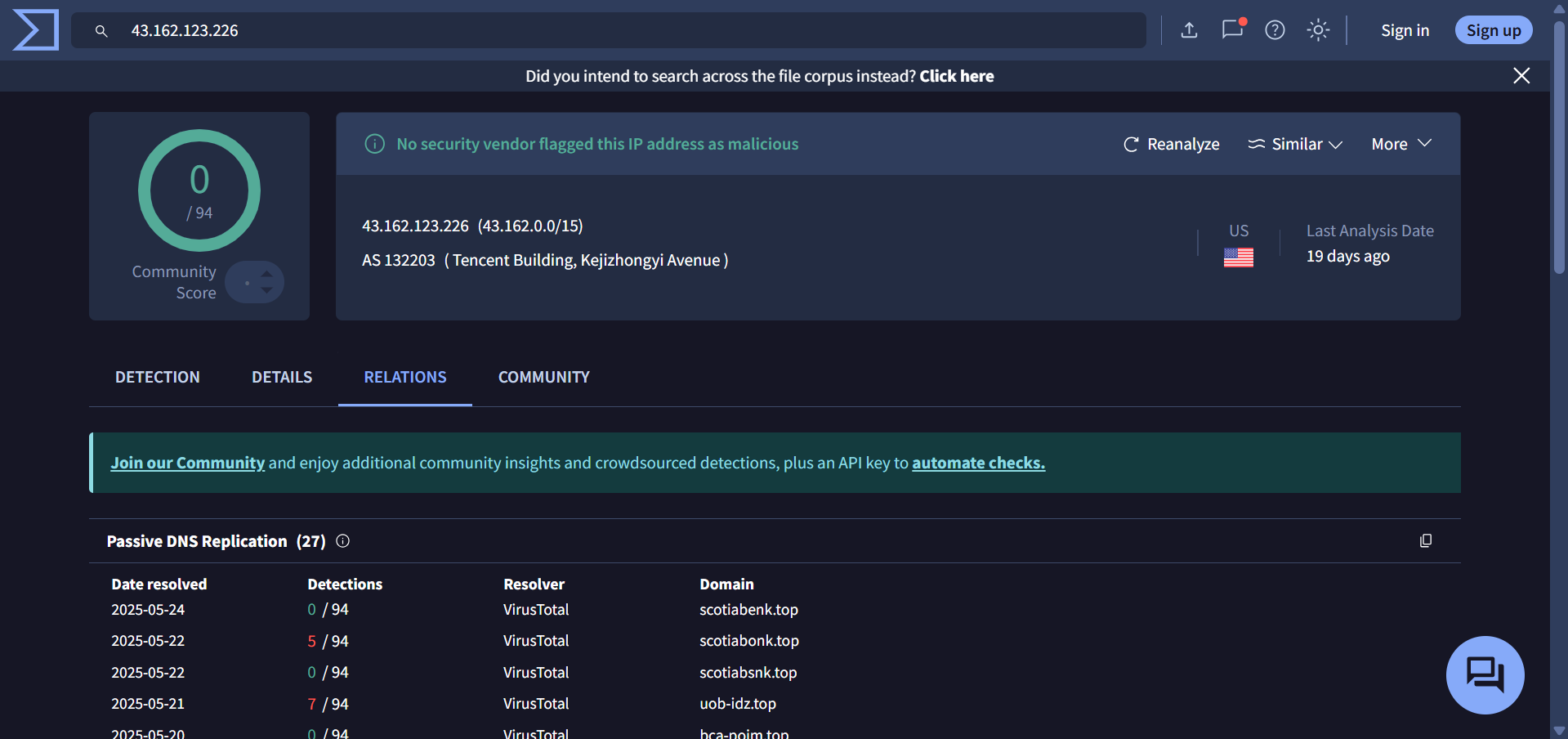
1- Phishing Infrastructure: The phishing domains used in this campaign resolve to IP addresses that are linked to infrastructure hosting domains currently active in Smishing Triad operations.
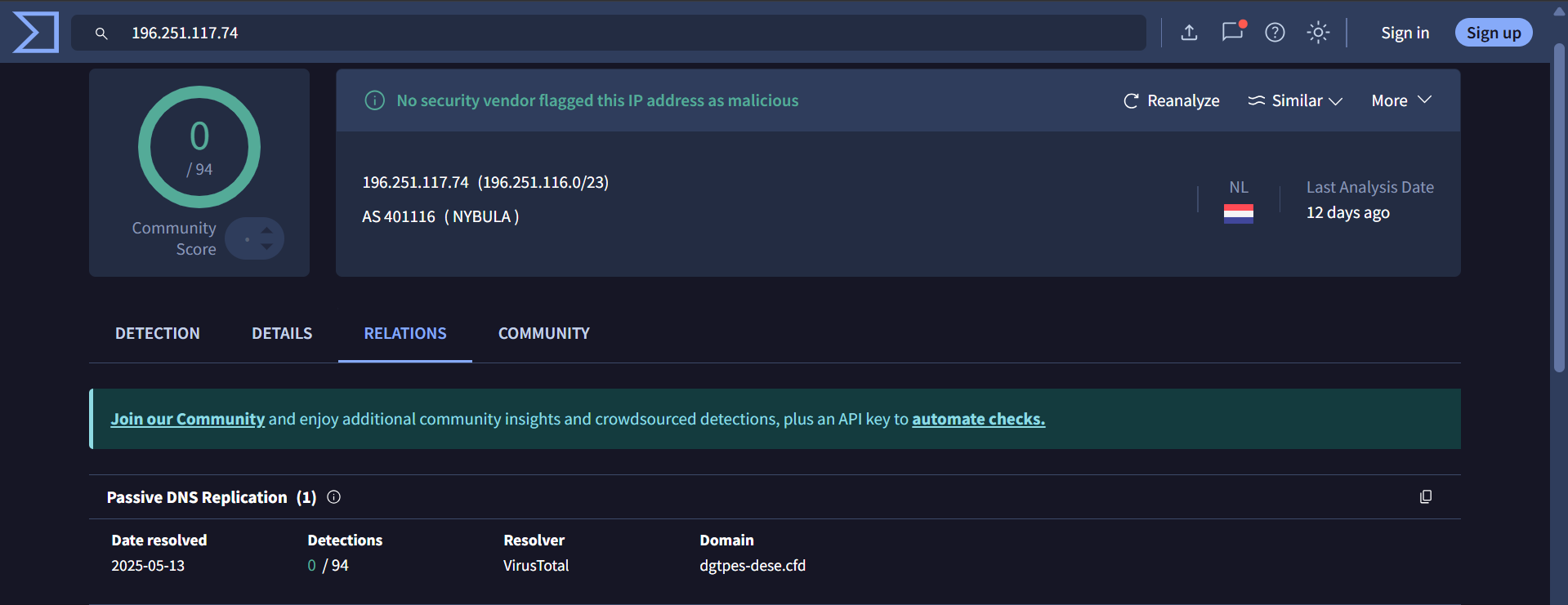
Multiple users who received the Egypt Post-themed smishing messages reported these domains: postegse[.]com and postuts[.]com.
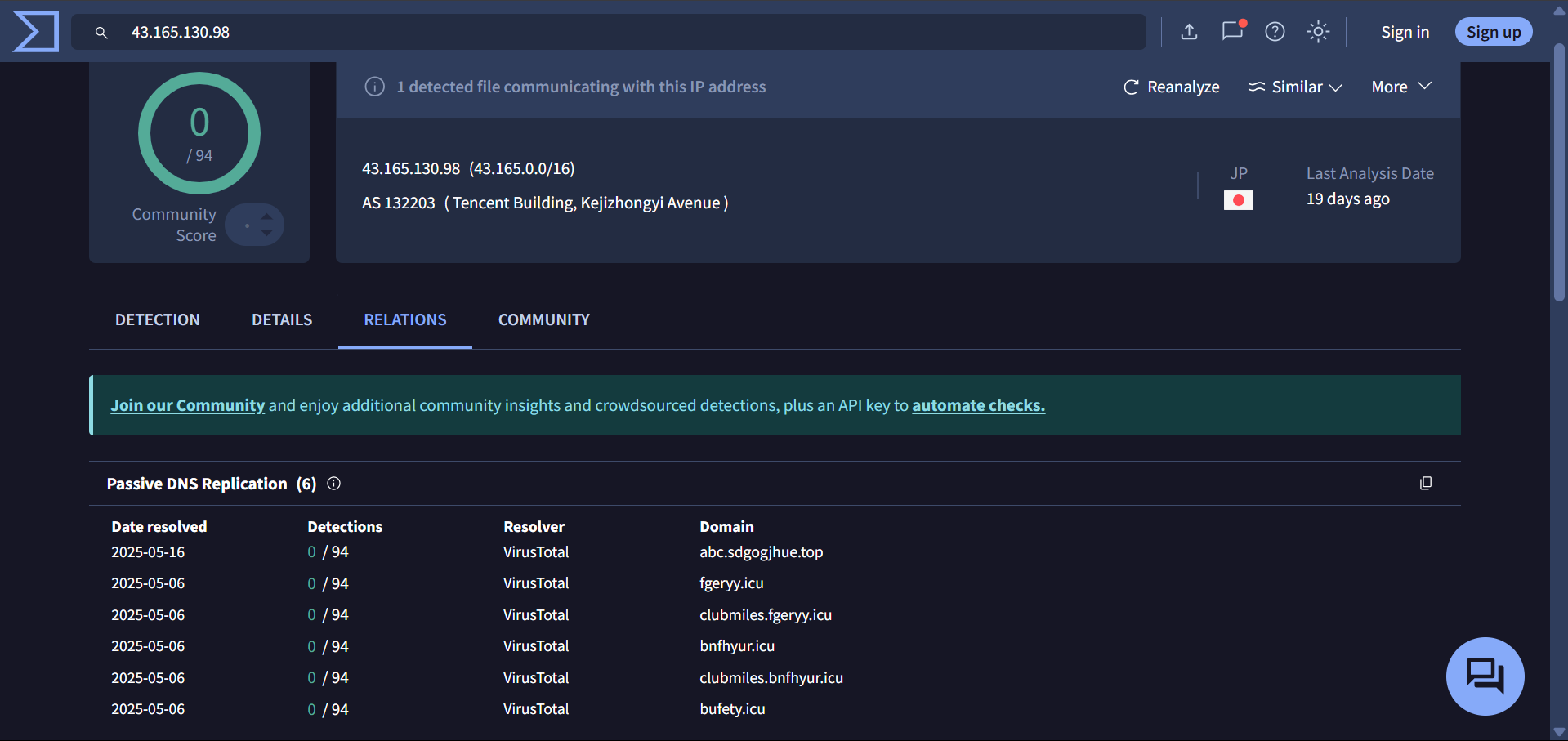
ewdfb[.]top domain is attributed to Smishing Triad – source
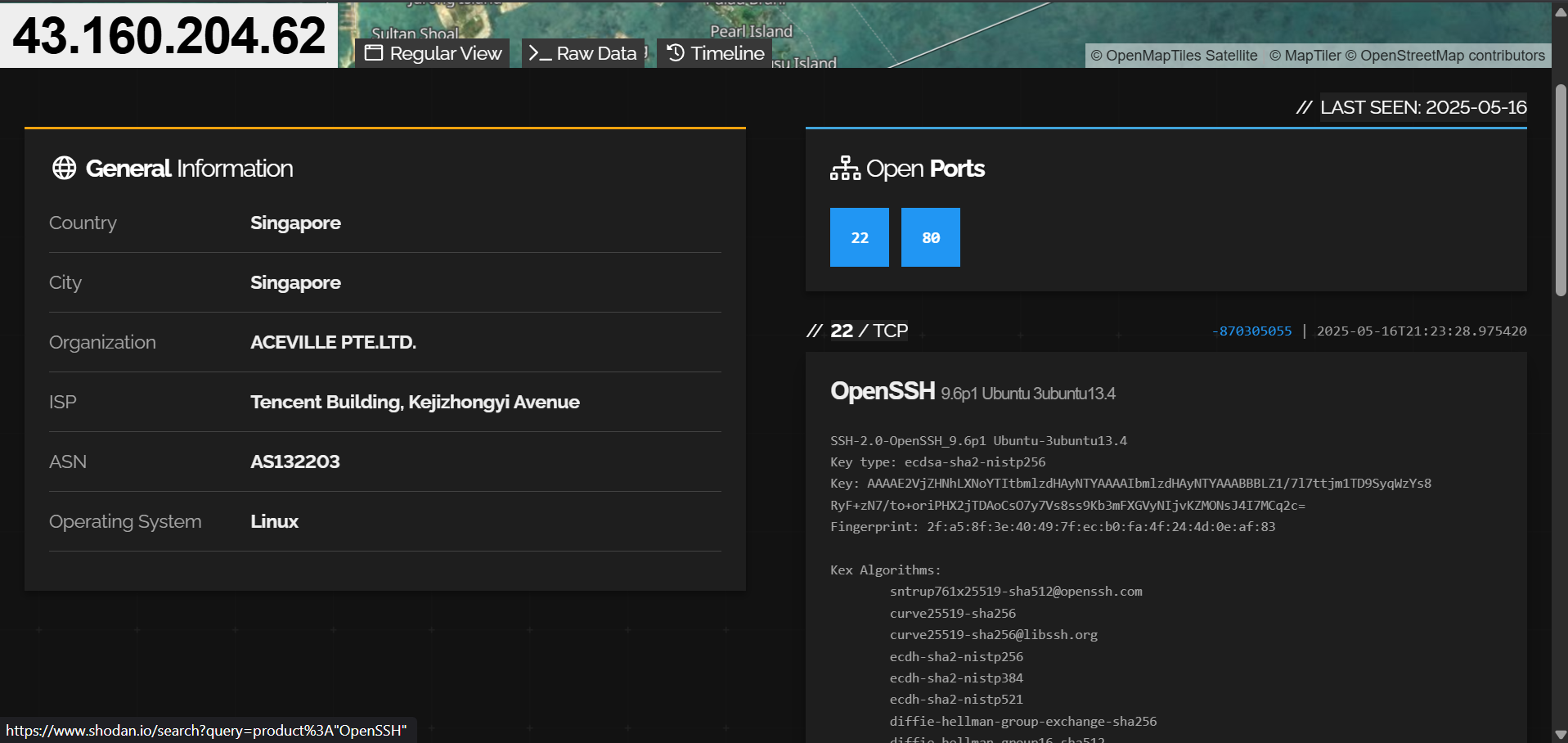
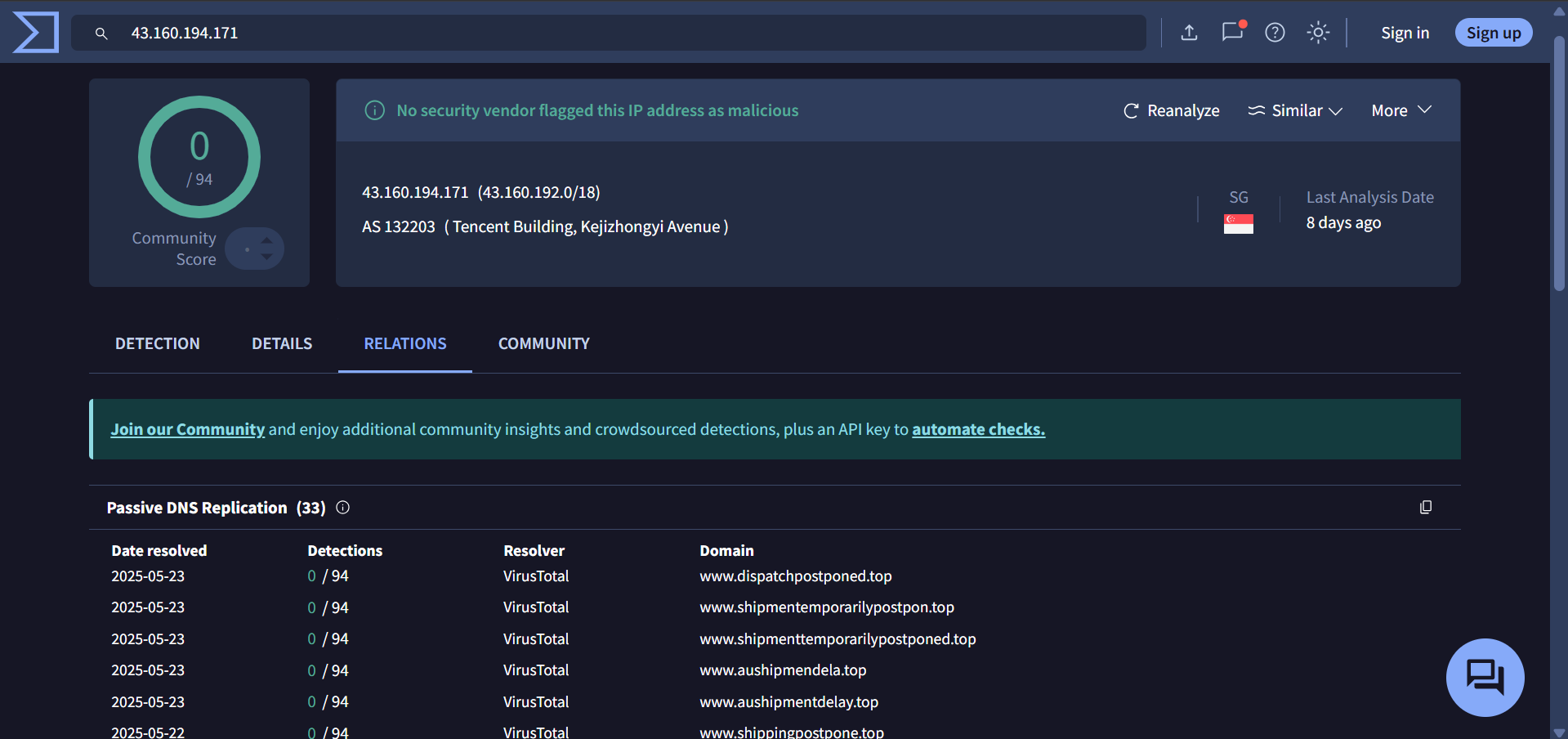
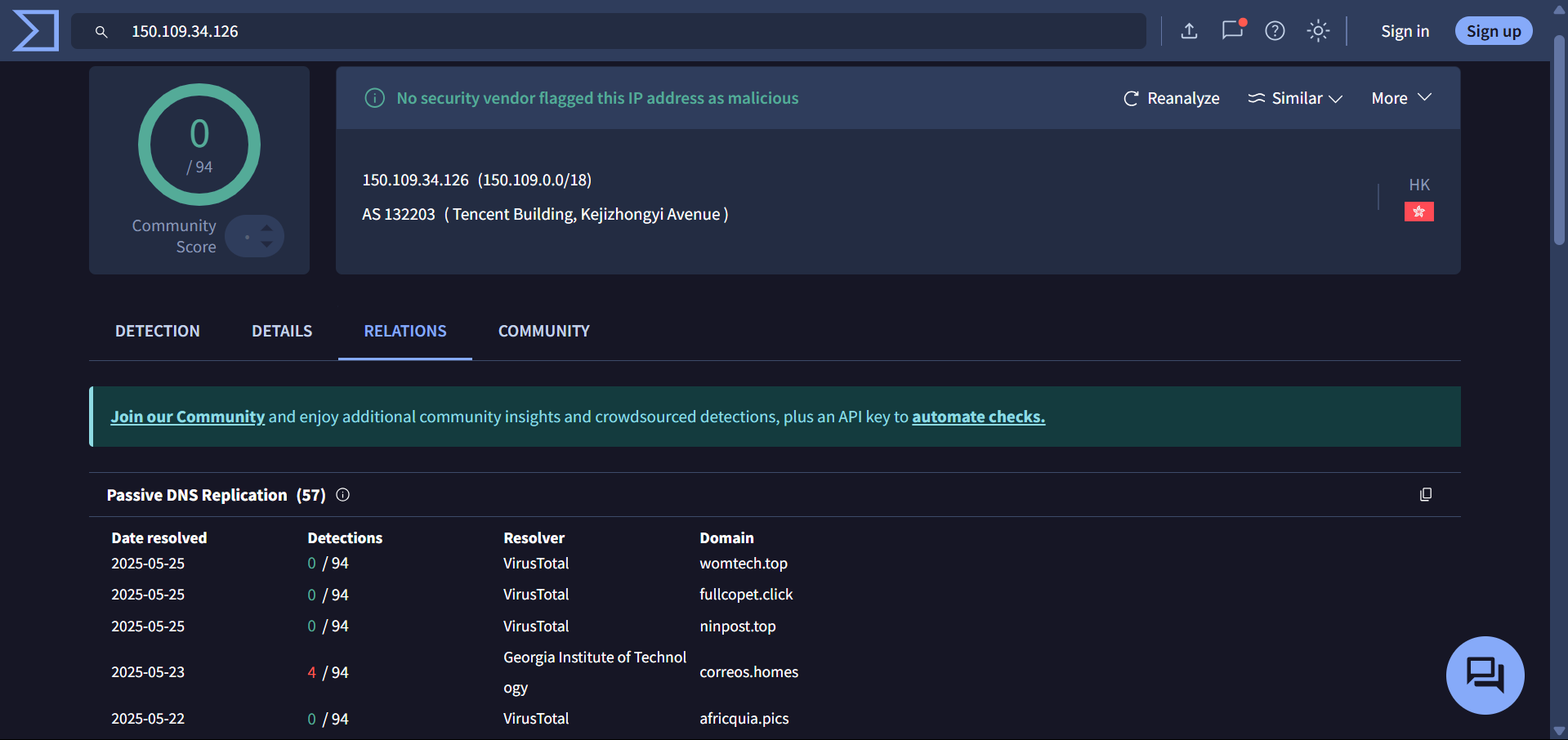
The IPs associated with postuts[.]com and ewdfb[.]top have both SSH (port 22) and HTTP (port 80) open.
43.160.204[.]62 (postuts[.]com):
43.133.39[.]120 (ewdfb[.]top):
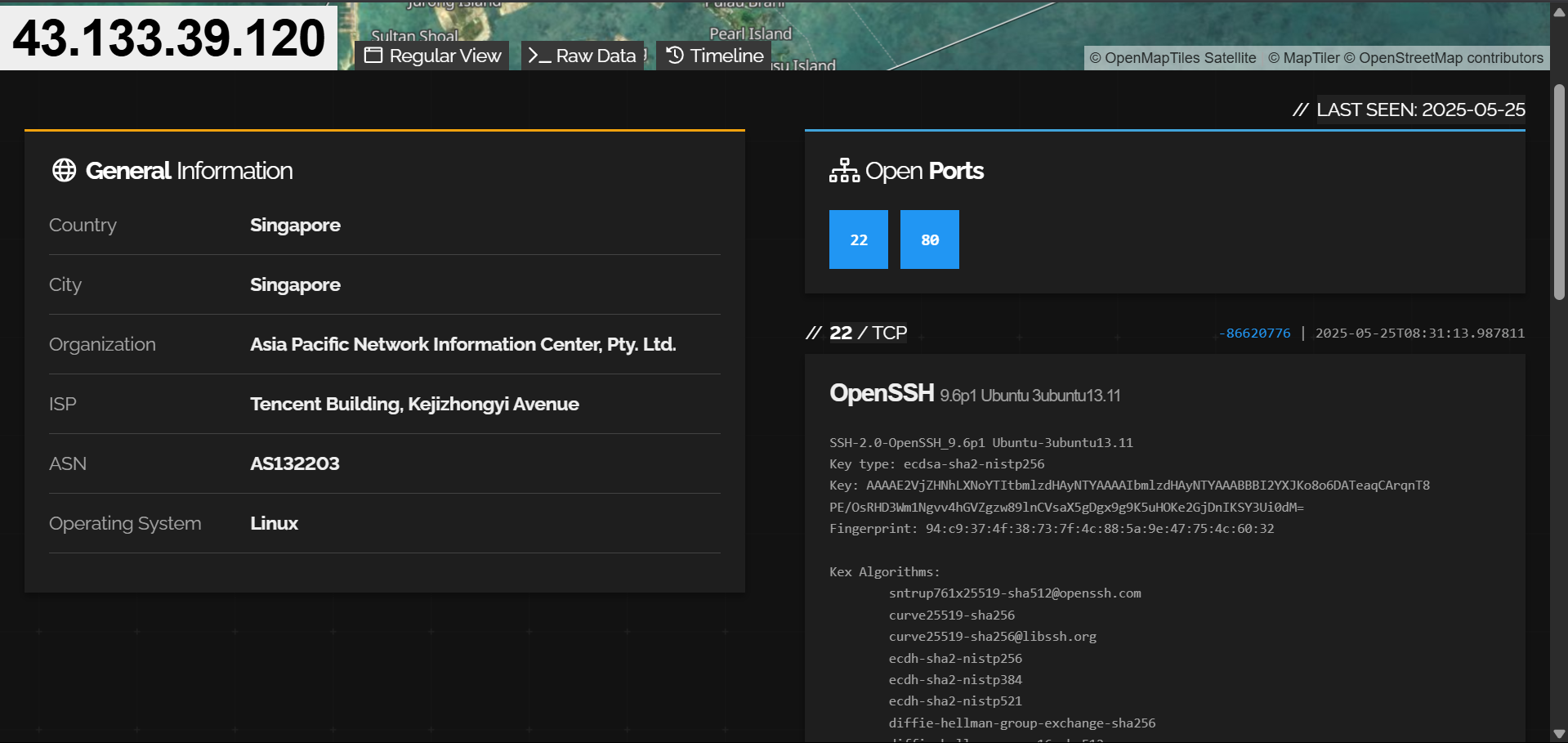
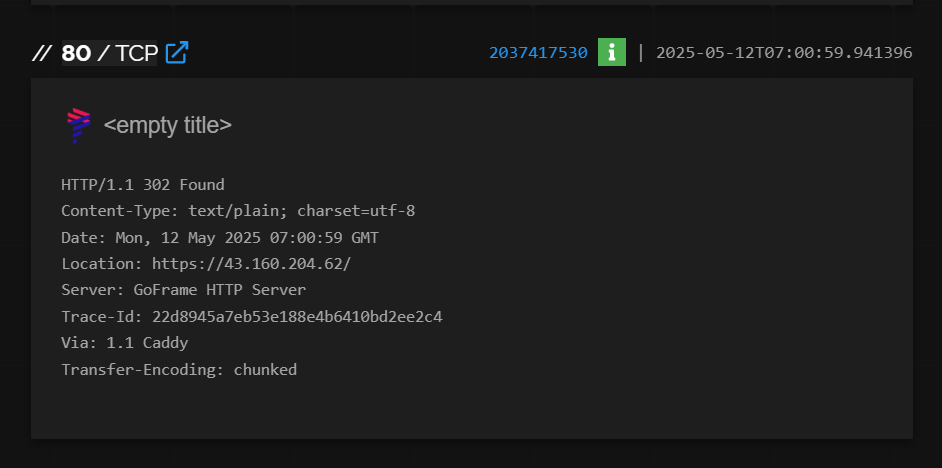
When comparing their HTTP responses over port 80, both return similar content.
43.160.204[.]62 (postuts[.]com):
43.133.39[.]120 (ewdfb[.]top):
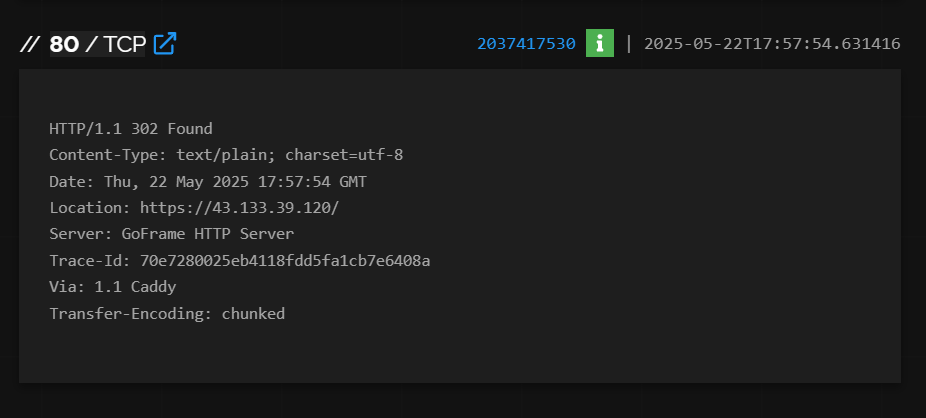
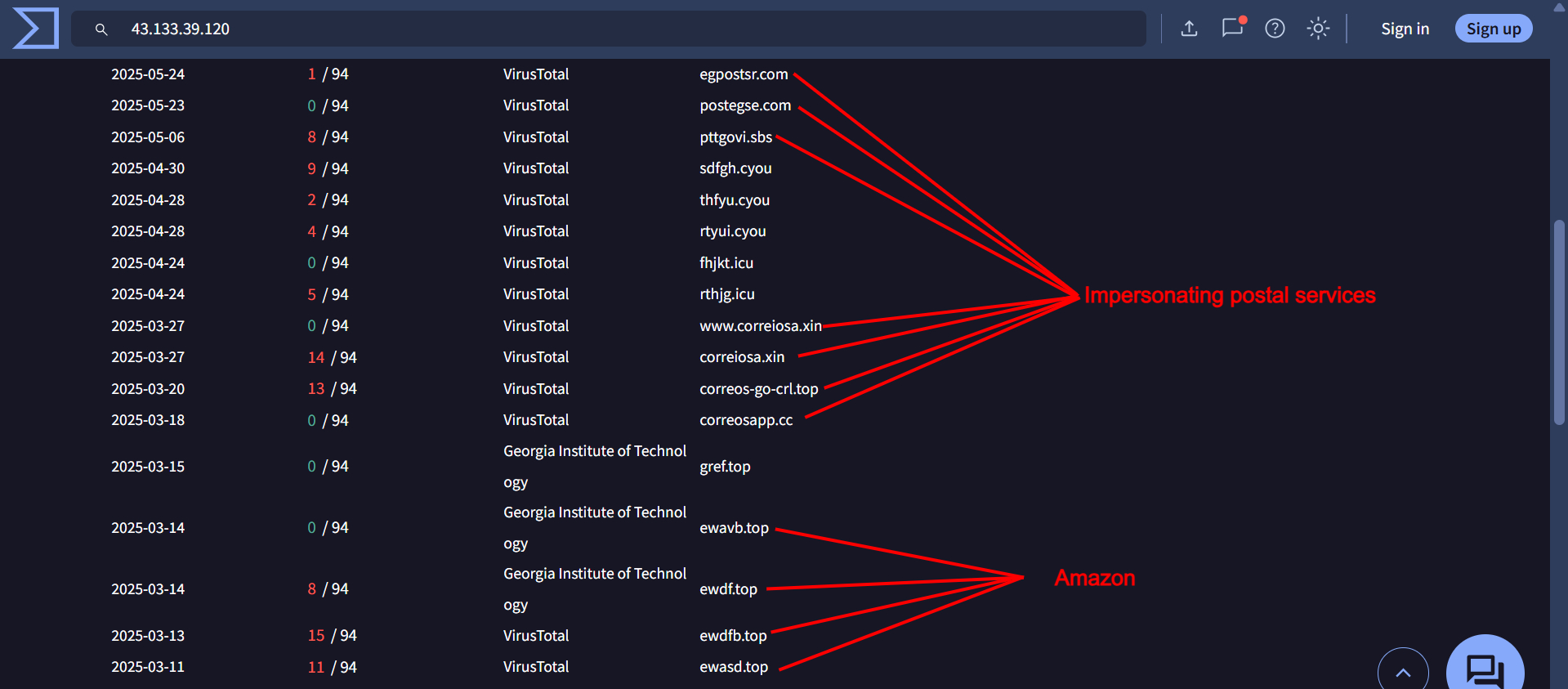
The domain postegse[.]com—reported as impersonating Egypt Post—and ewdfb[.]top both resolve to the same IP address: “43.133.39[.]120”.
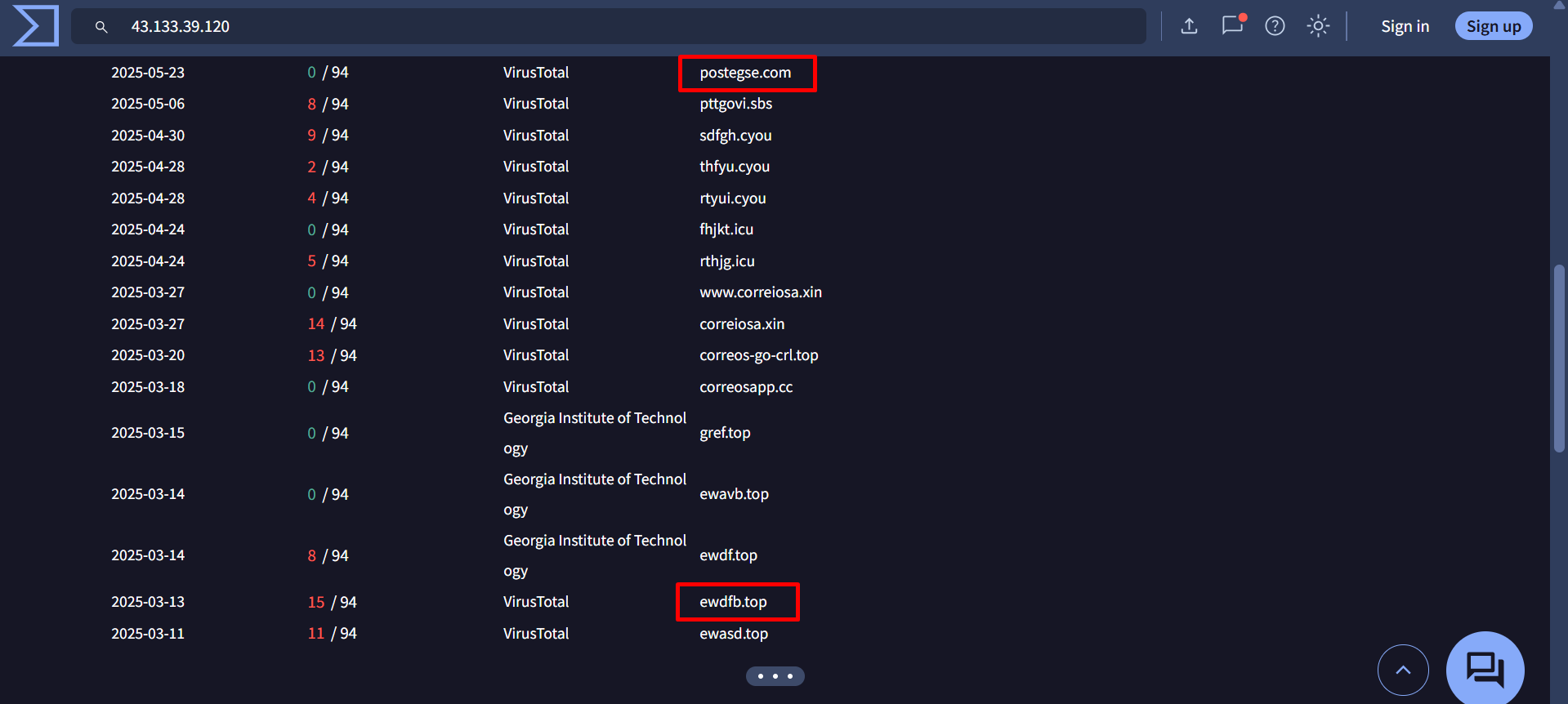
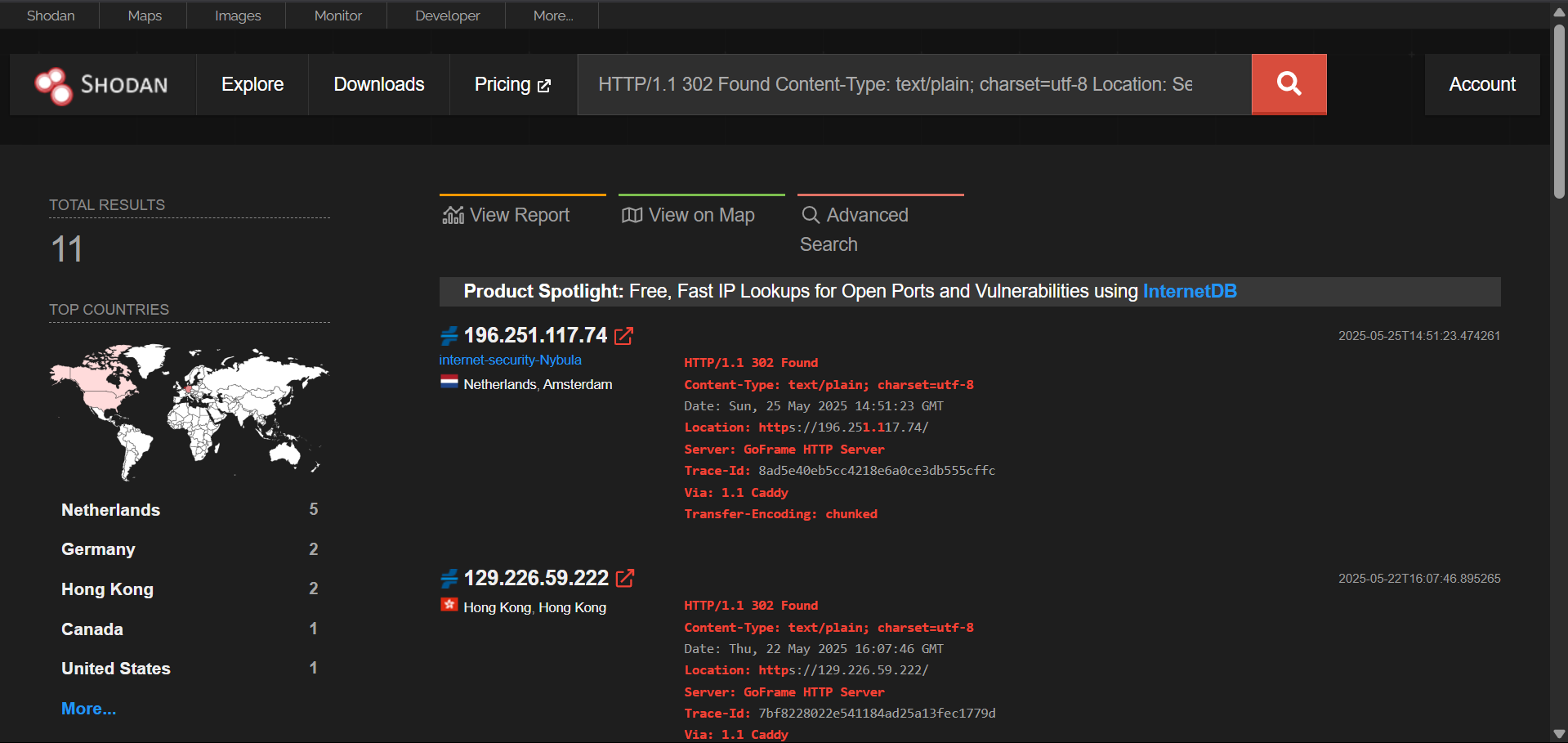
These IPs resolve domains impersonating organizations targeted by Smishing Triad
43.133.39[.]120:
43.160.204[.]62:
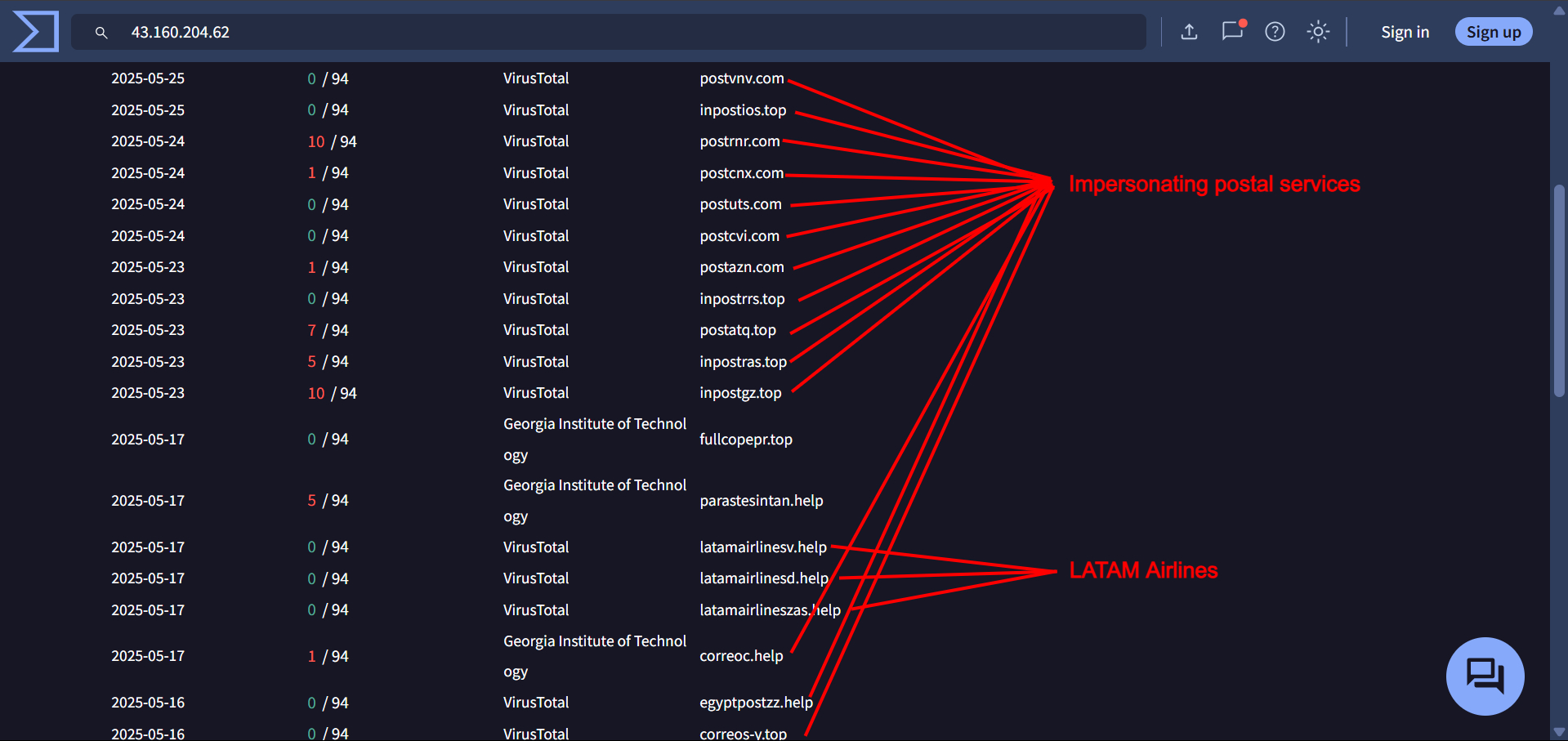
2- SMS Format Patterns: The structure of the messages—prompting users to “pay fees” or “update delivery details”—closely matches campaigns impersonating other postal services like USPS (US), Royal Mail (UK), and Correos (Spain).
Smishing message impersonates USPS:
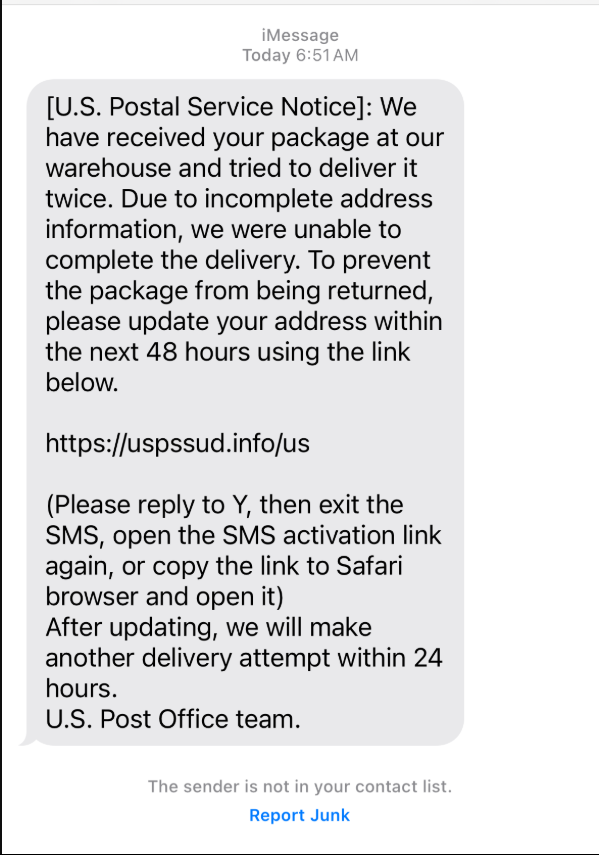
Message impersonates Egypt Post:

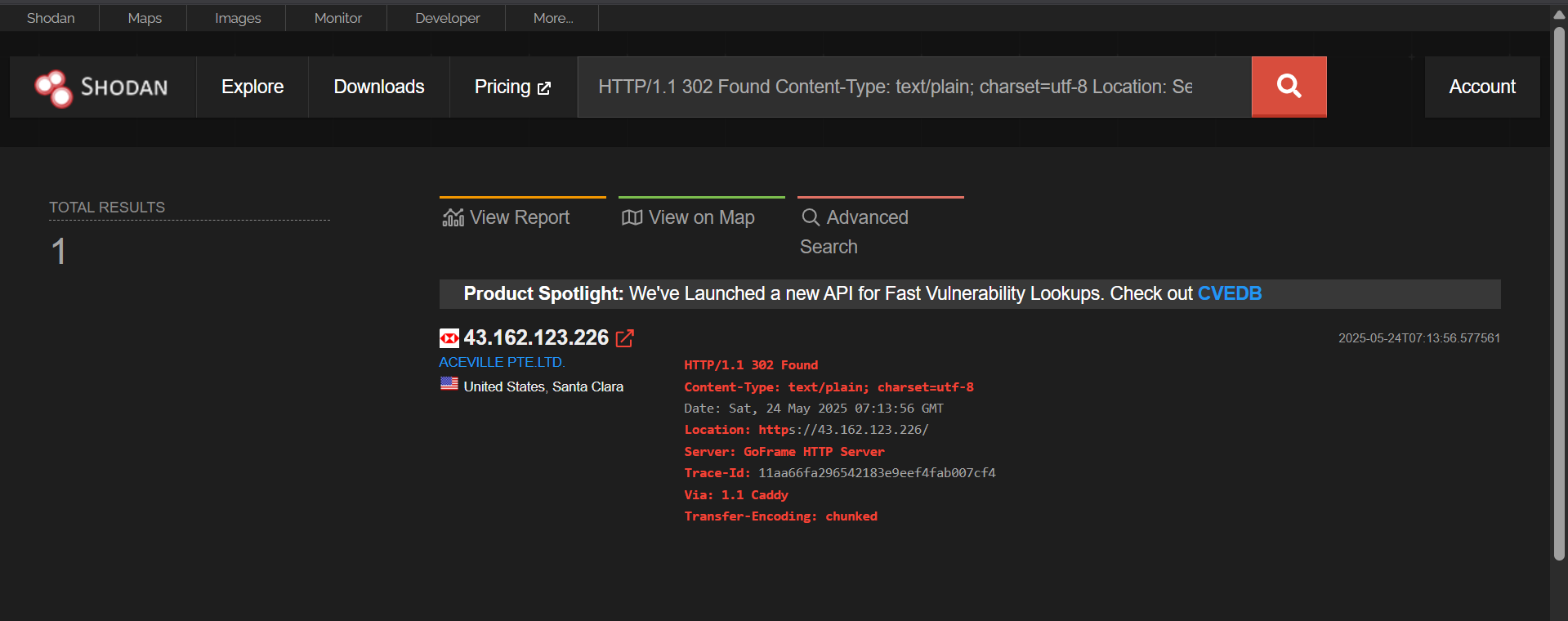
Uncovering Undetected Infrastructure for Smishing Triad
Rule Used in Shodan
HTTP/1.1 302 Found Content-Type: text/plain; charset=utf-8 Location: Server: GoFrame HTTP Server Trace-Id: Via: 1.1 Caddy Transfer-Encoding: chunked
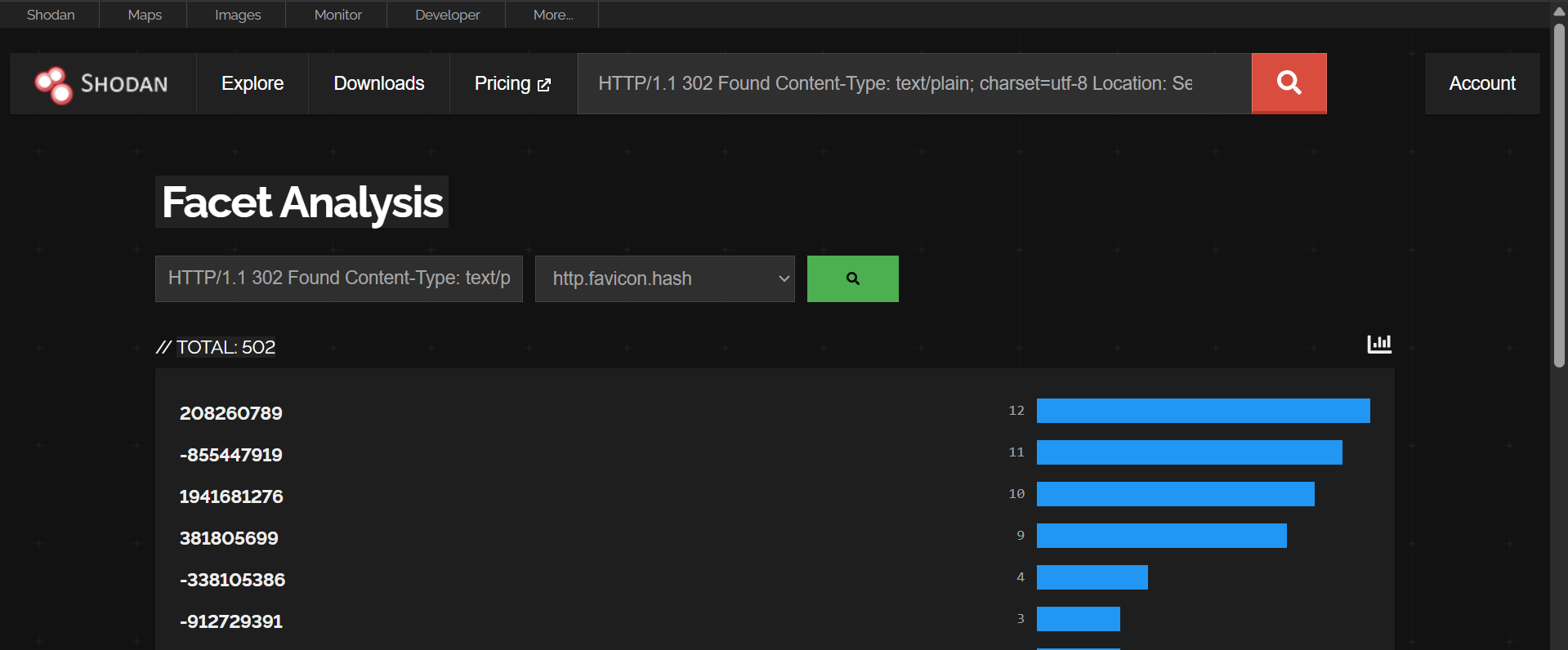
Facet Analysis tool sorted IPs by favicon hash
http.favicon.hash:208260789 –> Impersonates Australia Post
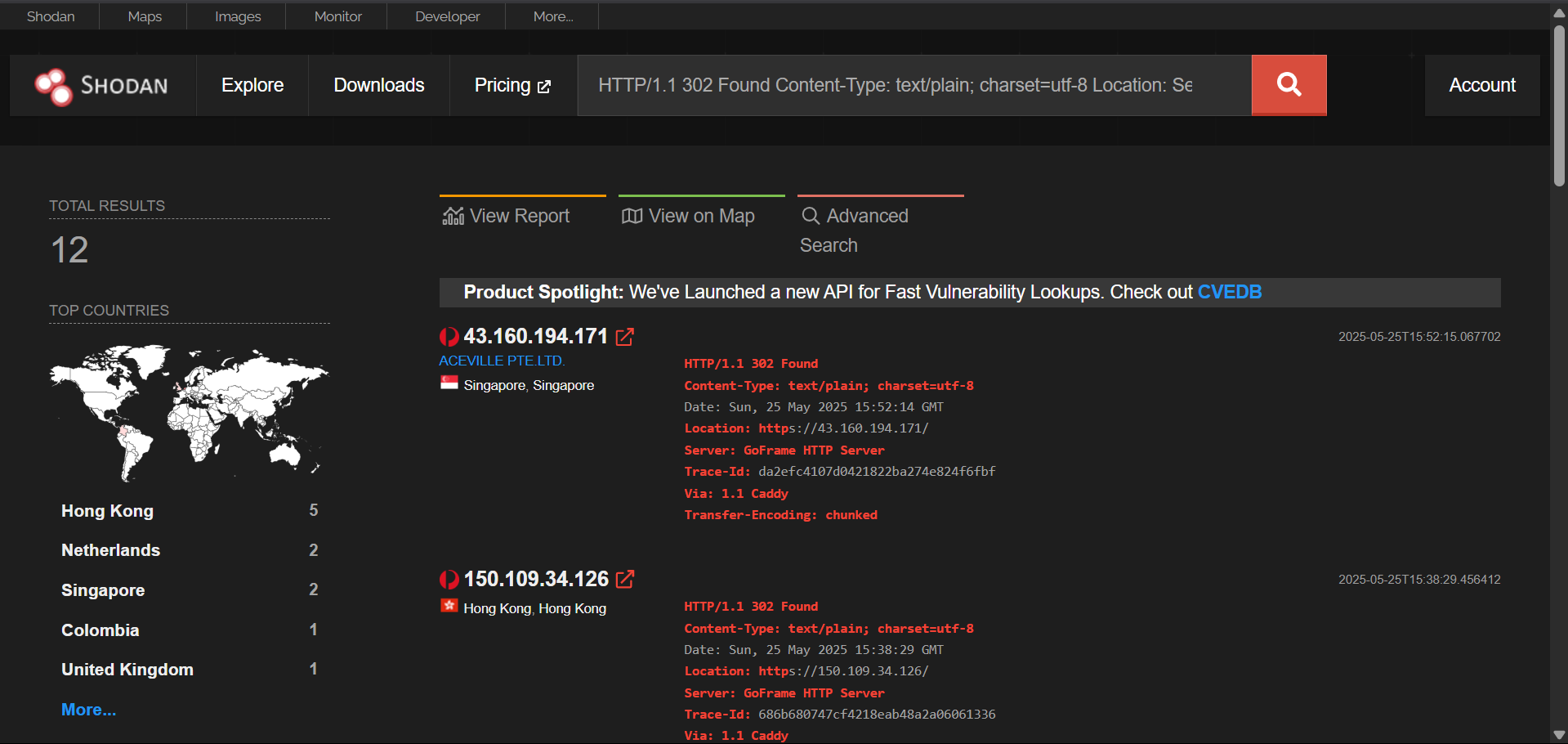
Undetected by VirusTotal
http.favicon.hash:-855447919 –> Impersonates dirección general de tráfico (General Traffic Department in spain)
Undetected on VirusTotal and resolves to a domain end with “.cfd”
http.favicon.hash:1941681276–> Impersonates Amazon
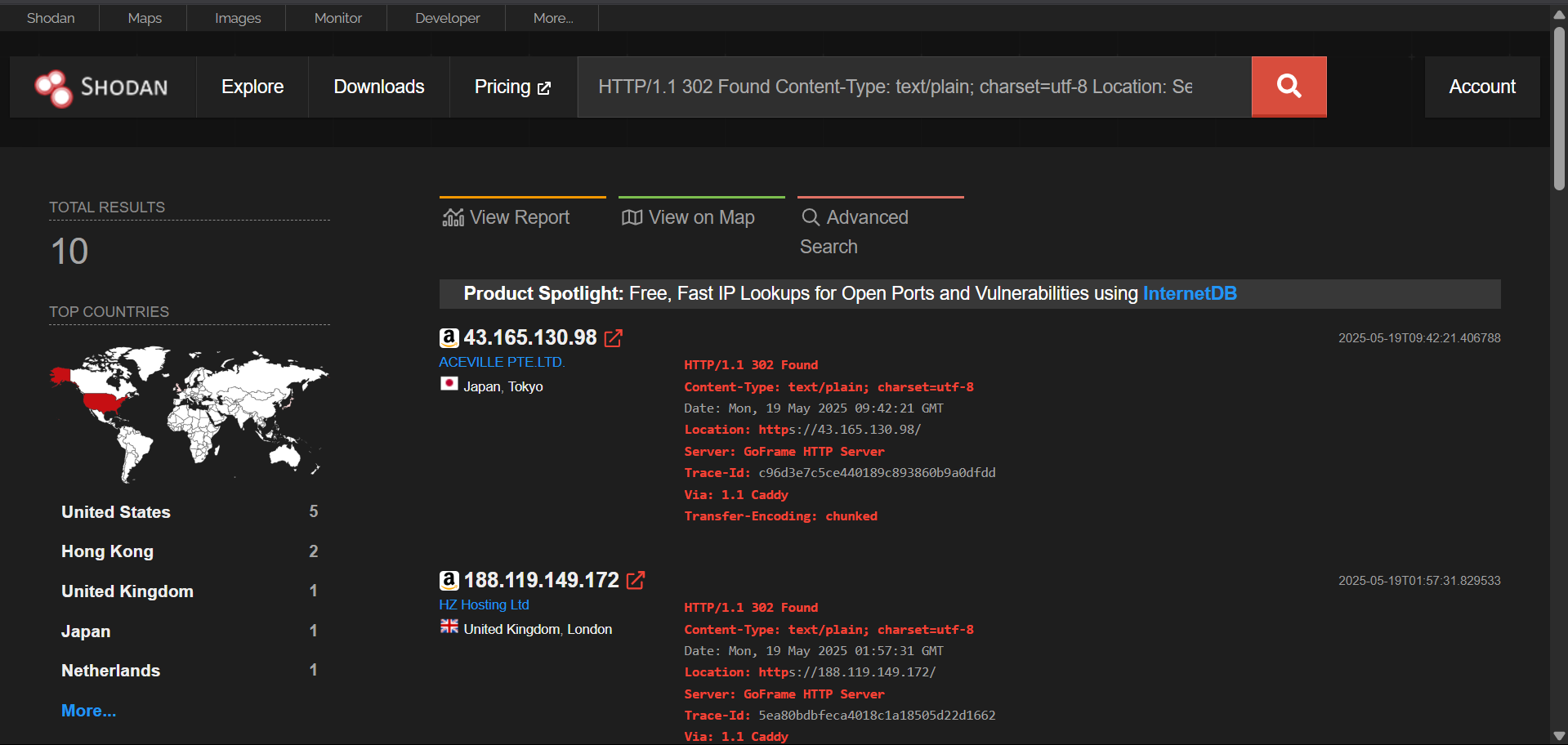
Undetected on VirusTotal, also resolves to domains end with “.icu” and “.top”
http.favicon.hash:381805699 –> Impersonates DHL
VirusTotal detection: 1/94
http.favicon.hash:-338105386 –> Impersonating FasTrak (Electronic toll collection Company)
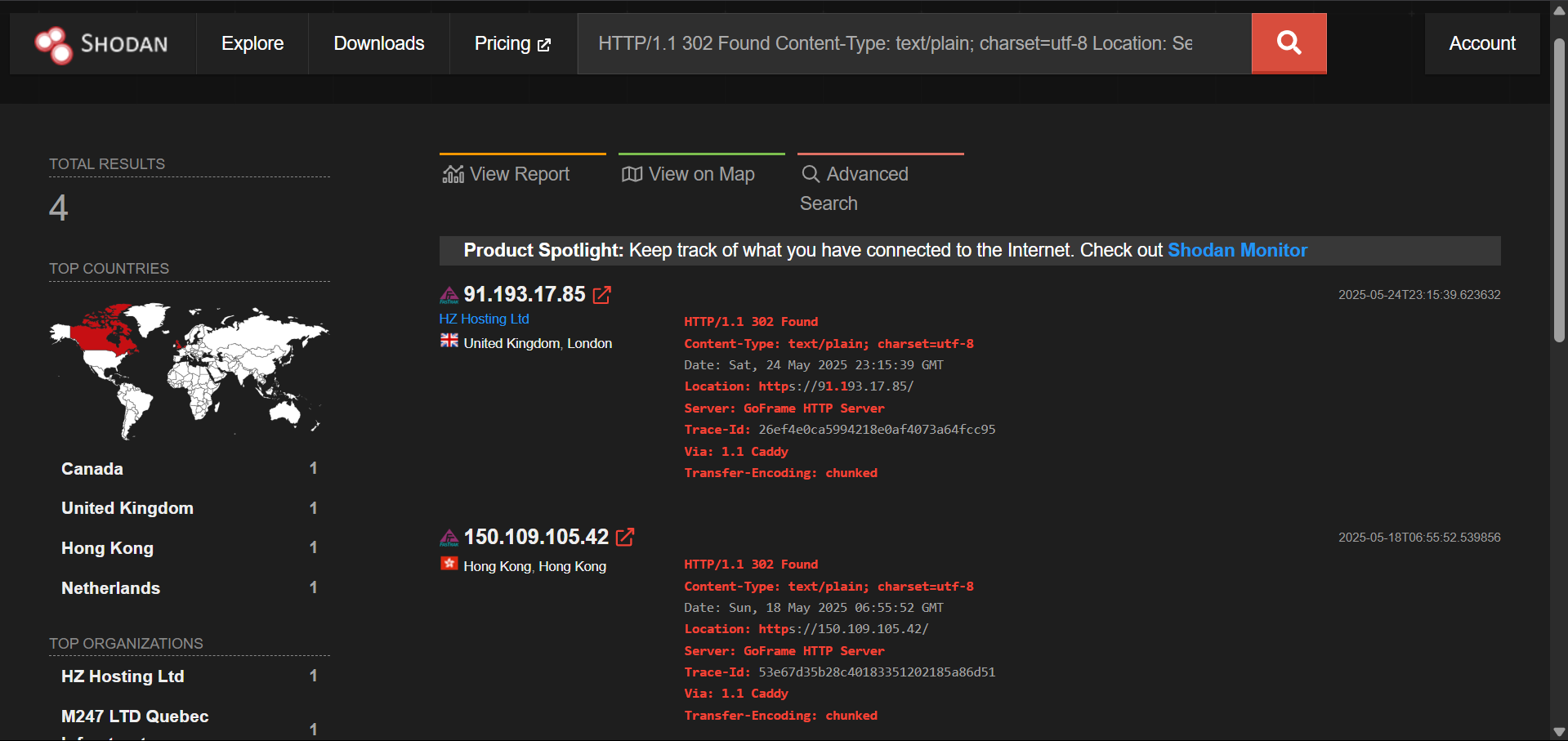
VirusTotal detection: 1/94
http.favicon.hash:-912729391 –> Impersonates LATAM Airlines
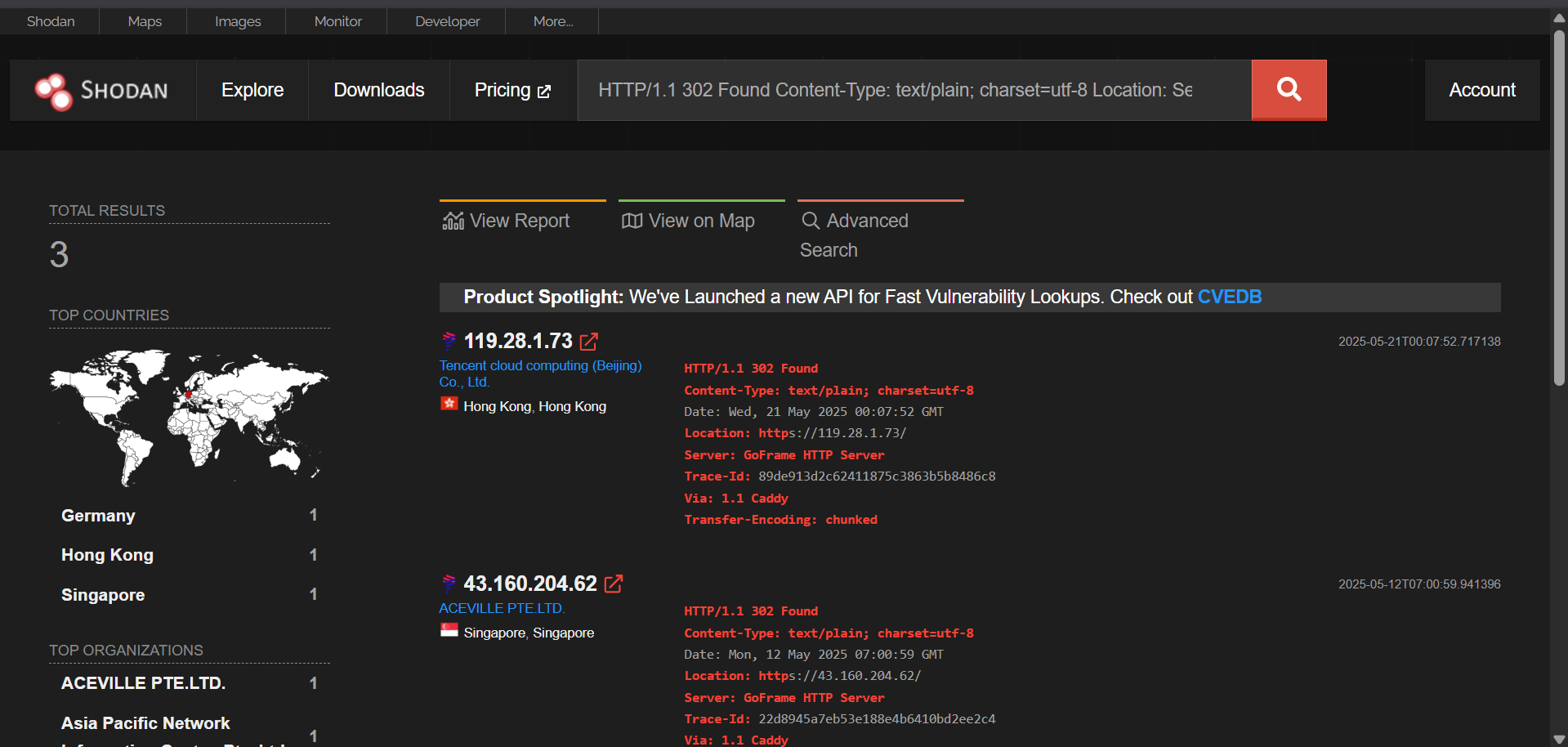
Undetected by VirusTotal
http.favicon.hash:-1528840246 –> Impersonates HSBC Bank
Undetected by VirusTotal
The other favicons are impersonating other banks, postal services and express delivery companies like: NEXCO East, mbh bank, J&T Express, etc.
Conclusion
The phishing campaign impersonating Egypt Post matches the known tactics of the Smishing Triad. The group’s infrastructure, message format, and phishing site behavior solidify the attribution to the Smishing Triad.
MITRE ATT&CK
Initial Access
- Phishing via SMS (Smishing) – T1660
- Phishing – T1566
Defense Evasion
- Impersonation – T1656
Exfiltration
- Exfiltration Over C2 Channel – T1041
Indicators of Compromise (IOCs)
101[.]32[.]23[.]119
107[.]175[.]111[.]20
119[.]28[.]1[.]73
124[.]156[.]117[.]151
124[.]156[.]97[.]60
129[.]226[.]178[.]65
129[.]226[.]50[.]30
129[.]226[.]59[.]222
129[.]226[.]74[.]220
146[.]70[.]86[.]28
150[.]109[.]105[.]42
150[.]109[.]34[.]126
150[.]109[.]34[.]190
154[.]223[.]16[.]232
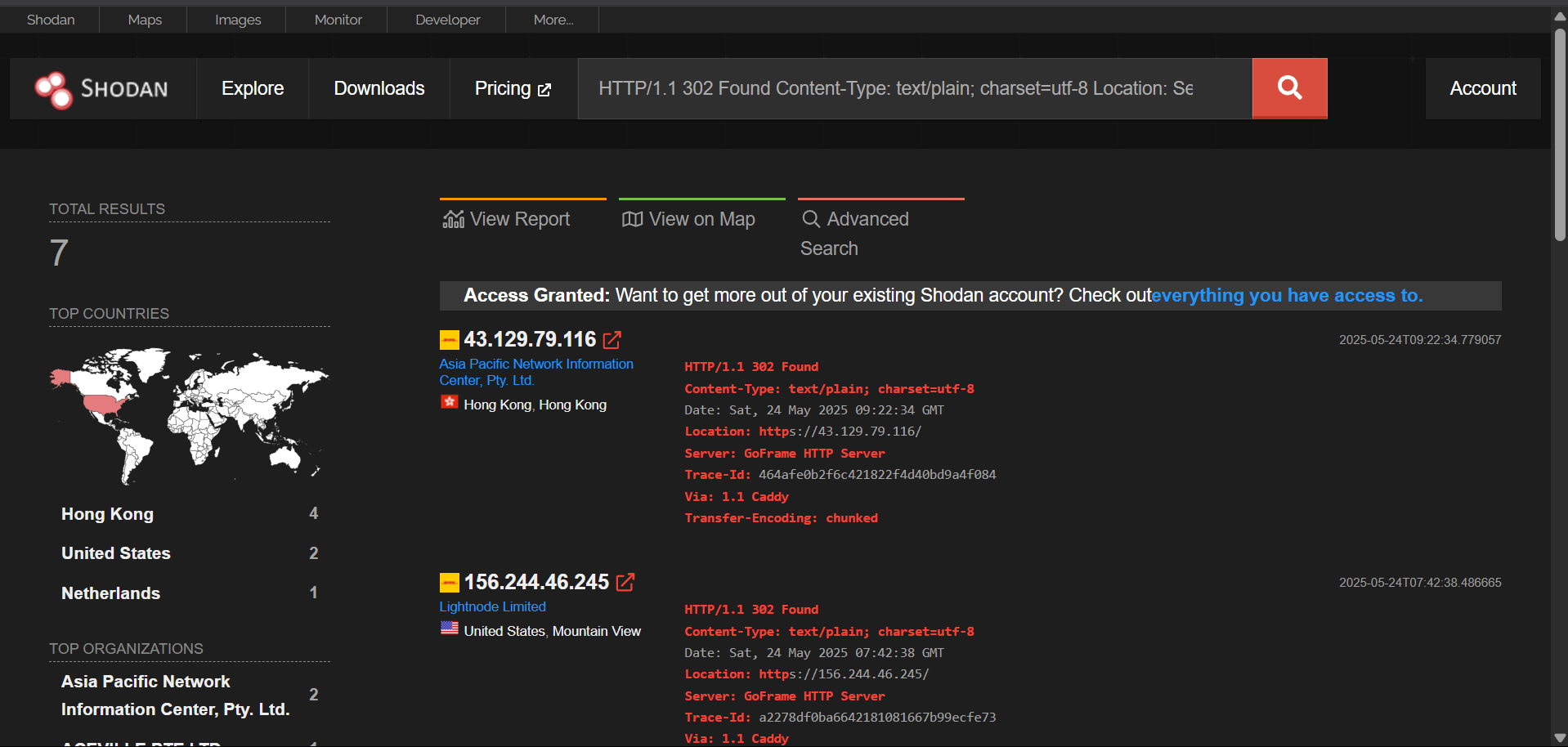
156[.]244[.]46[.]245
156[.]244[.]46[.]73
188[.]119[.]149[.]172
192[.]161[.]163[.]226
192[.]161[.]163[.]227
192[.]161[.]163[.]229
196[.]251[.]117[.]74
196[.]251[.]117[.]87
196[.]251[.]118[.]64
196[.]251[.]69[.]254
196[.]251[.]73[.]115
196[.]251[.]73[.]209
196[.]251[.]80[.]72
196[.]251[.]80[.]82
196[.]251[.]81[.]179
196[.]251[.]81[.]53
196[.]251[.]84[.]192
196[.]251[.]85[.]252
196[.]251[.]87[.]122
212[.]192[.]12[.]13
23[.]95[.]205[.]187
23[.]95[.]205[.]188
43[.]129[.]64[.]147
43[.]129[.]79[.]116
43[.]132[.]221[.]75
43[.]134[.]179[.]198
43[.]135[.]29[.]252
43[.]157[.]24[.]117
43[.]157[.]93[.]30
43[.]160[.]194[.]171
43[.]160[.]204[.]62
43[.]162[.]123[.]226
43[.]165[.]130[.]98
43[.]165[.]63[.]152
47[.]254[.]125[.]247
47[.]89[.]252[.]178
5[.]149[.]250[.]13
91[.]193[.]17[.]85
91[.]245[.]254[.]114
91[.]245[.]254[.]115
91[.]245[.]254[.]79
196[.]251[.]71[.]91
156[.]238[.]225[.]106



