Summary
Recently identified previously undetected Kimsuky (also known as Black Banshee) infrastructure through advanced pivoting techniques. Using HTTP header analysis, SSL Cert and JARM fingerprinting. We uncovered several IPs and domains, many of them were not flagged by VirusTotal at the time of discovery.
Who is APT43 Kimsuky / Black Banshee?
Kimsuky, also known as Black Banshee, is a North Korean state-sponsored APT group active since at least 2012. The group is primarily focused on cyber espionage, targeting organizations related to foreign policy, defense, and national security.
Target Sectors:
Government and defense
Think tanks and research institutions
Media organizations
Nuclear and energy sectors
NGOs and academic entities
Geographic Focus:
South Korea
United States
Europe
United Nations-related organizations
Phishing Tactics:
Spear-phishing with highly tailored lures (often impersonating journalists, scholars, or official entities)
Use of malicious Microsoft Office documents or compressed archives
Embedded macro scripts and remote template injection
Credential harvesting through spoofed login pages and malicious links
Notable Techniques:
Social engineering via email or messaging platforms (e.g., Gmail, Outlook, Telegram)
Use of compromised legitimate infrastructure for C2 communication
Browser data theft and keystroke logging
Abuse of cloud services (e.g., Google Drive) for data exfiltration
Initial Pivot
The initial pivot point for this hunt are IP addresses 158[.]247[.]239[.]225 and 67[.]217[.]62[.]219 as they are attributed to Kimsuky
We will pivot using HTTP header, JARM and Certificate public key
158[.]247[.]239[.]225
HTTP Header:
HTTP/1.1 200 OK
Server: Apache/2.4.46 (Win64) OpenSSL/1.1.1g PHP/7.2.33
X-Powered-By: PHP/7.2.33
Content-Length: 0
Content-Type: text/html; charset=UTF-8
-----------------
JARM 2ad2ad16d2ad2ad22c42d42d0000006f254909a73bf62f6b28507e9fb451b5
-----------------
SSL Cert Key:
Public-Key: (3072bit)
67[.]217[.]62[.]219
HTTP Header:
HTTP/1.1 200 OK
Server: Apache/2.4.58 (Unix) OpenSSL/1.1.1w PHP/8.0.30 mod_perl/2.0.12 Perl/v5.34.1
X-Powered-By: PHP/8.0.30
Content-Length: 19
Content-Type: text/html; charset=UTF-8
Building Rules
This is the rule that we will use in shodan (with and without ssl.jarm)
ssl.jarm:2ad2ad16d2ad2ad22c42d42d0000006f254909a73bf62f6b28507e9fb451b5 HTTP/1.1 200 OK Server: Apache/2.4.46 (Win64) PHP/7.2.33 X-Powered-By: PHP/7.2.33 Content-Length: 0 Content-Type: text/html; charset=UTF-8 ssl:3072
HTTP/1.1 200 OK Server: Apache/2.4.58 (Unix) OpenSSL/1.1.1w PHP/8.0.30 mod_perl/2.0.12 Perl/v5.34.1
X-Powered-By: PHP/8.0.30 Content-Length: 19 Content-Type: text/html; charset=UTF-8
Validating Results
1. 38[.]54[.]50[.]57 –> 0/94 detection
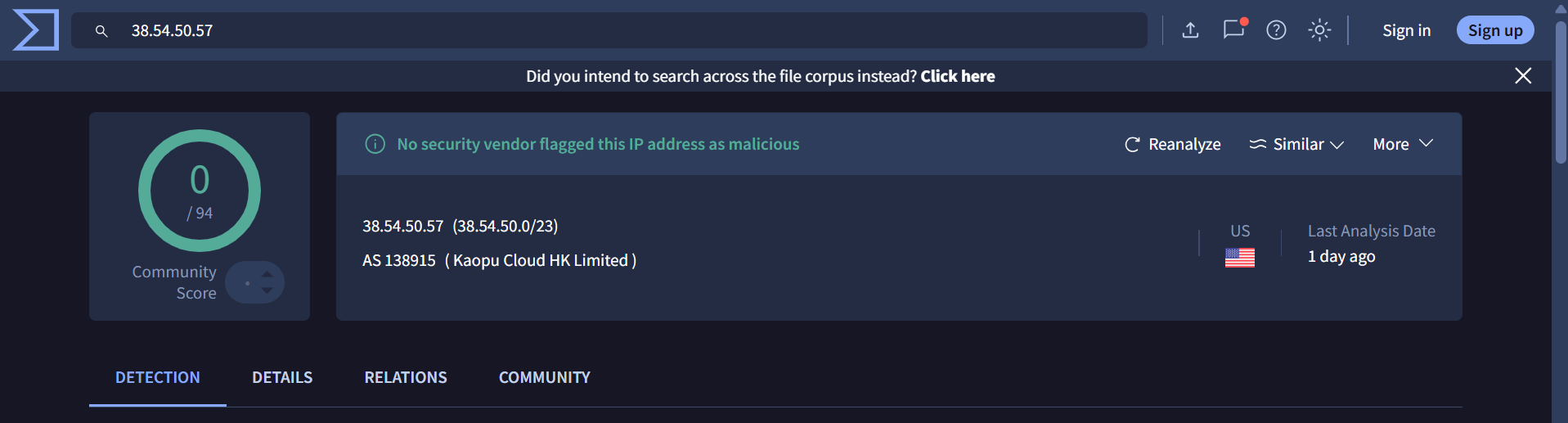
This IP resolves to phishing domains impersonate legitimate organizations and companies
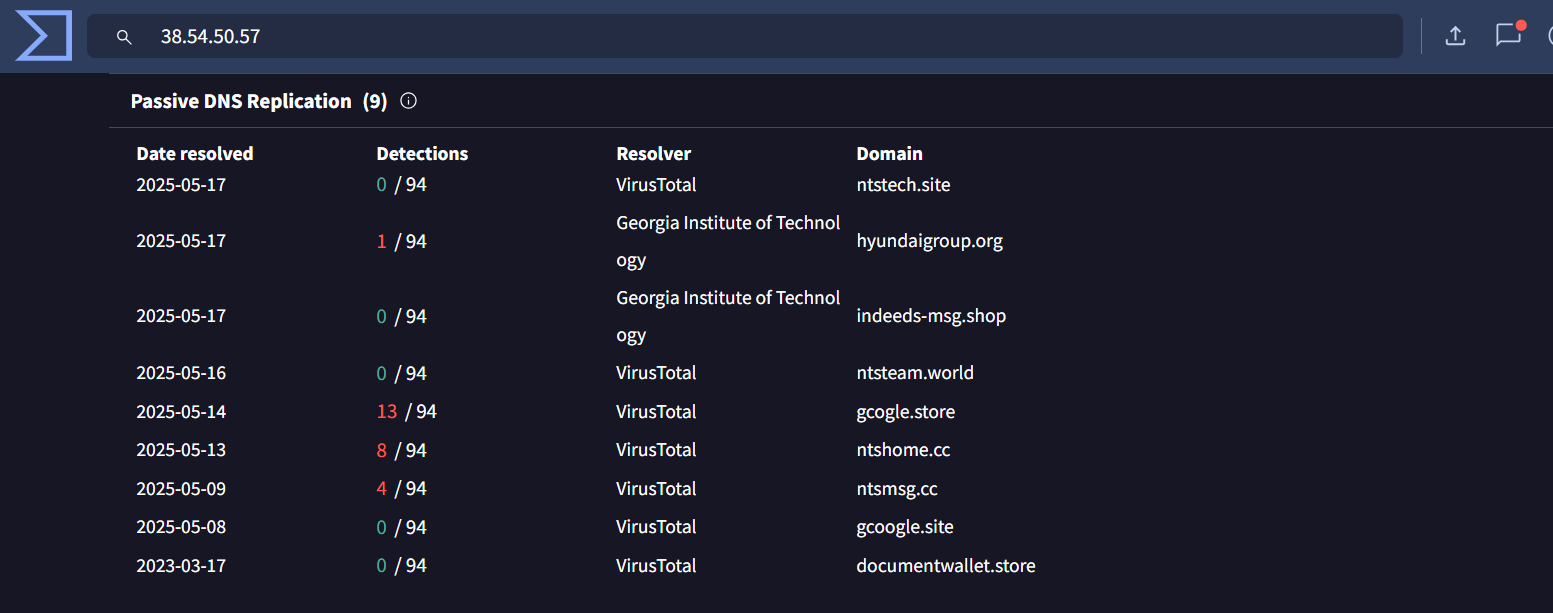
These domains are similar to the domains resolved by the initial IP
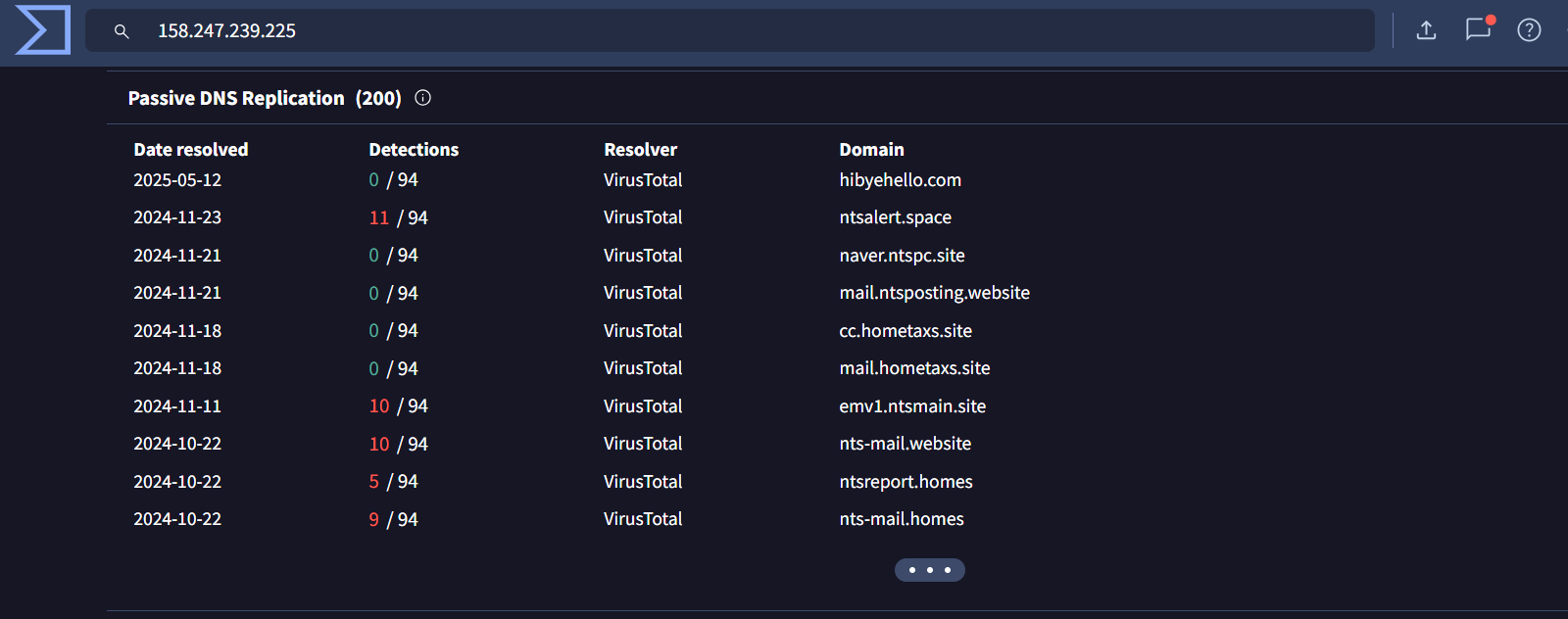
By pivoting on each domain we got another 2 IPs
156[.]244[.]19[.]218 –> 1/94
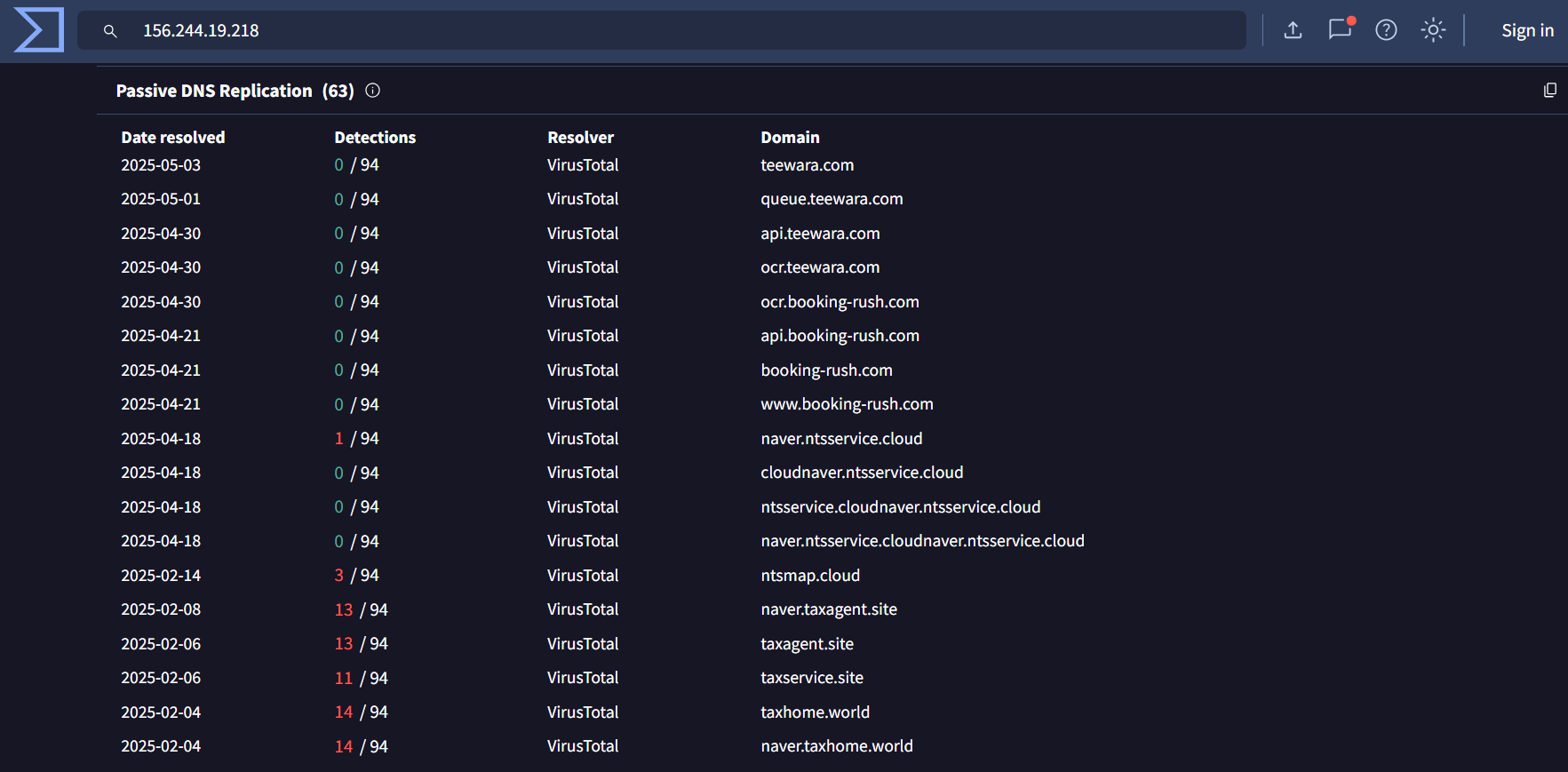
Impersonation of Naver & Cloud Services, travel-related services
91[.]195[.]240[.]123 –> 9/94

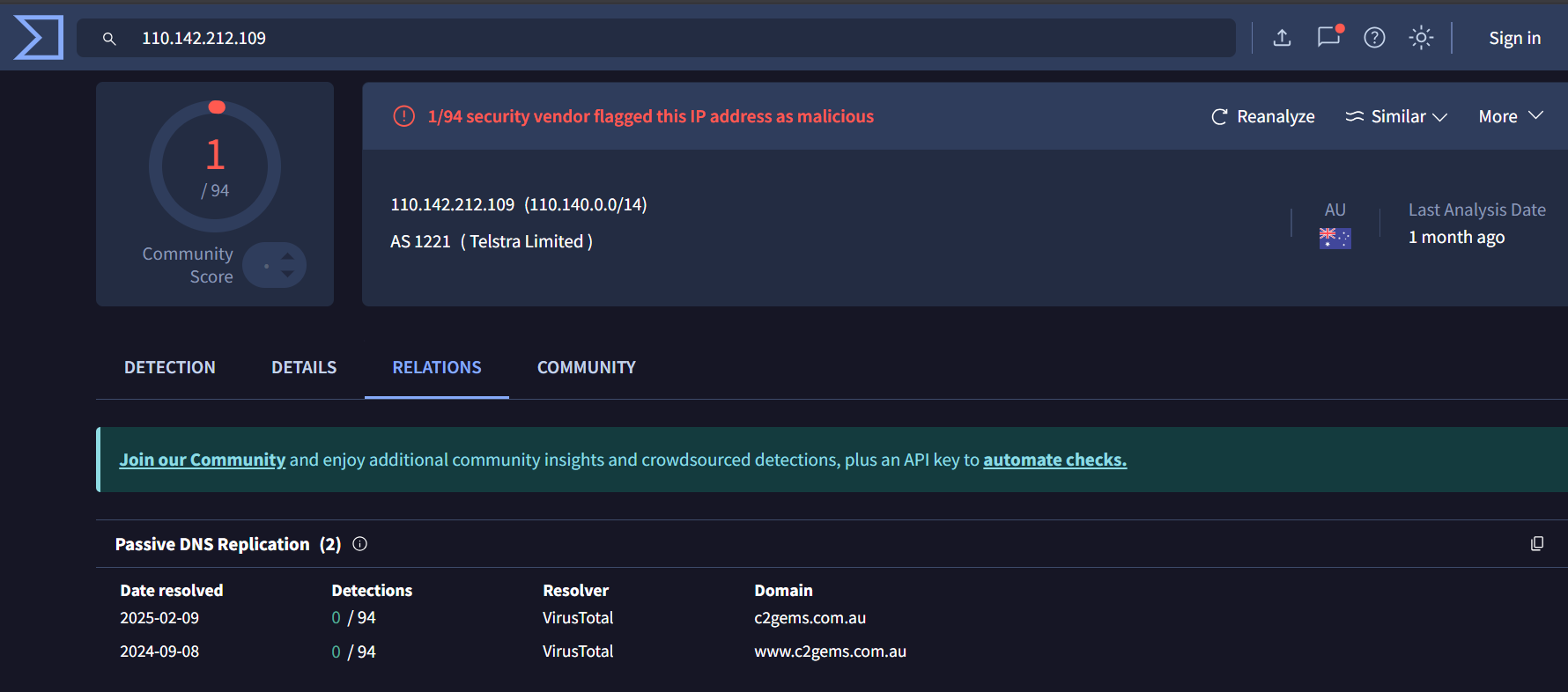
2. 110[.]142[.]212[.]109 –> 1/94
This IP resolves c2gems[.]com[.]au which impersonates C2G’s Energy Management System
3. 95[.]196[.]78[.]150 –> 0/94
The IP resolves va-teknik[.]nu domain
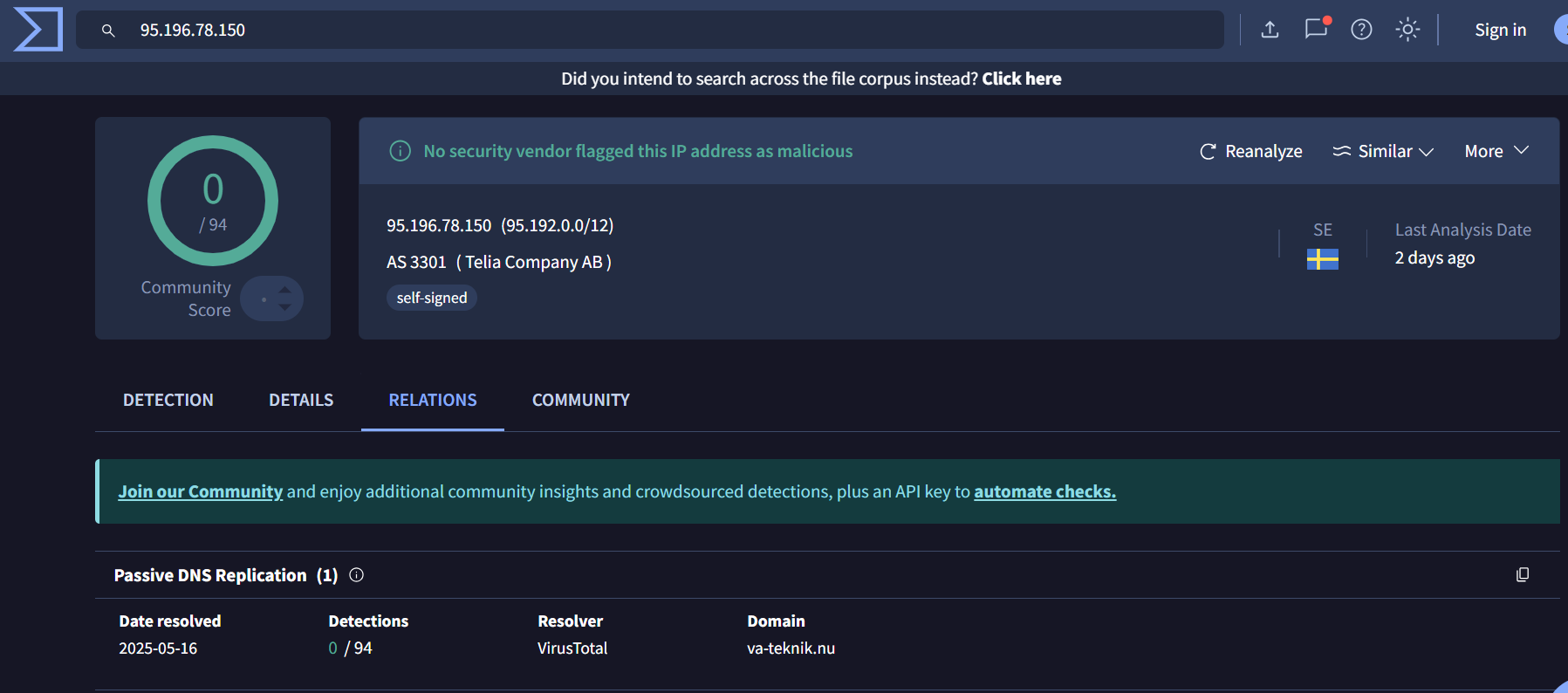
In Sweden, VA-Teknik refers to municipal water and wastewater services managed by the local government

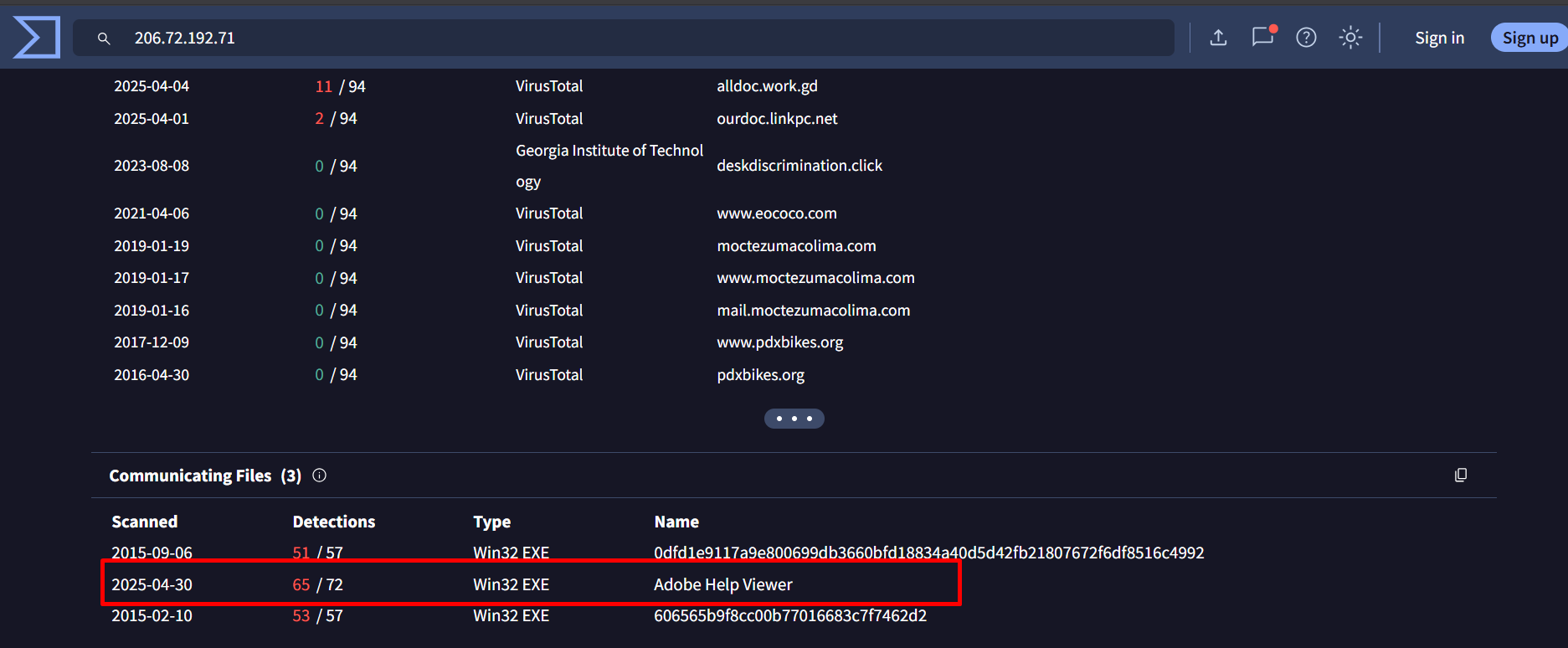
4. 206[.]72[.]192[.]71 –> 0/94
5. 162[.]220[.]11[.]84 –> 0/94
This IP resolves
all[.]bodysh[.]p-e[.]kr
mis[.]patriot[.]p-e[.]kr
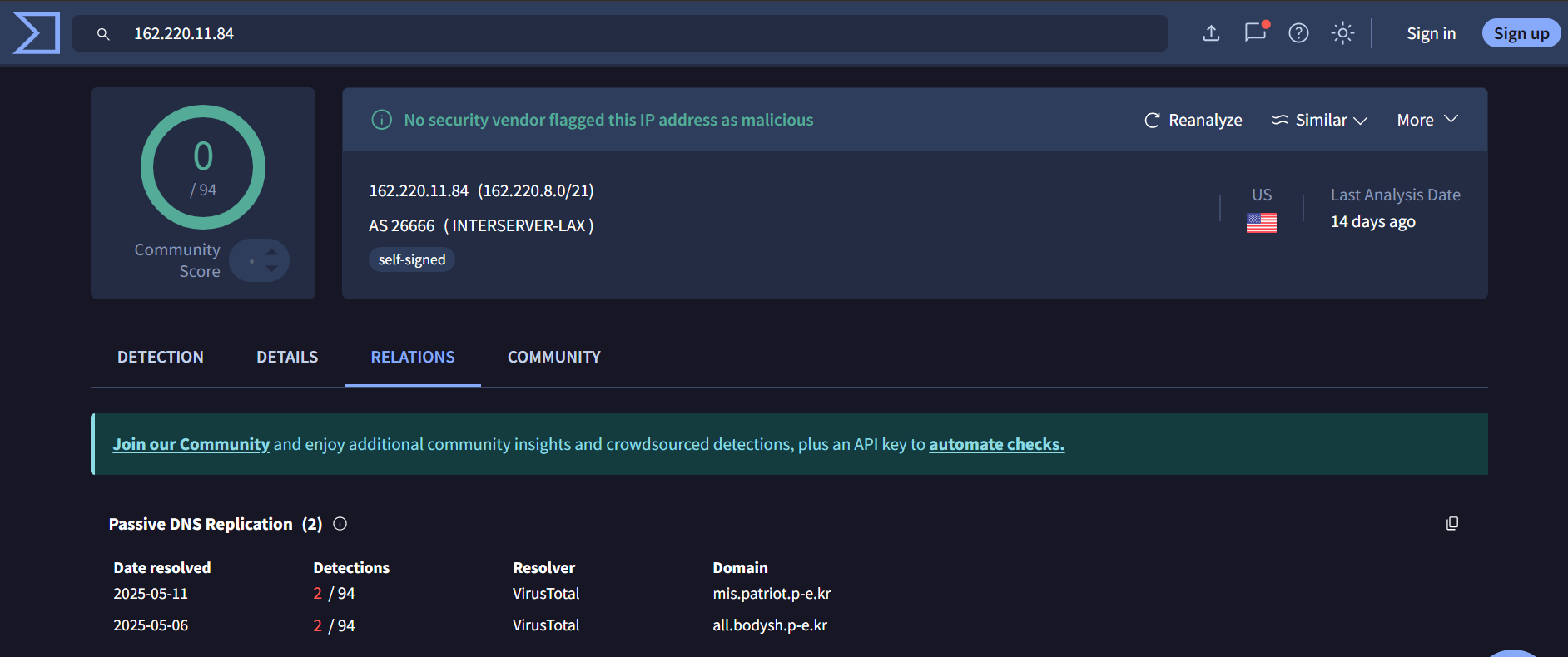
p-e[.]kr domain is used in Kimsuky campaign
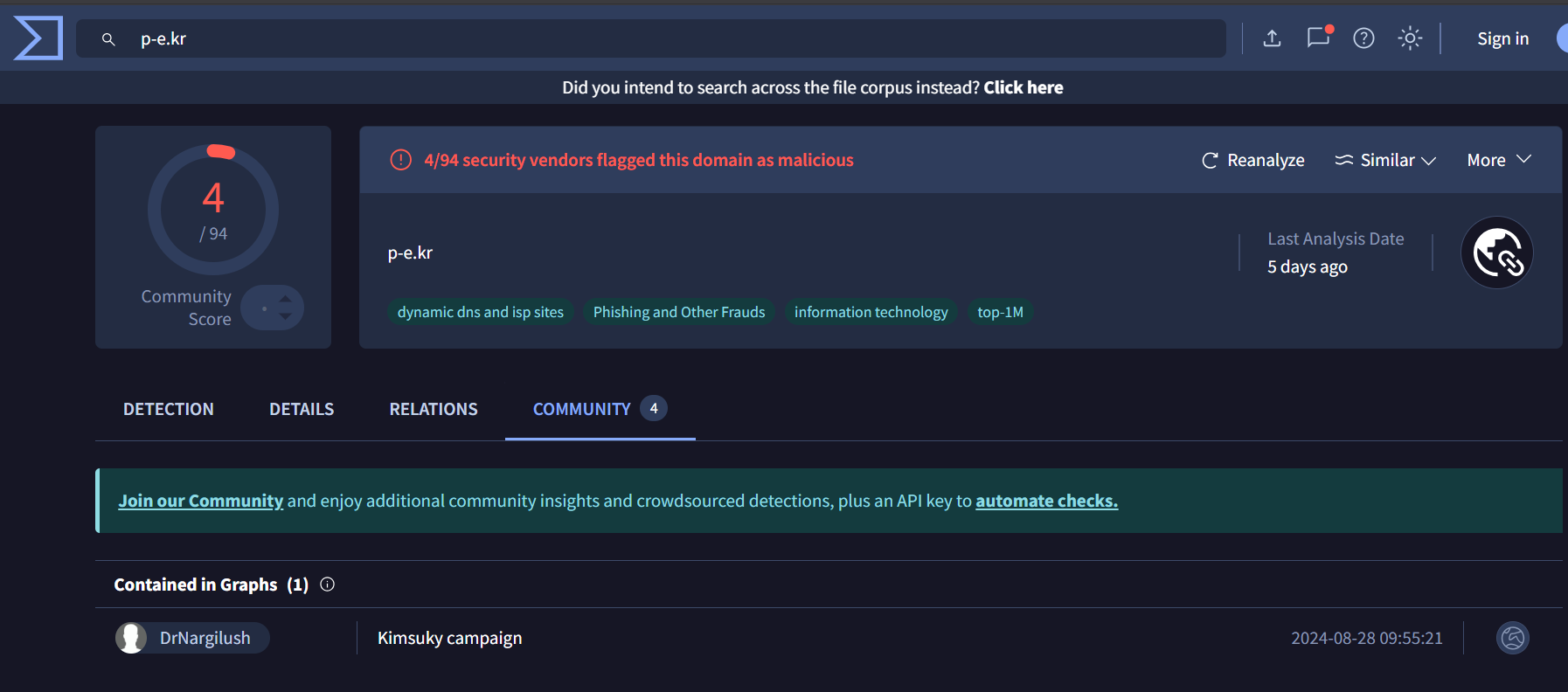
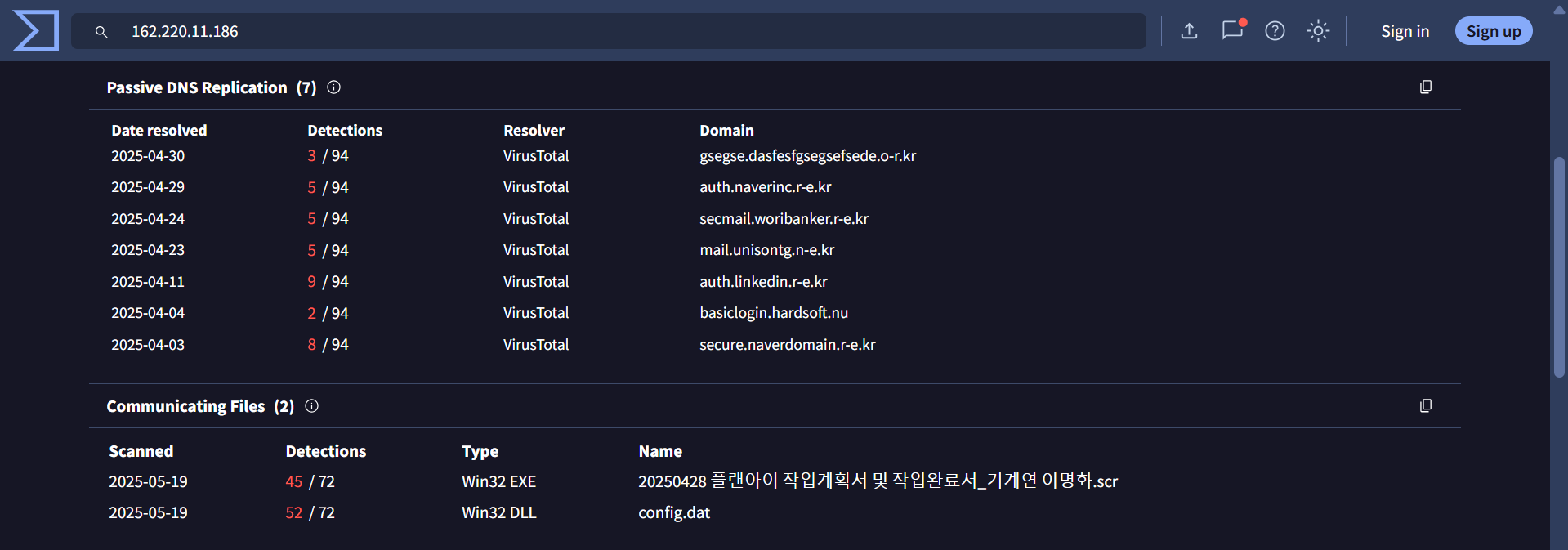
6. 162[.]220[.]11[.]186 –> 3/94
The IP address resolves to phishing domains impersonating legitimate companies. It is also associated with a file named in Korean:
“플랜아이 작업계획서 및 작업완료서_기계연 이명화” (translated: Plan-i Work Plan and Completion Report – Lee Myunghwa, Mechanical Research).
기계연 is an abbreviation for 기계연구원 (Korea Institute of Machinery & Materials), The file is created to target or impersonate a South Korean research institution
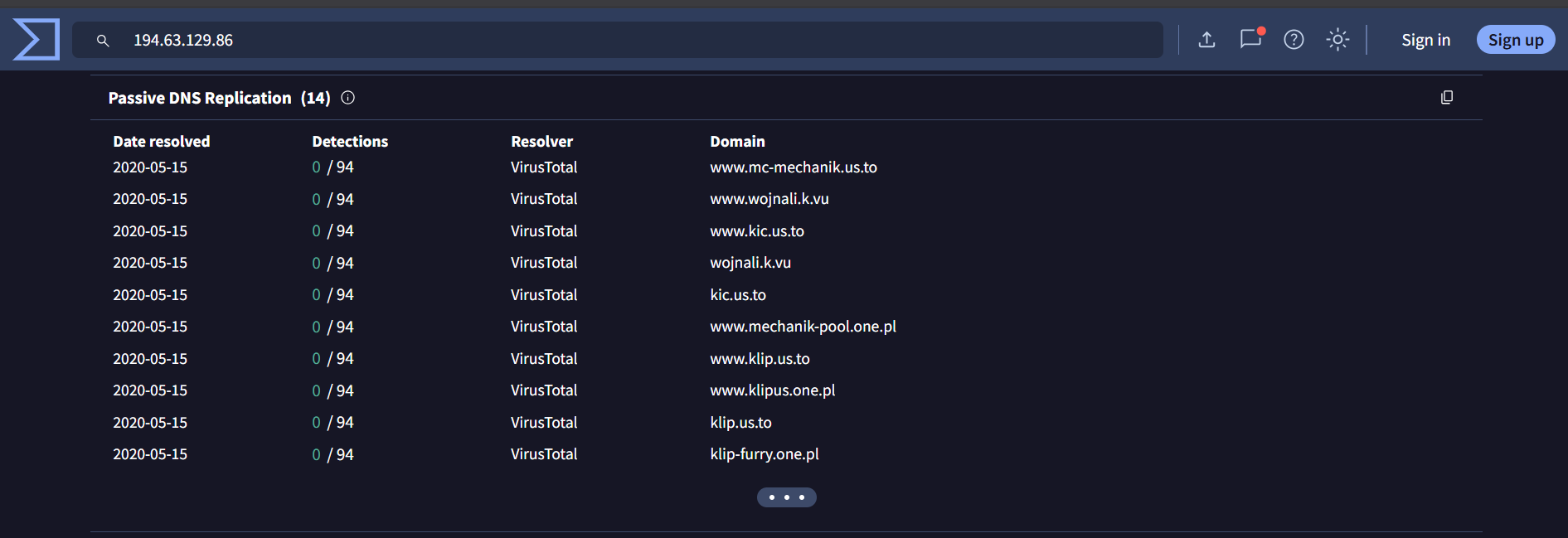
7. 194[.]63[.]129[.]86 –> 0/94
us[.]to domain is used in Kimsuky campaign
8. 3[.]89[.]115[.]251 –> 0/94
IP resolves to plesk[.]page domains
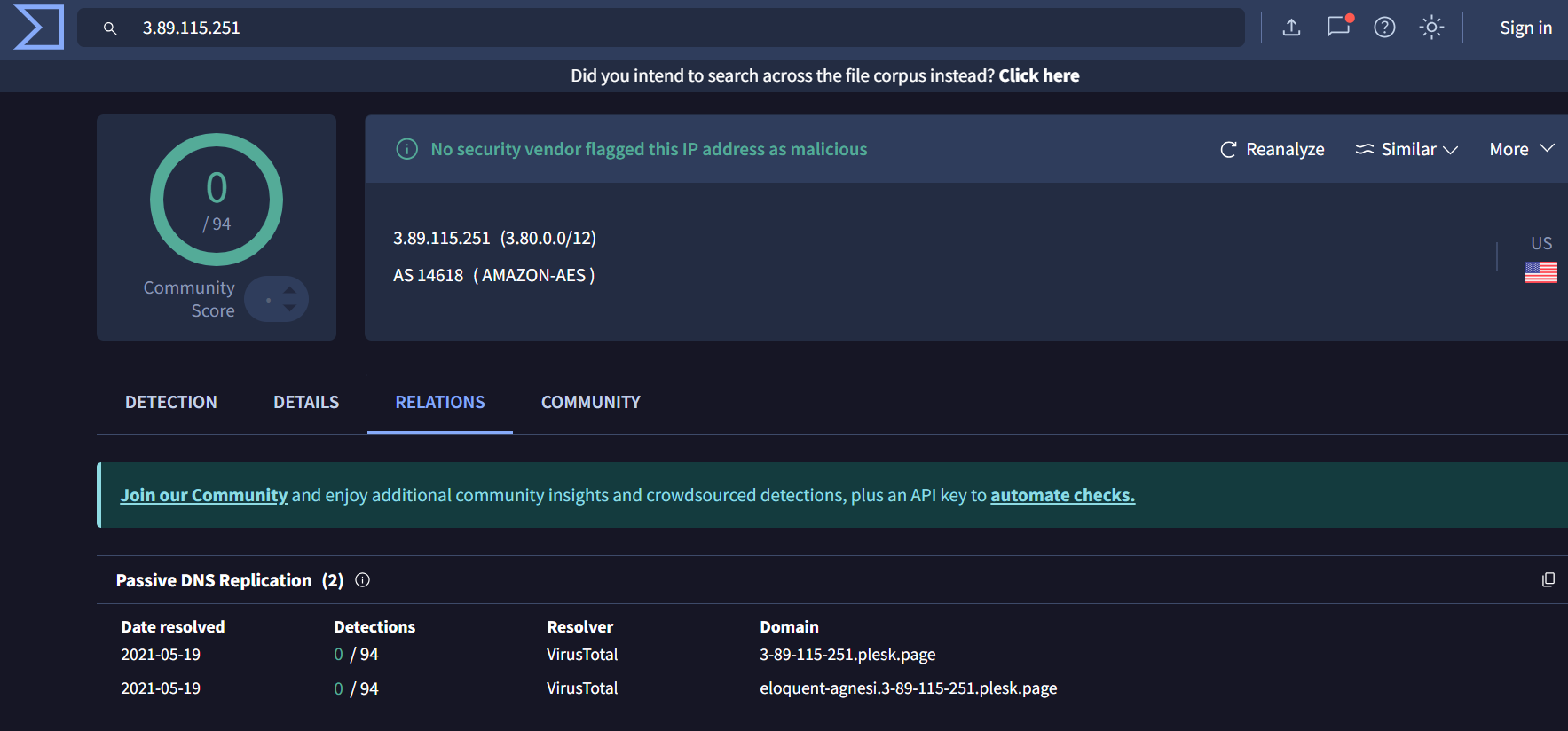
According to this tweet https://x.com/skocherhan/status/1920076871418413139
plesk[.]page domain is related to Kimsuky
Low Confidence Infrastructure
1. 124[.]40[.]247[.]67 –> 0/94
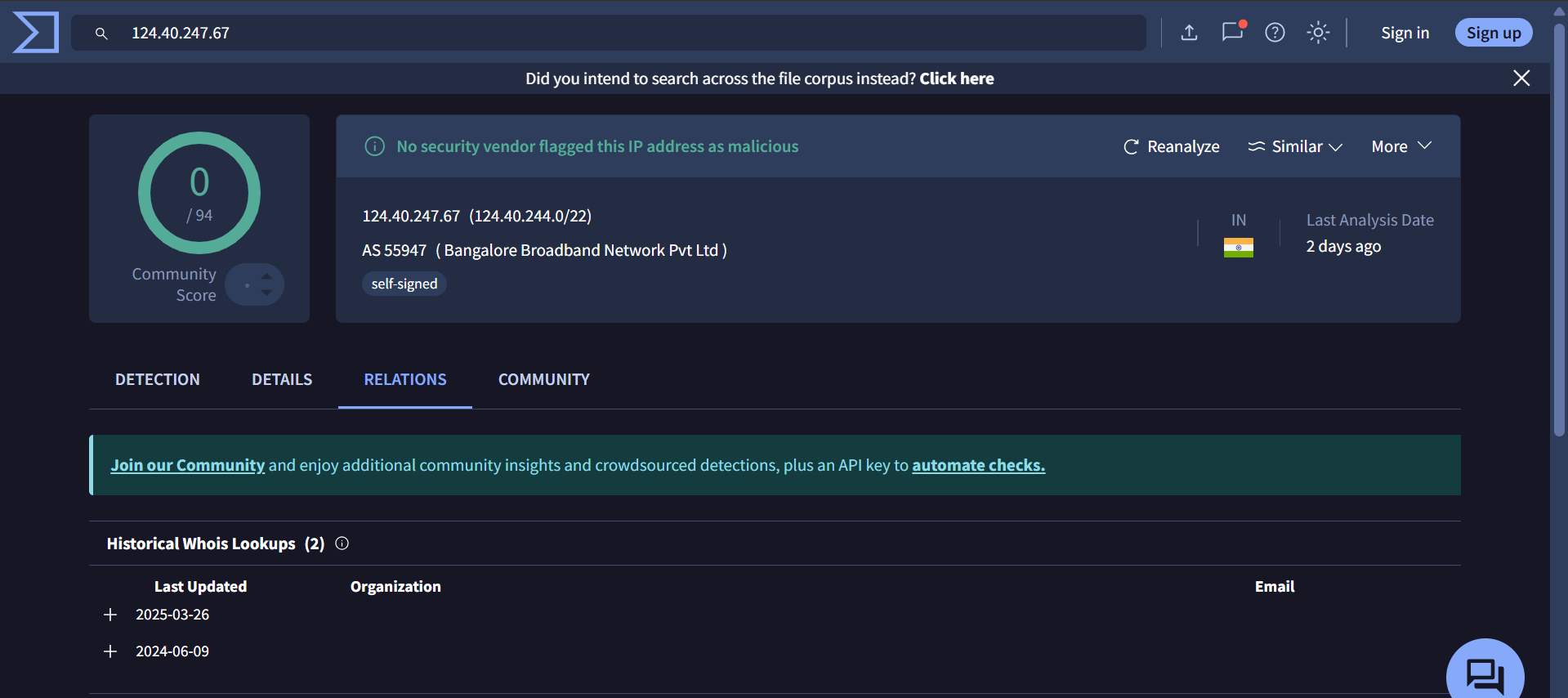
This IP doesn’t resolve any domains, so I searched with the IP in google and I found that it is mentioned in Ewit – East West Institute of Technology website hosted on ewit[.]edu[.]in domain
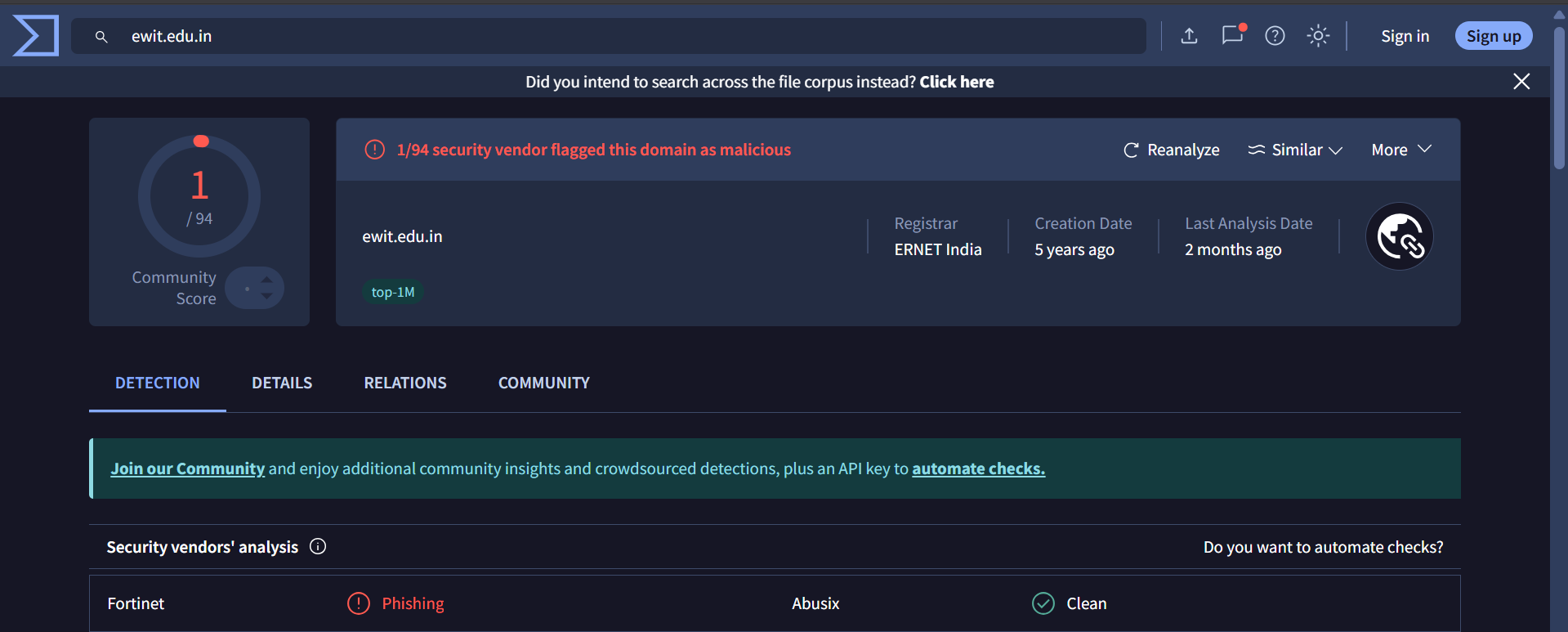
This domain is flagged by Fortinet as phishing
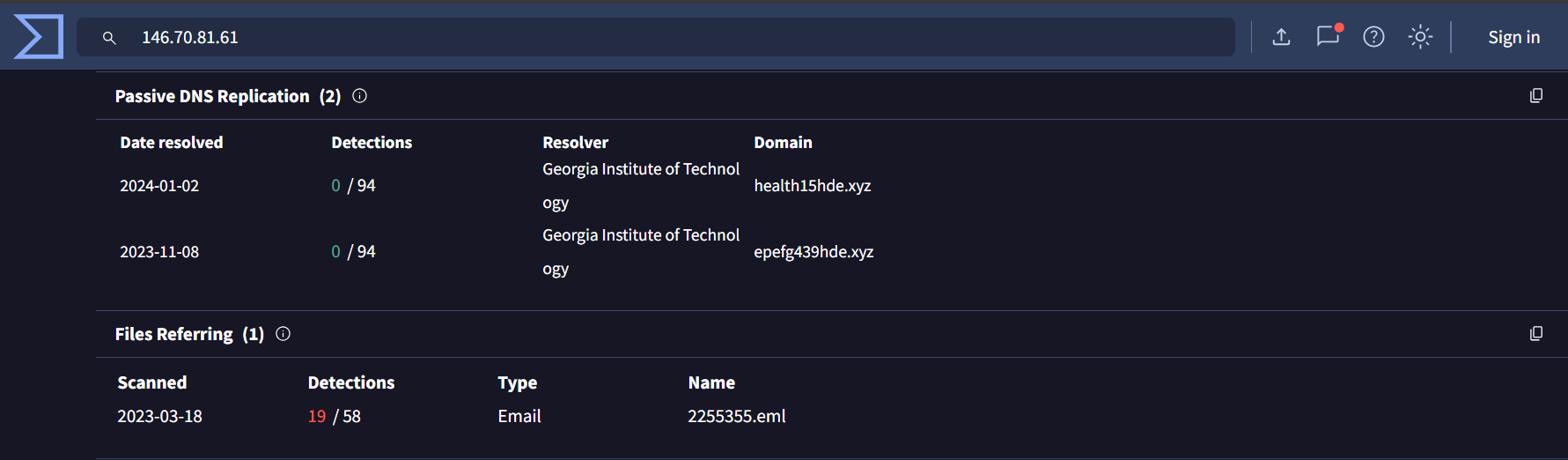
2. 146[.]70[.]81[.]61 –> 0/94
This IP resolves health15hde[.]xyz domain which impersonate health organization. Also the IP is associated with a malicious email
3. 222[.]73[.]105[.]195 –> 0/94
First domain is hosting a recruitment site for Shanghai Equivalent Computer Technology Co., Ltd.
This site is impersonating a Chinese B2B or B2C e-commerce or data aggregation company
There are 2 malicious files related to that IP, both of them has Chinese Highlighted Text.
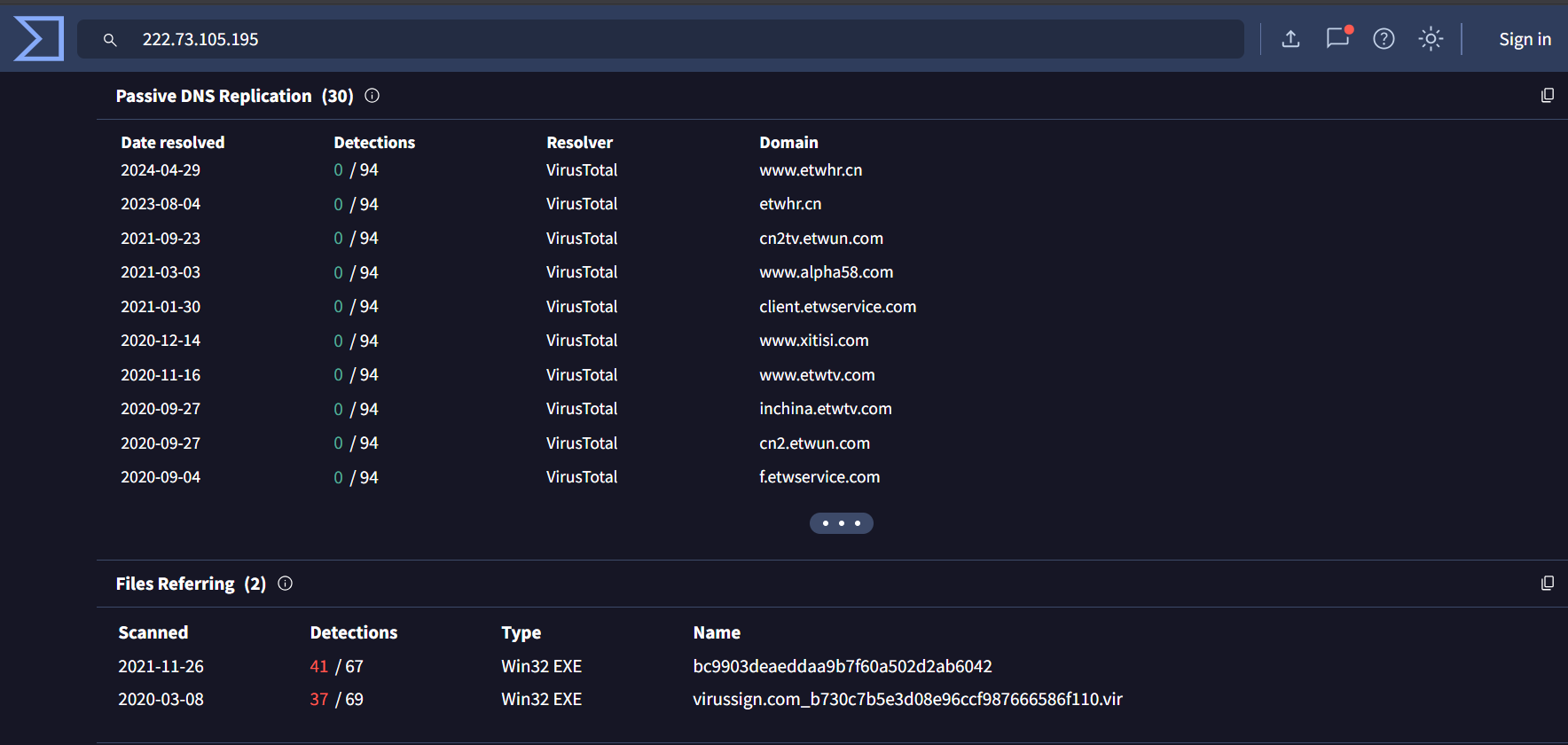
This text is translated to “The Yunda client patch has been installed successfully! Press Enter to close!”
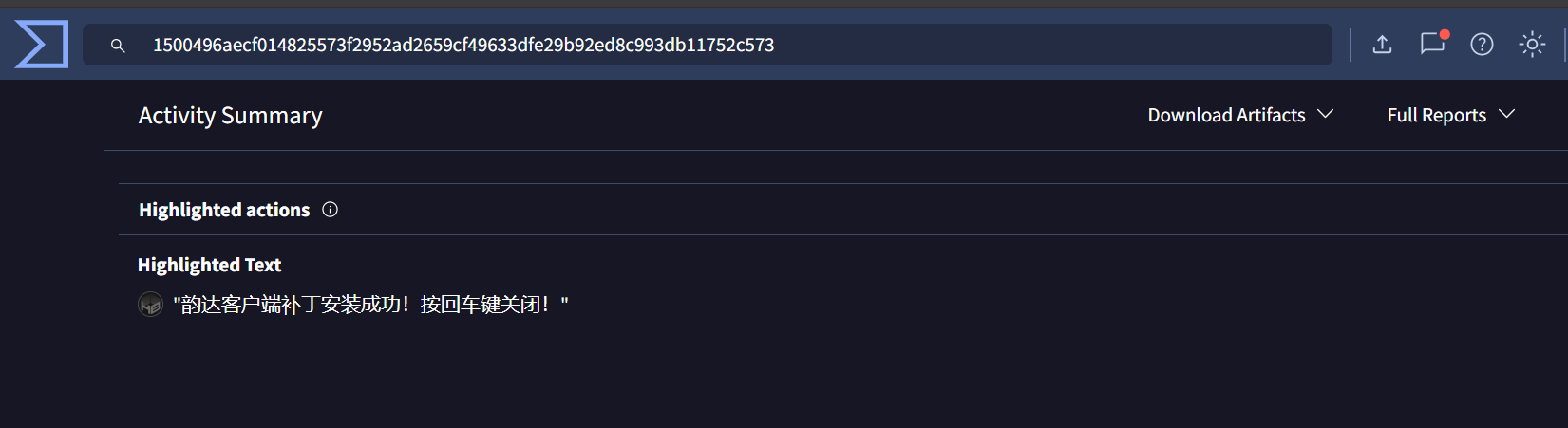
Yunda may refer to Yunda Express which is one of the major courier and logistics companies in China.
So it maybe impersonates Yunda Express
4. 91[.]210[.]106[.]42 –> 0/94
The IP resolves to domains contain “video.ru”
The IP is associated with a pdf file
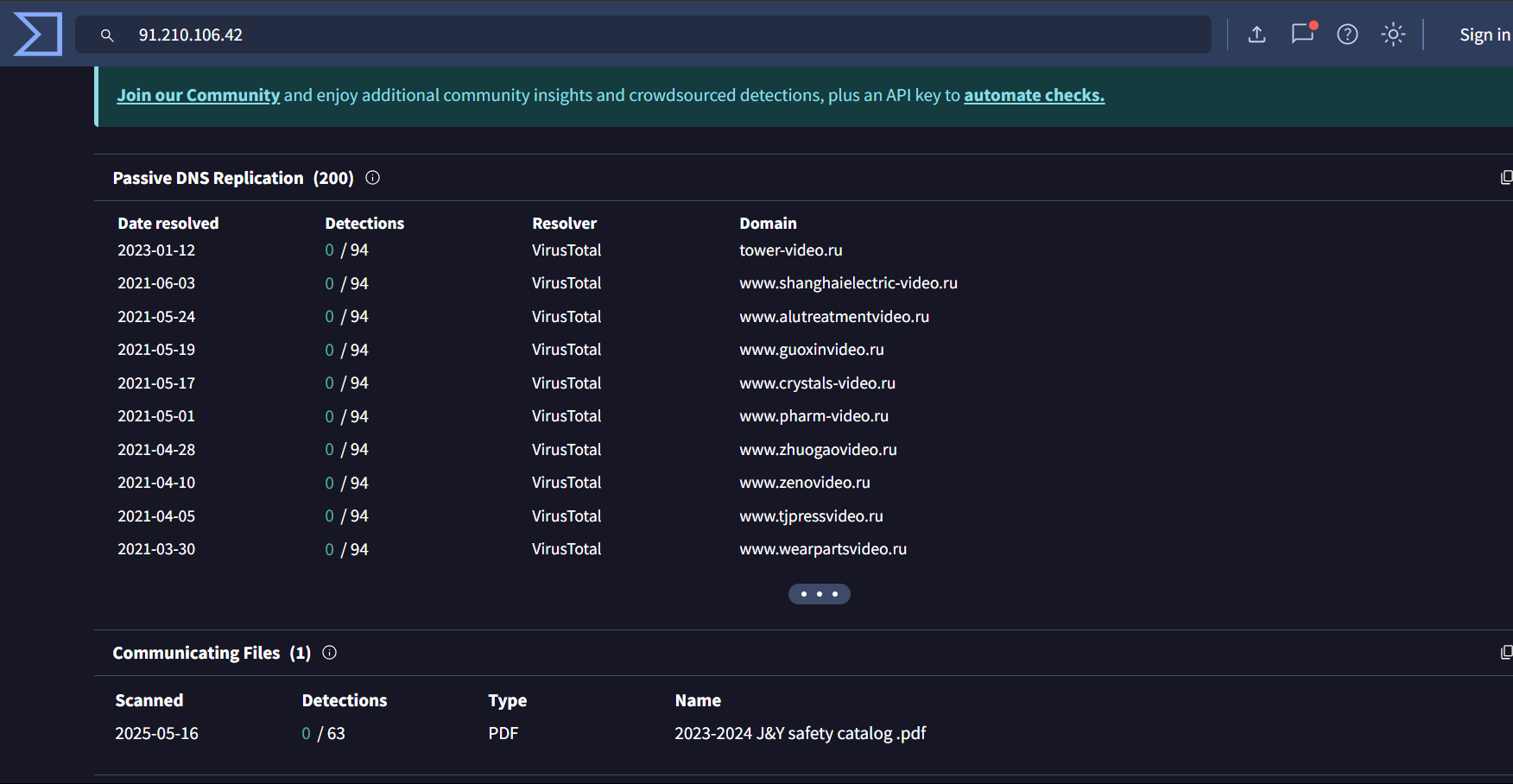
The pdf file contacts malicious IPs
IOCs
158[.]247[.]239[.]225
38[.]54[.]50[.]57
156[.]244[.]19[.]218
91[.]195[.]240[.]123
206[.]72[.]192[.]71
95[.]196[.]78[.]150
110[.]142[.]212[.]109
162[.]220[.]11[.]84
162[.]220[.]11[.]186
194[.]63[.]129[.]86
3[.]89[.]115[.]251
91[.]210[.]106[.]42
teewara[.]com
queue[.]teewara[.]com
api[.]teewara[.]com
ocr[.]teewara[.]com
ocr[.]booking-rush[.]com
api[.]booking-rush[.]com
booking-rush[.]com
naver[.]ntsservice[.]cloud
cloudnaver[.]ntsservice[.]cloud
ntsservice[.]cloudnaver[.]ntsservice[.]cloud
naver[.]ntsservice[.]cloudnaver[.]ntsservice[.]cloud
gcogle[.]store
ntsteam[.]world
ntshome[.]cc
ntsmsg[.]cc
gcoogle[.]site
c2gems[.]com[.]au
all[.]bodysh[.]p-e[.]kr
mis[.]patriot[.]p-e[.]kr
us[.]to
k[.]vu
one[.]pl
3-89-115-251[.]plesk[.]page
eloquent-agnesi[.]3-89-115-251[.]plesk[.]page
------------------
Low Confidence
------------------
146[.]70[.]81[.]61
124[.]40[.]247[.]67
222[.]73[.]105[.]195
91[.]210[.]106[.]42
health15hde[.]xyz
ewit[.]edu[.]in



